- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- Cloud Network Security
- :
- Discussion
- :
- Want to see real client Public IP at my backend se...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Want to see real client Public IP at my backend servers. Allow gateways to add X-forwarded-for field
Please help me with this. How to achieve seeing Clients Real Public IP at my backend servers allowing gateways to pass Public IPs through.
~My Network Flow when client tries to open a URL over the internet (Accessing a web page): -
Client --> Internet --> Azure Load balancer (Layer4) --> Cloud Guard IaaS Cluster HA(A-P) R80.30 --> Azure Application Gateway(Layer 7) --> Web Apps (Azure App Services)/Servers
In this architecture I am able to see Clients real Public-IP till the Firewall logs only.
~What I want to achieve: -
I need the same public IP to be seen at the Azure Application Gateway(Layer 7). Which at the moment I am seeing firewalls internal Translated Source IP (Private IP) for each and every request.
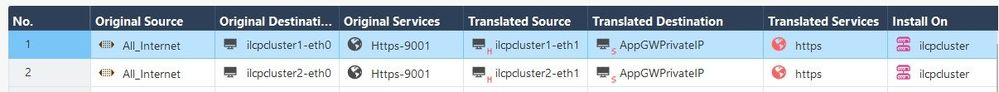
This is the Application Gateway(Layer 7) logs where I am seeing IP as "clientIP:10.0.11.10" which is my Check Point gateways eth1/port2/internal port. Instead of this I should get real clients public-IP.
~As a knowledge: -
I am using NAT here where All internet as a Original Source gets converted to Gateways port2/eth1 (Hide behind NAT) as Translated Source
~Once I am able to see the public IP at Azure Application Gateway(Layer 7), the work is done here.
BR
Amarpreet Singh
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |
Thu 09 May 2024 @ 05:00 PM (CEST)
Under the Hood: Automate Azure Virtual WAN security deployments with Terraform