- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- CNAPP
- :
- Cloudguard Workload and The Serverless Framework
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Cloudguard Workload and The Serverless Framework
The purpose of this article is the outline how CloudGuard Workload protects serverless functions deployed through the Serverless Framework.
What is a Serverless Function?
The term “Serverless” can be the source of confusion for many. A serverless function (like AWS Lambda, or Azure Functions) is an event driven engine that executes code. This allows developers to focus on the code and not worry about maintaining infrastructure. It is also the most efficient way to consume compute power form the public cloud providers, as you are only charged for when the function is running. The cloud provider handles the scalability, redundancy, etc.
What is the Serverless Framework?
It’s a movement that demands that the most menial parts of building an application be abstracted away so that developers are free to actually spend their time delivering business value
The Serverless Framework simplifies the task of building applications on AWS Lambda. It gives developers the ability to define their application infrastructure in YAML, but in a much simpler format than Cloud Formation templates. It also automates tasks such as packaging the code with dependencies and uploading to an S3 Bucket. This allows developers to spend more time focusing on development, and less time focusing on infrastructure.
Further information on using the Serverless Framework can be found here:
CloudGuard Workload Protection
CloudGuard Workload is automated security for AWS Lambda functions. It provides seamless vulnerability assessment, and creates deep code flow analysis and behavioral profiles in runtime for unmatched protection - with minimal performance impact.
Observability: Continuously scans functions, to increase security posture- providing observability, and continuous assessment.
Least Privilege Protection: Maximize workload security through automatic least privilege protection for functions, logs, and databases.
Threat Prevention: Zero-touch serverless application security using pattern matching, whitelisting, blacklisting, and more applied at the function level for threat prevention.
There are two engines that achieve this functionality:
- Proact – Scans the code for vulnerabilities, hard coded credentials and overly permissive roles.
- Function Self-Protect (FSP) – FSP is runtime protection that learns the behavior of a lambda function and blocks anomalous processes. FSP can also detect or block attacks based on signatures.
CloudGuard Workload & The Serverless Framework
In order to facilitate seamless integration with the development process, Check Point has developed a CloudGuard Workload plugin for the Serverless Framework. To demonstrate this integration, we will use the OWASP **bleep** Vulnerable Serverless Application (https://github.com/OWASP/DVSA) as a platform.
Let’s examine the serverless.yml file.
Original
|
plugins: - serverless-finch - serverless-offline - serverless-stack-output - serverless-scriptable-plugin custom: stage: ${opt:stage, self:provider.stage} accountId: ${file(backend/serverless/scripts/vars.js):accountId}
|
In order to add the Cloudguard Workload Plugin, we need to modify this file.
Modified
|
plugins: - serverless-finch - serverless-offline - serverless-stack-output - serverless-scriptable-plugin - serverless-cloudguard-plugin custom: stage: ${opt:stage, self:provider.stage} accountId: ${file(backend/serverless/scripts/vars.js):accountId} cloudguard: fsp: Enabled: true proact: Enabled: true StoreJobReport: true |
As demonstrated above, it takes adding only a few lines to the serverless.yml file to integrate Cloudguard Workload. The next time a developer deploys this application, Proact will scan the code and FSP will protect it at runtime.
CloudGuard Reporting
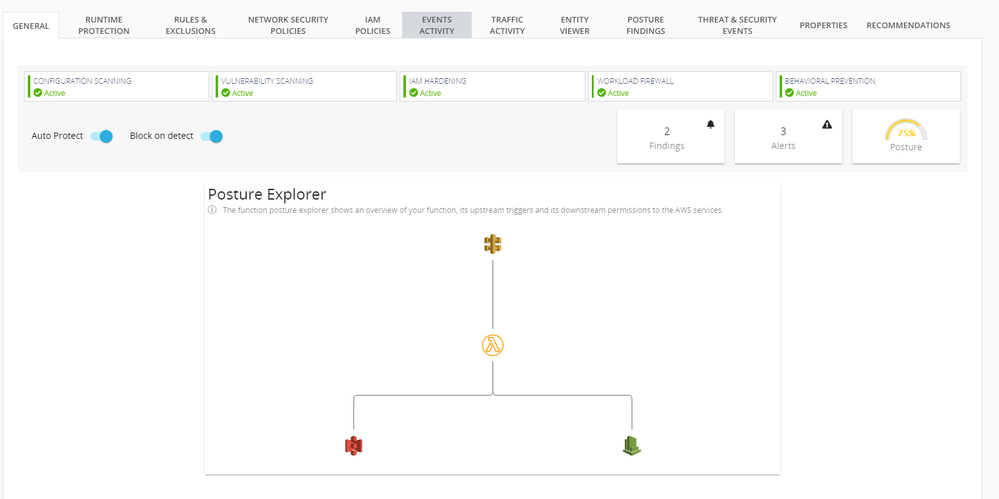
Once CloudGuard Workload has been implemented, you will have enhanced visibility to the function in the CloudGuard Native console.
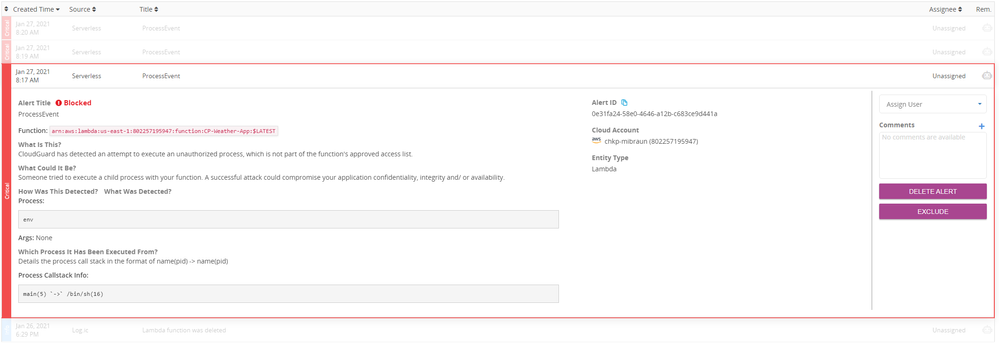
At this point you can drill down into the events or alerts. In this example, a malicious actor attempted to run an “env” command on the serverless function.
For more information on CloudGuard Workload, please visit:
https://www.checkpoint.com/products/workload-protection/
Final Thoughts
As businesses move towards automation, security needs to be seamlessly integrated within development processes. The integration of CloudGuard Workload with the Serverless Framework is an example of feature rich security tools that require little administrative overhead to implement.