- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- Cloud Network Security
- :
- Discussion
- :
- How does CloudGuard controller makes your life eas...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How does CloudGuard controller makes your life easier?
The first Check Point cloud controller connector was released around 2 years ago to transform the way we consume objects in security policies and opening a revolutionary new security model for designing and operating policies with an automated and zero-touch approach that helps security practitioners focusing on analyzing security events and improving security postures and designs instead of performing basic operational tasks.
Since that first release a number of new features and connectors have been added so that almost any organization today can leverage this functionality (for free by the way). In the past months I have met a number of customers sharing with me different use cases enjoying this function in multiple ways to improve their day to day security challenges. I realized it could be very interesting for the community to share how each setup is leveraging CloudGuard Controller so I invite you to share your use case in this thread explaining how the organization you work with enjoys this function. I will start by sharing the policy I use as an example on how to leverage it:
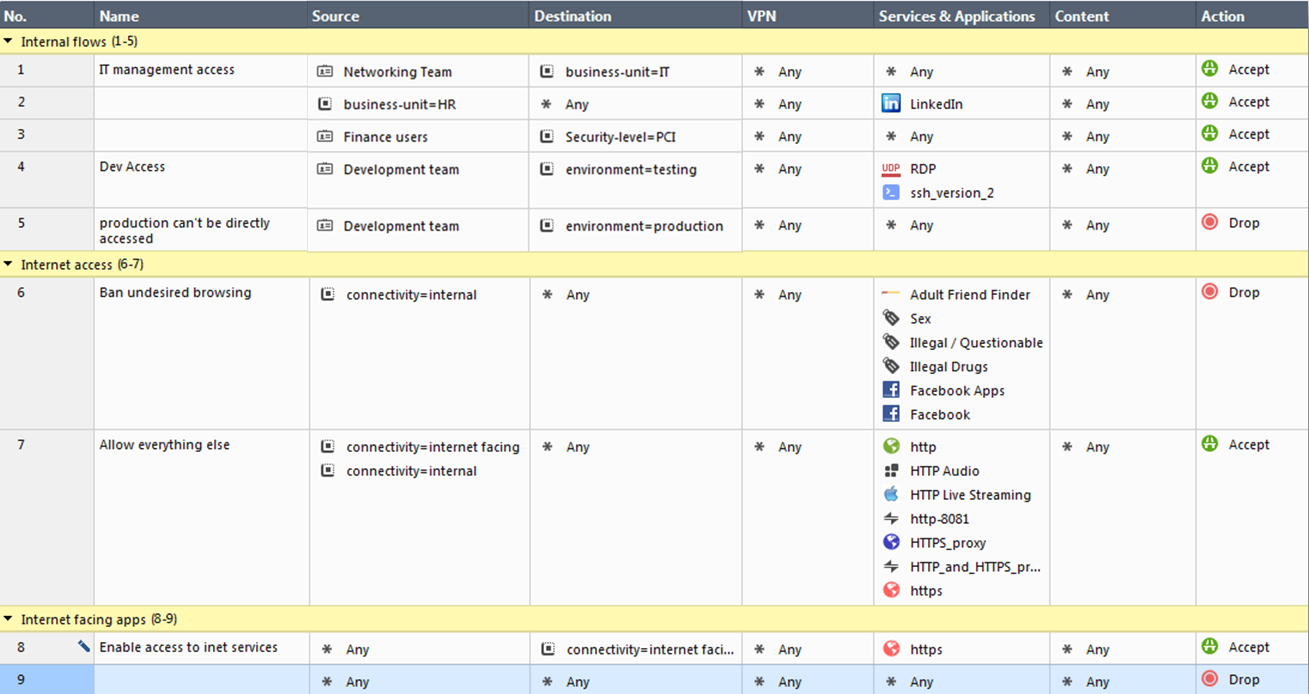
The example above protects a hybrid infrastructure with on-prem, azure and aws environments where each and every asset has been previously tagged according to the security needs. Any new application that is for instance ruled by PCI requirements only needs to be use the "PCI" tag in order to be automatically added with the right access and protection without modifying or reinstalling the policy above.
What is your use case?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great post. What is the name of the type of object you have for the tagged VMs such as "connectivity-internal"? Dynamic objects?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The Cloudguard is a very helpful feature.
the introduction of datacenter object based on TAGS even in vCenter (no NSX) by R80.20M2 will make easier making a rule base configuration in response to the infrastructure team, that will deploy VMs, and they need.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm trying to convince our team to use Cloudguard for Azure but they still say it is not fast enough with updates. They say it takes to long before updates for nodes with Tags are done with the firewalls. What is the time frame for sync?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi HooftG,
The CloudGaurd Controller has a sleep time of 30 between each cycle.
You can reduce the sleep time between each cycle, as it's a configurable parameter, but depending on the rest of your environment you run the risk of the cloud vendor throttling you if you exceed their API call limit.
I'm assuming that you don't mean that 30 seconds is too long and that for some reason changes take longer to propagate in your environment.
If you are seeing delays, it might be something worth looking into - for example it could be related to what I mentioned above and that your environment has multiple elements which are sending API calls causing Azure to throttle your connection and making many API calls fail,
I've seen a similar case where a customer had a malfunctioning 3rd party asset which was spamming Azure and causes severe delays in updates as a result.
Obviously the above is just one possible explanation and might not be relevant in your case.
It might be beneficial to run some empirical tests - import a tag into your policy, make a change in Azure and check how long it takes for the change to appear in your dashboard.
HTH
Yonatan


