- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- CNAPP
- :
- Re: Checkpoint CloudGuard w Kubernetes
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Checkpoint CloudGuard w Kubernetes
Hello! I've deployed the cloudguard-2.10.2 chart into a Kubernetes cluster in AWS. I am now attempting to learn how to affect policy with Admission Control. The GSL builder makes things really easy, very intuitive! Great!
I've temporarily disabled runtimeProtection but imageScan and adminssionControl are both still enabled and checking in.
While in the console UI:
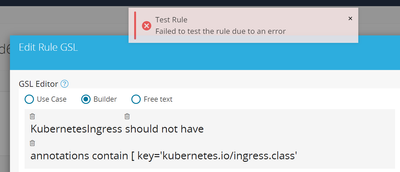
- When creating a new policy and I try to test it, I'm presented with a somewhat perplexing "Failed to test the rule due to an error". How can I troubleshoot the cause of the error? I don't see it in the admission-policy container log or the console log in the browser?
Thanks for taking a look!
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi David, there seems to be a syntax error in your GSL. You need to close the scope block with a ]
KubernetesIngress should not have annotations contain [ key='kubernetes.io/ingress.class' ]
2 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi David, there seems to be a syntax error in your GSL. You need to close the scope block with a ]
KubernetesIngress should not have annotations contain [ key='kubernetes.io/ingress.class' ]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ha! Absolutely right, that did it. Thank you!