- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- Cloud Network Security
- :
- Discussion
- :
- Inspecting and detecting original source address o...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Inspecting and detecting original source address of TCP NLB inbound traffic
Hello,
I have a AWS TCP Network Load Balancer with proxy protocol v2 enabled. This LB routes the traffic to a logical server IP with a group of internal web servers. The ports it use are 30080 and 30443, configured as TCP service with HTTP/S protocol but it seems that IPS are not inspecting this traffic.
Futhermore, I can see the real client IP address in the web server's log, so it seems proxy protocol are working, but in the Checkpoint log I only see the internal LB addresses so I can not differentiate between real traffic and LB health check traffic.
I appreciate any kind of suggestion or hint.
Thank you, regards!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
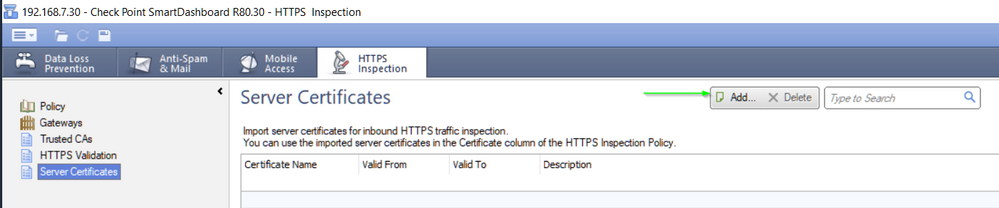
For HTTPS, you may have to add server cert to the Check Point:
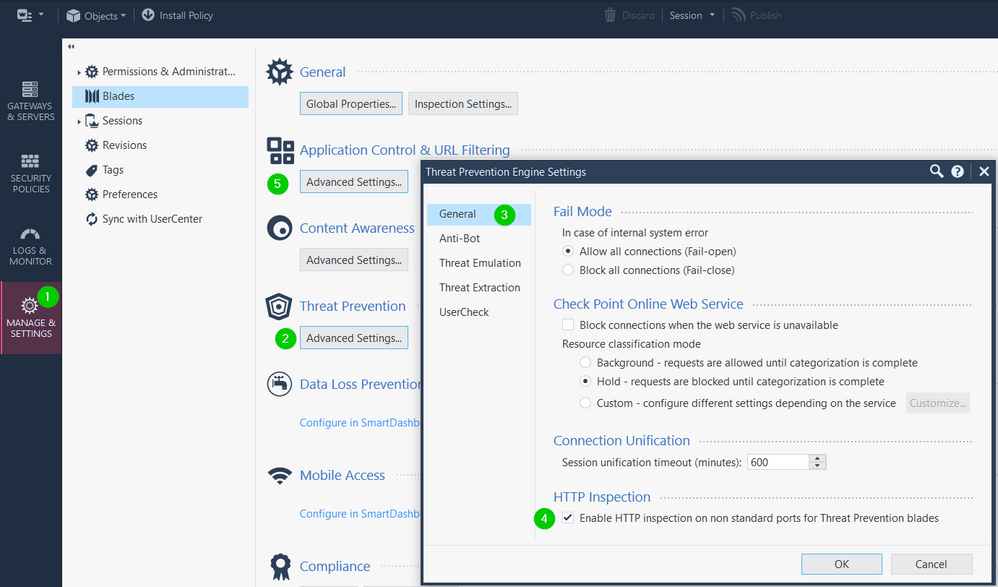
and for HTTP, it should work by default, but just in case it is different in AWS, check the "Non-standard ports" setting here:
and in App Control URLF Advanced Settings.
Also, take a look at this thread, perhaps it could be helpful for pinning down the real traffic:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@PhoneBoy , thanks for pointing it out: got one of those errors when pasting into the post, but it allowed the process to complete sans the URL.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Vladimir, thank you for your help.
I ve checked the "non-standard port" setting and it is enabled in both blades.
I'm checking the IPS with this URL that triggers the "web server exposed git repository..." protection:
http://{public-ip}/.git/config
When I put a web server public IP address the IPS works, prevent the connection and creates a log.
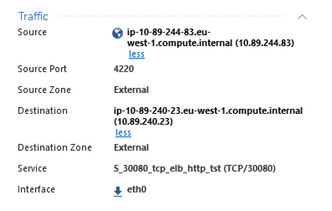
When I put the LB public IP address nothing is detected. I can see it in the checkpoint log with the LB internal IP address as a source and the connection reaches the web server.
I have read the thread as well and confirmed that the proxy protocol are enabled in the LB. The real source IP appears correctly in the web servers behind the logical servers, but in Checkpoint log:
Currently, the 10.89.240.23 is a logical server. I will change it for a host object and check if it affects in some way.
I will uptade this thread with the results.
Regards!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Checked with host object instead of logical server but nothing changes. The IPS does not apply the protections and still appears the LB internal address as a source address in the tracker.