- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Announcing Quantum R82.10!
Learn MoreOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Developers
- :
- API / CLI Discussion
- :
- Getting the times of 'Install Policy"
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Getting the times of 'Install Policy"
Hi,
Is there an easy way to get the install times for the "Install Policy" operations like in the embedded picture, but with a WAPI REST API call? The screenshot is from Audit Logs, from the Checkpoint controller portal.
I can't find any REST API in the documentation. I used 'show-tasks', which doesn't have any "install" references in the"task-name" field (from the REST API's response message). I also tried to use show-logs, but got the permissions error (see embedded picture).
Thanks for your prompt help.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sadly, you have to filter on the task-name field. The rest of the task's fields depend on the type of task it is, but there is no distinct "task-type" field. Also note the tasks are first-in-first-out. Task 1 is the oldest task in the list. To get recent policy installations, you have to look at the tasks towards the end of the list (thus my 'offset 2500' below).
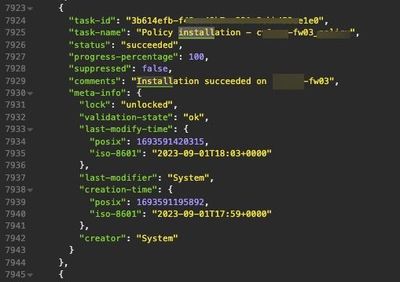
Here is an exemplar task object corresponding to a successful policy installation. The policy package's name was Standard, and the firewall's name was DallasSA. Standard detail level first, then full detail level:
[Expert@DallasSA]# mgmt_cli -f json -r true show tasks limit 500 offset 2500 | jq -c '.tasks[]' | grep "Policy installation" | tail -n 1 | jq .
{
"task-id": "a8dee8f6-00f4-4a34-9d94-e29fa9ac6328",
"task-name": "Policy installation - Standard",
"status": "succeeded",
"progress-percentage": 100,
"suppressed": false,
"comments": "Installation succeeded on DallasSA",
"meta-info": {
"lock": "unlocked",
"validation-state": "ok",
"last-modify-time": {
"posix": 1691255301129,
"iso-8601": "2023-08-05T17:08+0000"
},
"last-modifier": "System",
"creation-time": {
"posix": 1691255275000,
"iso-8601": "2023-08-05T17:07+0000"
},
"creator": "System"
}
}
[Expert@DallasSA]# mgmt_cli -f json -r true show tasks limit 500 offset 2500 details-level full | jq -c '.tasks[]' | grep "Policy installation" | tail -n 1 | jq .
{
"uid": "d3e5cd97-5e4a-4730-a515-7a237a977131",
"type": "task",
"domain": {
"uid": "41e821a0-3720-11e3-aa6e-0800200c9fde",
"name": "SMC User",
"domain-type": "domain"
},
"task-id": "a8dee8f6-00f4-4a34-9d94-e29fa9ac6328",
"task-name": "Policy installation - Standard",
"status": "succeeded",
"progress-percentage": 100,
"start-time": {
"posix": 1691255274991,
"iso-8601": "2023-08-05T17:07+0000"
},
"last-update-time": {
"posix": 1691255301107,
"iso-8601": "2023-08-05T17:08+0000"
},
"suppressed": false,
"task-details": [
{
"uid": "385ec945-276e-49ed-b0c7-1e793159c713",
"name": null,
"domain": {
"uid": "41e821a0-3720-11e3-aa6e-0800200c9fde",
"name": "SMC User",
"domain-type": "domain"
},
"color": "black",
"statusCode": "succeeded",
"statusDescription": "Succeeded",
"taskNotification": "d3e5cd97-5e4a-4730-a515-7a237a977131",
"gatewayId": "ea61e15b-0a8e-e441-a015-31dec0dcd15b",
"policyId": "f9835641-5436-49fa-97e4-042a9fbb88de",
"fastInstallStatus": {
"worksessionId": "19ec3896-de91-4a08-998f-d057cdbac941",
"gatewayId": "ea61e15b-0a8e-e441-a015-31dec0dcd15b",
"policyId": "f9835641-5436-49fa-97e4-042a9fbb88de",
"status": "eligible",
"detailedReason": []
},
"runningStages": [],
"waitingStages": [],
"stagesInfo": [
{
"type": "info",
"stage": "modern verification",
"messages": []
}
],
"cluster": false,
"meta-info": {
"validation-state": "ok",
"last-modify-time": {
"posix": 1691255298536,
"iso-8601": "2023-08-05T17:08+0000"
},
"last-modifier": "System",
"creation-time": {
"posix": 1691255275622,
"iso-8601": "2023-08-05T17:07+0000"
},
"creator": "System"
},
"tags": [],
"icon": "General/globalsNa",
"comments": "",
"display-name": "",
"customFields": null,
"gatewayName": "DallasSA",
"revision": "19ec3896-de91-4a08-998f-d057cdbac941"
}
],
"comments": "Installation succeeded on DallasSA",
"color": "black",
"icon": "General/globalsNa",
"tags": [],
"meta-info": {
"lock": "unlocked",
"validation-state": "ok",
"last-modify-time": {
"posix": 1691255301129,
"iso-8601": "2023-08-05T17:08+0000"
},
"last-modifier": "System",
"creation-time": {
"posix": 1691255275000,
"iso-8601": "2023-08-05T17:07+0000"
},
"creator": "System"
},
"read-only": false
}
15 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here are a few suggestions:
1| Go directly to the Install Policy log file in $FWDIR/log/install_policy.elg
2| Use the same shows-tasks command with grep and before and after lines, for example:
mgmt_cli show tasks status successful details-level standard | grep -A 10 -B 10 "Policy installation"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @Tal_Paz-Fridman .
I don't think we have permissions to access the Checkpoint FW, and issue CLI commands from our python program to issue the mgmt_cli show tasks command.
All our calls to the Checkpoint firewall is via REST API calls (Web Services), with a service account. Is there a REST API solution to get the Install Policy times?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The API command is one that should be able to run remotely using Web Services
https://sc1.checkpoint.com/documents/latest/APIs/index.html#web/show-tasks~v1.9%20
It is important that the administrators using the run the command has the relevant permissions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, we are already using it like below, and search for the firewall and the 'policy installation' keyword in the REST API response's "task-name", but all the tasks in the response are for a different (not the one we are interested in) firewall and are related to an automated script running.
Would the WAPI show-tasks call grabs the tasks for all the firewalls in the mgmt controller? I am wondering why I see one firewall in the response, which isn't the firewall that the policy was installed on. Even a max value of 500 for the body's parameter "limit", I can't see my target firewall.
Maybe there is a permission issue I need to look more into. But the service account is admin, so there shouldn't be any permission issue I don't believe.
url = f"{url}/show-tasks"
body = {"details-level": "standard", "limit": 500, "offset": 0}
body = {"details-level": "standard", "limit": 500, "offset": 0}
response = self.session.post(url, json=body, verify=self.verify)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Tal_Paz-Fridman I just thought of something, so my program is using a 'admin' service account, when making that 'show-tasks' api call. The response only shows tasks from one firewall (the 'wrong' firewall, where the access rule wasn't installed on).
The policy install was actually done by an admin person, manually (not via our program with a install-policy REST API POST call). Would the show-tasks API call will also grab all the tasks, including those policy install tasks by that admin person?
So far, I only see the 'creator' field being the service account that my program is using, in the response.
Wondering why? Maybe it's a permissions issue, that causes 'show-tasks' not being able to grab all the tasks for all firewalls managed in the mgmt controller? Maybe, the admin service accounts that my program is using needs more permissions roles?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The output should show all install policy actions regardless of the administrator.
Consider running a test where you initiate install policy (or someone in your team), then shortly after check that you see the output using the shows-tasks command.
Another option would to use the show-logs command:
mgmt_cli show logs new-query.time-frame last-hour new-query.type audit
https://sc1.checkpoint.com/documents/latest/APIs/index.html#cli/show-logs~v1.9%20
This will allow to go over the same audit logs you attached as an image.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @Tal_Paz-Fridman, I will go from there and try out per your suggestions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sadly, you have to filter on the task-name field. The rest of the task's fields depend on the type of task it is, but there is no distinct "task-type" field. Also note the tasks are first-in-first-out. Task 1 is the oldest task in the list. To get recent policy installations, you have to look at the tasks towards the end of the list (thus my 'offset 2500' below).
Here is an exemplar task object corresponding to a successful policy installation. The policy package's name was Standard, and the firewall's name was DallasSA. Standard detail level first, then full detail level:
[Expert@DallasSA]# mgmt_cli -f json -r true show tasks limit 500 offset 2500 | jq -c '.tasks[]' | grep "Policy installation" | tail -n 1 | jq .
{
"task-id": "a8dee8f6-00f4-4a34-9d94-e29fa9ac6328",
"task-name": "Policy installation - Standard",
"status": "succeeded",
"progress-percentage": 100,
"suppressed": false,
"comments": "Installation succeeded on DallasSA",
"meta-info": {
"lock": "unlocked",
"validation-state": "ok",
"last-modify-time": {
"posix": 1691255301129,
"iso-8601": "2023-08-05T17:08+0000"
},
"last-modifier": "System",
"creation-time": {
"posix": 1691255275000,
"iso-8601": "2023-08-05T17:07+0000"
},
"creator": "System"
}
}
[Expert@DallasSA]# mgmt_cli -f json -r true show tasks limit 500 offset 2500 details-level full | jq -c '.tasks[]' | grep "Policy installation" | tail -n 1 | jq .
{
"uid": "d3e5cd97-5e4a-4730-a515-7a237a977131",
"type": "task",
"domain": {
"uid": "41e821a0-3720-11e3-aa6e-0800200c9fde",
"name": "SMC User",
"domain-type": "domain"
},
"task-id": "a8dee8f6-00f4-4a34-9d94-e29fa9ac6328",
"task-name": "Policy installation - Standard",
"status": "succeeded",
"progress-percentage": 100,
"start-time": {
"posix": 1691255274991,
"iso-8601": "2023-08-05T17:07+0000"
},
"last-update-time": {
"posix": 1691255301107,
"iso-8601": "2023-08-05T17:08+0000"
},
"suppressed": false,
"task-details": [
{
"uid": "385ec945-276e-49ed-b0c7-1e793159c713",
"name": null,
"domain": {
"uid": "41e821a0-3720-11e3-aa6e-0800200c9fde",
"name": "SMC User",
"domain-type": "domain"
},
"color": "black",
"statusCode": "succeeded",
"statusDescription": "Succeeded",
"taskNotification": "d3e5cd97-5e4a-4730-a515-7a237a977131",
"gatewayId": "ea61e15b-0a8e-e441-a015-31dec0dcd15b",
"policyId": "f9835641-5436-49fa-97e4-042a9fbb88de",
"fastInstallStatus": {
"worksessionId": "19ec3896-de91-4a08-998f-d057cdbac941",
"gatewayId": "ea61e15b-0a8e-e441-a015-31dec0dcd15b",
"policyId": "f9835641-5436-49fa-97e4-042a9fbb88de",
"status": "eligible",
"detailedReason": []
},
"runningStages": [],
"waitingStages": [],
"stagesInfo": [
{
"type": "info",
"stage": "modern verification",
"messages": []
}
],
"cluster": false,
"meta-info": {
"validation-state": "ok",
"last-modify-time": {
"posix": 1691255298536,
"iso-8601": "2023-08-05T17:08+0000"
},
"last-modifier": "System",
"creation-time": {
"posix": 1691255275622,
"iso-8601": "2023-08-05T17:07+0000"
},
"creator": "System"
},
"tags": [],
"icon": "General/globalsNa",
"comments": "",
"display-name": "",
"customFields": null,
"gatewayName": "DallasSA",
"revision": "19ec3896-de91-4a08-998f-d057cdbac941"
}
],
"comments": "Installation succeeded on DallasSA",
"color": "black",
"icon": "General/globalsNa",
"tags": [],
"meta-info": {
"lock": "unlocked",
"validation-state": "ok",
"last-modify-time": {
"posix": 1691255301129,
"iso-8601": "2023-08-05T17:08+0000"
},
"last-modifier": "System",
"creation-time": {
"posix": 1691255275000,
"iso-8601": "2023-08-05T17:07+0000"
},
"creator": "System"
},
"read-only": false
}
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @Bob_Zimmerman for the feedbacks. As I mentioned before, currently we (our Python program) are only allowed to interact with the Checkpoint via REST API. I will check with my Checkpoint admin guy to see about using the CLI commands and CLI logs.
I just tried to use show-tasks API call, with that large offset value, but got nothing back. Any good explanation why?
Request body:
{
"details-level": "standard",
"limit": 500,
"offset": 2500
}
Response:
{
"tasks": [
],
"total": 0
}
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think I got it! It returns nothing since there isn't that many (> 2500) tasks, right?
I do see my firewall now and the 'Policy installation'. So I just need to loop through, with incrementing offset. Our program currently is using a fixed offset of 0!
Thank you everyone for your feedbacks. I love this Checkpoint forum, so responsive to my questions! 👍
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
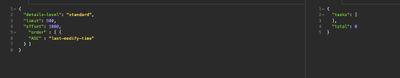
Actually, can someone share with me the request's body that will help sort the tasks by 'task-name', then by the 'iso-8601' time of the 'last-modify-time' field?
I tried (screenshot), but not working.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The body looks correct, but the only valid value for "ASC" or "DESC" is "name". You can't sort by any other keys as of APIv1.9.1.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
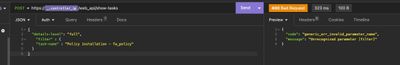
Not sure why 'filter' doesn't work, even though it's listed in the documentation. So I have v1.8, and still got the "message": "Unrecognized parameter [filter]" error message, with show-tasks.
Can you please shred some light?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Probably a documentation bug. Everything to do with tasks feels very unfinished.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK then, thanks for the prompt response.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter