- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- CNAPP
- :
- Amazon S3 Bucket encryption compliance validation
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Amazon S3 Bucket encryption compliance validation
Amazon S3 is subject to compliance with standards like HIPAA, PCI, or FedRAMP
Data at rest encryption secures the object while it is saved on the disk. In case encrypted files are obtained by an unauthorized party, they cannot be open without the encryption key.
The Amazon S3 buckets default encryption setting is set to Disable.
You have to ensure that Amazon S3 buckets have Default Encryption feature enabled.
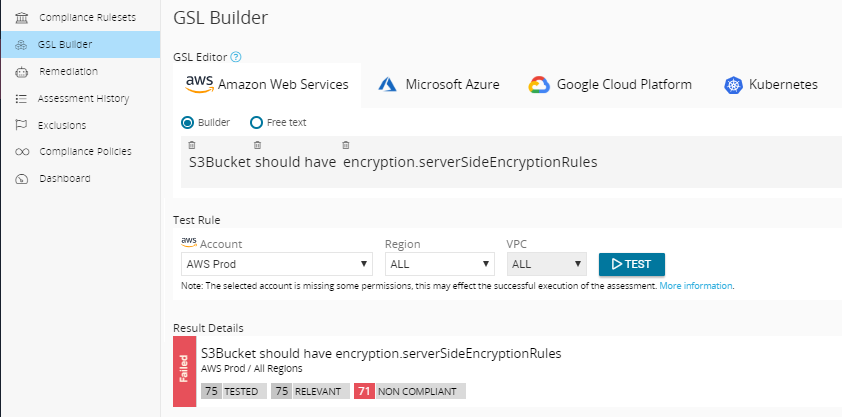
With CloudGuard Dome9 GSL tool, you can run a simple query on thousands of S3 buckets and know in few seconds if any of your S3 buckets are not encrypted.
S3Bucketshould have encryption.serverSideEncryptionRules
You can easily add automatic remediation using CloudBots that would always enable encryption on existing buckets and future buckets that would be created.
Watch this 3-minute How-to video to learn how easily you can enforce compliance at all times.
For more cloud security best practices (CLOUD SECURITY POSTURE REPOSITORY (CSPR) click here