Hi community,
another easy way to test and experience the SandBlast API is via a API development tool called Postman | API Development Environment.
You can store API samples in collections in the left of the interface:
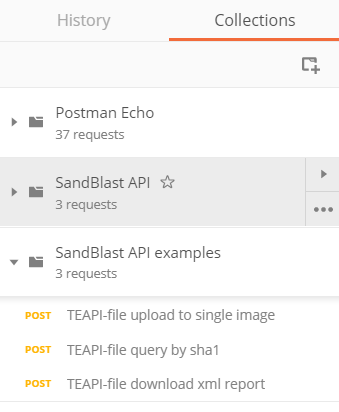
1) File upload to single image
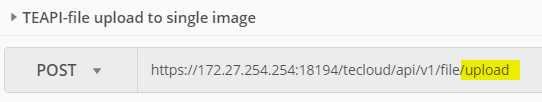
Create a post request to your appliance´s API address for file upload:
Populate the request body:
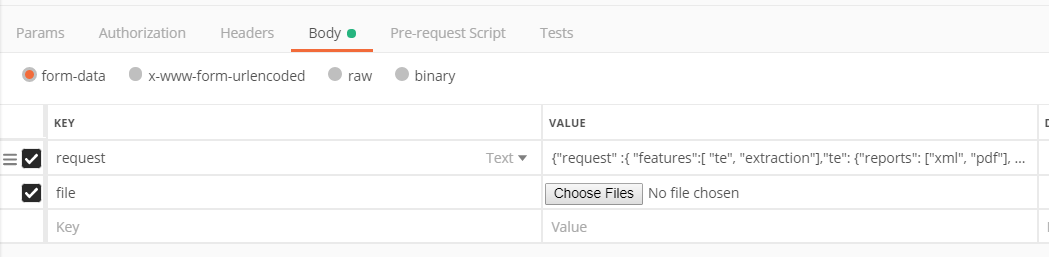
"request" to emulate on Win7/Office 2013 image only (you can omit the "extraction" feature if you want but it does not hurt here :-):
{"request" :{ "features":[ "te", "extraction"],"te": {"reports": ["xml", "pdf"], "images":[{"id": "5e5de275-a103-4f67-b55b-47532918fa59","revision":1}]}}}
On "file" you simply need to specify the file you want to upload.
2) Request result after emulation
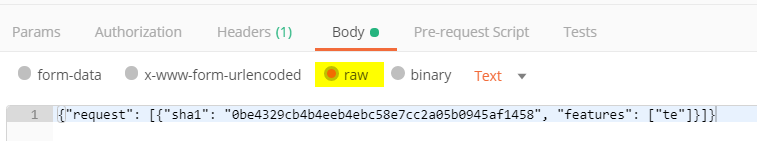
To request the current status of emulation and the final verdict you need to query for the file´s hash via:

Just create the following raw body and adjust the file sha1 hash:
As a result you get something like:
{
"response" : [
{
"features" : [ "te" ],
"file_type" : "doc",
"md5" : "764f4cc91ebd096a1908934c32fc7984",
"sha1" : "0be4329cb4b4eeb4ebc58e7cc2a05b0945af1458",
"sha256" : "bf79ad4cbb4b3c41ecda0dbc34bb799fa3157572",
"status" : {
"code" : 1006,
"label" : "PARTIALLY_FOUND",
"message" : "The request has been partially served"
},
"te" : {
"combined_verdict" : "Malicious",
"confidence" : 3,
"images" : [
{
"id" : "5e5de275-a103-4f67-b55b-47532918fa59",
"report" : {
"full_report" : "",
"report_version" : 1,
"verdict" : "Malicious",
"xml_report" : "64845505-20CF-4C4B-8F18-10B173517DB1"
},
"revision" : 1,
"status" : "found"
},
For getting the report XML you need to note the "xml_report" ID from this output.
3) Get XML report for malicious file
To get the XML report data use the "xml_report" ID you get via the previous file hash query:
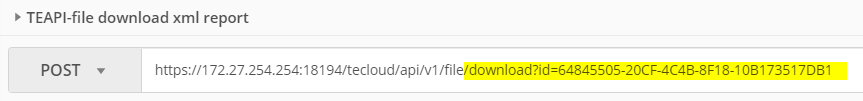
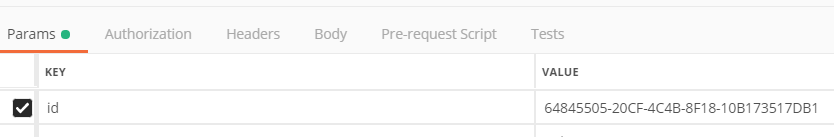
Expected result:
<?xml version="1.0" encoding="UTF-8"?>
<report>
<reportDate>Wed Jul 11 13:07:10 2018
</reportDate>
<CPULevelDetection>false</CPULevelDetection>
<System>
<Osname>Windows 7</Osname>
<OsInfo>Microsoft Windows 7 32 bit, Office 2013, Adobe Acrobat Reader 11.0, Adobe Flash Player 12, Java SE 1.7.0</OsInfo>
<OsUID>5e5de275-a103-4f67-b55b-47532918fa59</OsUID>
<OsRev>234</OsRev>
</System>
<ScreenShotsNames>
<ScreenShot>ScreenShot1.bmp</ScreenShot>
<ScreenShot>ScreenShot2.bmp</ScreenShot>
<ScreenShot>ScreenShot3.bmp</ScreenShot>
<ScreenShot>ScreenShot4.bmp</ScreenShot>
</ScreenShotsNames>
<Activities>
<Command>
<CommandName>ProcessEvent</CommandName>
<ID>8</ID>
<Time>00:00:09</Time>
<Src>C:\Program Files\Microsoft Office\Office15\WINWORD.EXE</Src>
<Dst>C:\Windows\System32\calc.exe</Dst>
<Action>Create</Action>
</Command>
<Command>
<CommandName>RegistryEvent</CommandName>
[...]
Attached you can find the samples as an export from my Postman collections which you can simply import to your Postman installation:

So have fun with SandBlast API.
Regards Thomas










