- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- Cloud Network Security
- :
- Discussion
- :
- CloudGuard Network Security Use Case: Remote Acce...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CloudGuard Network Security Use Case: Remote Access VPN for Azure Virtual WAN
As you may already be aware, Check Point CloudGuard Network Security announced its integration with Azure Virtual WAN and specifically the new Routing Intent feature recently.
This new integration allows for simplified security insertion for all of your Azure connected traffic. Virtual WAN allows customers to quickly connect VNETs, Site-to-Site VPN, Point-to-Site VPN, and ExpressRoute spokes which allows them to communicate without the manual effort required previously. CloudGuard Network Security sits inside Virtual WAN and allows customers to secure that same traffic with a few simple clicks. You can be up and running in under 30 minutes.
- Easy-to-deploy – It takes under 30 minutes to deploy CloudGuard inside your Azure Virtual WAN hub. If you have are already using Check Point management, you can easily connect the new deployment. If not, it’s easy to use Check Point’s management-as-a-service solution.
- Easy-to-configure – The best practices configuration is automatically deployed for you. Advanced configurations may be applied using the UI or APIs.
- Easy-to-scale – The security gateways deployed into your Virtual WAN support dynamic changes in your traffic capacity (up to the maximum capacity you defined when creating the Azure Virtual WAN).
- Easy-to-consume – You pay for what you consume based on throughput only, transacted on Azure Marketplace.
- Easy-to-maintain – There are no resources to manage on your Azure account. Upgrading and updating the security gateways are simply “rip and replace”.
Building on top of this announcement is to demonstrate the many different use cases available with this integration.
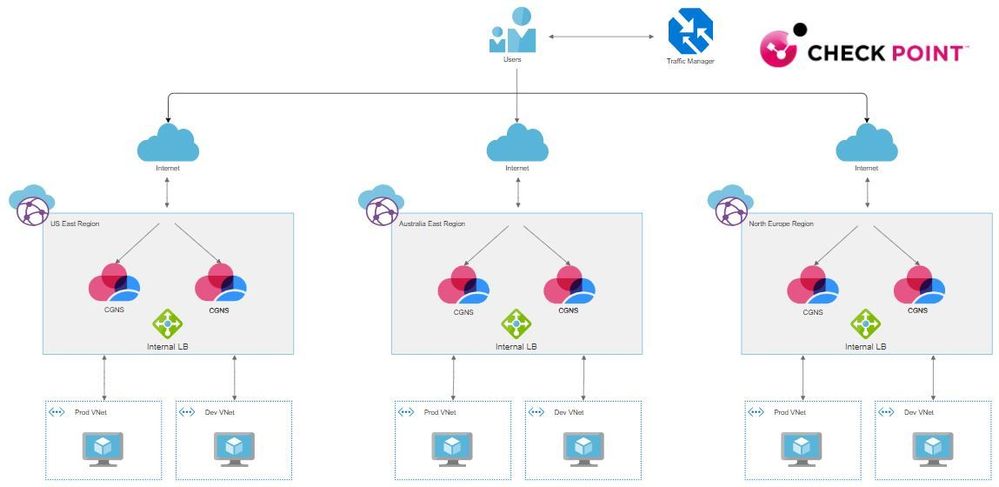
In this case we will be talking about Remote Access VPN. What's the big deal you ask?
- Built-in availability and resiliency
- Availability Zone aware and configured to be highly available automatically
- Geographically redundant and nearly infinite scale
- No single point of failure
- Up to 12,000 concurrent Remote Access VPN users per Hub when running NGTP(up to 13,500 concurrent users with NGFW)
- Simple configuration utilizing Azure Traffic Manager
- Tried and true Check Point Remote Access VPN
Reference Architecture:
Demo Video:
Additional Information and Resources:
- Labels:
-
Azure
-
Cloud
-
Cloud network security