- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Developers
- :
- API / CLI Discussion
- :
- Add new user and assign to an existing group using...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Add new user and assign to an existing group using the generic-object API calls
This document explains the steps to create a user in the R80.x Check Point Security Management Server and assign that user to an existing group using the generic-object API.
Disclaimer
These APIs provide direct access to different objects and fields in the database. As a result if an objects schema change, scripts that relied on specific schema fields may break.
As the generic-object(s) API calls have direct access to change different objects and fields in the database, they do not provide any data validation to ensure that the data added to the fields are following required format for this field. Therefore you have to ensure that the script or 3rd party system you are using to integrate with the management server is doing appropriate data validation before sending the API call.
When you have the option, always prefer to use the documented API calls and not the generic API calls as they are
- They are doing data validation
- They are documented
- They are future compatible
- They are tested
- They are supported by Technical Assistance Center (TAC)
Data flow
The data flow for the generic API calls are the same as when using the documented API
(Login) > (Add) > (Assign) > (Publish) > (Logout)
- Login to session
POST https://<mgmt-server>:<port>/web_api/login - Add new user
POST https://<mgmt-server>:<port>/web_api/add-generic-object - Assign newly created user to existing group
POST https://<mgmt-server>:<port>/web_api/set-generic-object - Publish changes
POST https://<mgmt-server>:<port>/web_api/publish - Logout
POST https://<mgmt-server>:<port>/web_api/logout
Format of the API calls
Please refer to the Security Management API reference guide if you need more information about the login, publish and logout API calls. https://sc1.checkpoint.com/documents/latest/APIs/index.html#introduction~v1.1
Below is describing the formatting of the generic-objects API calls used to create a new user and add that user to an existing user group
Request - 2 Add new user
Note: When adding a new user the following fields are the minimal required fields, all other fields that are omitted will be created with default values.mgmt_cli:
mgmt_cli add generic-object create "com.checkpoint.objects.classes.dummy.CpmiUser" name "myvpnuser" userc.create "com.checkpoint.objects.classes.dummy.CpmiSpecificUserc" userc.owned-object.ike.create "com.checkpoint.objects.classes.dummy.CpmiSpecificUsercIke"
Web Services:
{
"create" : "com.checkpoint.objects.classes.dummy.CpmiUser",
"name":"myvpnuser",
"userc" : {
"create" : "com.checkpoint.objects.classes.dummy.CpmiSpecificUserc",
"owned-object" : {
"ike" : {
"create" : "com.checkpoint.objects.classes.dummy.CpmiSpecificUsercIke"
}
}
}
}
Example 1 - Adding a new user with “Check point Password” as authentication method.
The password hash in the internalPassword object must be defined using a two character long salt string and a 4-8 character long key that needs to be encrypted with DES. The key is they user password in clear text and cannot contain spaces.
You can for example use the following command in order to generate a password hash for the password Mypaswd!
# cpopenssl passwd -crypt -salt $(cpopenssl rand -base64 2) 'Mypaswd!'
mgmt._cli:
# mgmt_cli -s id.txt -d "SMC User" -f json add generic-object create "com.checkpoint.objects.classes.dummy.CpmiUser" name "myvpnuser" email "myvpn@user.local" phoneNumber "00468118118" color "BLUE_1" authMethod "INTERNAL_PASSWORD" internalPassword "59WtGQ3UiC5lo" adminExpirationBaseData.create "com.checkpoint.objects.classes.dummy.CpmiAdminExpirationBaseData" adminExpirationBaseData.owned-object.expirationDate "10-Apr-2018" userc.create "com.checkpoint.objects.classes.dummy.CpmiSpecificUserc" userc.owned-object.useGlobalEncryptionValues "true" userc.owned-object.ike.create "com.checkpoint.objects.classes.dummy.CpmiSpecificUsercIke"
Web Services:
|
HTTP POST |
POST https://<mgmt-server>:<port>/web_api/-add-generic-object |
|
Headers |
Content-Type: application/json X-chkp-sid: <The SID retrieved from the Login command> |
|
Body |
{ "create" : "com.checkpoint.objects.classes.dummy.CpmiUser", "name":"myvpnuser", "email":"myvpn@user.local", "phoneNumber":"00468118118", "color" : "BLUE_1", "authMethod" : "INTERNAL_PASSWORD", "internalPassword":"59WtGQ3UiC5lo", "adminExpirationBaseData" : { "create" : "com.checkpoint.objects.classes.dummy.CpmiAdminExpirationBaseData", "owned-object" : { "expirationDate" : "10-Apr-2018" } }, "userc" : { "create" : "com.checkpoint.objects.classes.dummy.CpmiSpecificUserc", "owned-object" : { "useGlobalEncryptionValues" : "true", "ike" : { "create" : "com.checkpoint.objects.classes.dummy.CpmiSpecificUsercIke" } } } } |
Response - You need to retrieve the UID of the user object you just created in order to be able to add this user to a user group
|
Response Body |
{…. "adminExpirationBaseData": { "objId": "f871998d-8e2f-4108-b4af-35a144642897", "checkPointObjId": null, "domainId": "41e821a0-3720-11e3-aa6e-0800200c9fde", "expirationDateVisualNotif": true, "expirationDate": "25-Apr-2018", "expirationDateMethod": "EXPIRE_AT", "folderPath": "1edb57e2-37f3-468f-b613-4a2bcf4e5315", "text": null, "folder": "1edb57e2-37f3-468f-b613-4a2bcf4e5315", "is_owned": false, "ownedName": "myvpnuser" }, "days": 127, "email": "myvpnuser@test.local", "authMethod": "INTERNAL_PASSWORD", "tohour": "23:59", "administrator": false, "uid": "ac7fba44-6875-45d2-ad04-6c79508b2f30", …… "_original_type": "CpmiUser" …….} |
Example 2 - Adding a new user with “Radius” as authentication method towards any Radius server defined in the management server
mgmt._cli:
# mgmt_cli -s id.txt -d "SMC User" -f json add generic-object create "com.checkpoint.objects.classes.dummy.CpmiUser" name "myvpnuser" email "myvpn@user.local" phoneNumber "00468118118" color "BLUE_1" authMethod "RADIUS" adminExpirationBaseData.create "com.checkpoint.objects.classes.dummy.CpmiAdminExpirationBaseData" adminExpirationBaseData.owned-object.expirationDate "10-Apr-2018" userc.create "com.checkpoint.objects.classes.dummy.CpmiSpecificUserc" userc.owned-object.useGlobalEncryptionValues "true" userc.owned-object.ike.create "com.checkpoint.objects.classes.dummy.CpmiSpecificUsercIke"
Web Services:
|
HTTP POST |
POST https://<mgmt-server>:<port>/web_api/-add-generic-object |
|
Headers |
Content-Type: application/json X-chkp-sid: <The SID retrieved from the Login command> |
|
Body |
{ "create" : "com.checkpoint.objects.classes.dummy.CpmiUser", "name":"myvpnuser", "email":"myvpn@user.local", "phoneNumber":"00468118118", "color" : "BLUE_1", "authMethod" : "RADIUS ", "adminExpirationBaseData" : { "create" : "com.checkpoint.objects.classes.dummy.CpmiAdminExpirationBaseData", "owned-object" : { "expirationDate" : "10-Apr-2018" } }, "userc" : { "create" : "com.checkpoint.objects.classes.dummy.CpmiSpecificUserc", "owned-object" : { "useGlobalEncryptionValues" : "true", "ike" : { "create" : "com.checkpoint.objects.classes.dummy.CpmiSpecificUsercIke" } } } } |
Response - You need to retrieve the UID of the user object you just created in order to be able to add this user to a user group
|
Response Body |
{…. "adminExpirationBaseData": { "objId": "f871998d-8e2f-4108-b4af-35a144642897", "checkPointObjId": null, "domainId": "41e821a0-3720-11e3-aa6e-0800200c9fde", "expirationDateVisualNotif": true, "expirationDate": "25-Apr-2018", "expirationDateMethod": "EXPIRE_AT", "folderPath": "1edb57e2-37f3-468f-b613-4a2bcf4e5315", "text": null, "folder": "1edb57e2-37f3-468f-b613-4a2bcf4e5315", "is_owned": false, "ownedName": "myvpnuser" }, "days": 127, "email": "myvpnuser@test.local", "authMethod": "RADIUS", "tohour": "23:59", "administrator": false, "uid": "ac7fba44-6875-45d2-ad04-6c79508b2f30", …… "_original_type": "CpmiUser" …….} |
Example 3 - Adding a new user with “Radius” as authentication method towards a specific radius server or radius group of servers.
To specify the Radius server or group of server the object “radiusServer” shpuld contain the uid of the Radius server or group of server you want to assign to this user.
mgmt_cli:
# mgmt_cli -s id.txt -d "SMC User" -f json add generic-object create "com.checkpoint.objects.classes.dummy.CpmiUser" name "myvpnuser" email "myvpn@user.local" phoneNumber "00468118118" color "BLUE_1" authMethod "RADIUS" radiusServer "0972a020-2915-4a78-8868-135d13b3f7bb" adminExpirationBaseData.create "com.checkpoint.objects.classes.dummy.CpmiAdminExpirationBaseData" adminExpirationBaseData.owned-object.expirationDate "10-Apr-2018" userc.create "com.checkpoint.objects.classes.dummy.CpmiSpecificUserc" userc.owned-object.useGlobalEncryptionValues "true" userc.owned-object.ike.create "com.checkpoint.objects.classes.dummy.CpmiSpecificUsercIke"
Web Services:
|
HTTP POST |
POST https://<mgmt-server>:<port>/web_api/-add-generic-object |
|
Headers |
Content-Type: application/json X-chkp-sid: <The SID retrieved from the Login command> |
|
Body |
{ "create" : "com.checkpoint.objects.classes.dummy.CpmiUser", "name":"myvpnuser", "email":"myvpn@user.local", "phoneNumber":"00468118118", "color" : "BLUE_1", "authMethod" : "RADIUS ", "radiusServer" : "0972a020-2915-4a78-8868-135d13b3f7bb", "adminExpirationBaseData" : { "create" : "com.checkpoint.objects.classes.dummy.CpmiAdminExpirationBaseData", "owned-object" : { "expirationDate" : "10-Apr-2018" } }, "userc" : { "create" : "com.checkpoint.objects.classes.dummy.CpmiSpecificUserc", "owned-object" : { "useGlobalEncryptionValues" : "true", "ike" : { "create" : "com.checkpoint.objects.classes.dummy.CpmiSpecificUsercIke" } } } } |
Response - You need to retrieve the UID of the user object you just created in order to be able to add this user to a user group
|
Response Body |
{…. "adminExpirationBaseData": { "objId": "f871998d-8e2f-4108-b4af-35a144642897", "checkPointObjId": null, "domainId": "41e821a0-3720-11e3-aa6e-0800200c9fde", "expirationDateVisualNotif": true, "expirationDate": "25-Apr-2018", "expirationDateMethod": "EXPIRE_AT", "folderPath": "1edb57e2-37f3-468f-b613-4a2bcf4e5315", "text": null, "folder": "1edb57e2-37f3-468f-b613-4a2bcf4e5315", "is_owned": false, "ownedName": "myvpnuser" }, "days": 127, "email": "myvpnuser@test.local", "authMethod": "RADIUS", "tohour": "23:59", "administrator": false, "uid": "ac7fba44-6875-45d2-ad04-6c79508b2f30", …… "_original_type": "CpmiUser" …….} |
Request - 3 Assign newly created user to existing group.
To assign a user to a group you need to provide the UID of the group you want to change and you need to add the user UID to that group.
To get the UID of an object you can use# mgmt_cli –s id.txt true -f json show generic-objects name "name of object" details-level "full"
Or in Web Services
HTTP POST https://<mgmt-server>:<port>/web_api/show-generic-objects
Headers Content-Type: application/json
X-chkp-sid: <The SID retrieved from the Login command>
Body {
"name" : " Clientless-vpn-user",
"details-level" : "full"
}mgmt_cli
mgmt_cli -s id.txt -d "SMC User" -f json set generic-object uid "d5654c00-a153-5148-b451-a5c5d9909895" emptyFieldName.add.1 "ac7fba44-6875-45d2-ad04-6c79508b2f30"
Web Services:
|
HTTP POST |
https://<mgmt-server>:<port>/web_api/set-generic-object |
|
Headers |
Content-Type: application/json X-chkp-sid: <The SID retrieved from the Login command> |
|
Body |
{ "uid" : "d5654c00-a153-5148-b451-a5c5d9909895", "emptyFieldName": { "add": " ac7fba44-6875-45d2-ad04-6c79508b2f30" } } |
Response – will show you the object properties with the new expiration date
|
Response Body |
{…. "email" : "", "emptyFieldName" : [ "ea511503-86f1-4616-bd04-4c2a4141b059", "ea2fb4e7-8b1e-44c3-b0e6-91178132f529", "fc182f23-40ec-49ab-a11b-86ac8e12259f", "1d1046c8-3863-4cd6-87de-7d723a63a80f", "a0abbf0f-979a-4757-a7f7-3b0023e9c6ab" ], "type" : "usrgroup", "groups" : [ ], },……… |
Full Example:
The following CLI example will create a user with username “myvpnuser” password “Mypaswd!” and assign that user to group “Clientless-vpn-user”
# Create user myvpnuser and retrieve UID of newly created user
mgmt_cli -r true -d "SMC User" -f json login > id.txt
varUidUsr=$(mgmt_cli -s id.txt -d "SMC User" -f json add generic-object create "com.checkpoint.objects.classes.dummy.CpmiUser" name "myvpnuser" email "myvpn@user.local" phoneNumber "00468118118" color "BLUE_1" authMethod "INTERNAL_PASSWORD" internalPassword $(cpopenssl passwd -crypt -salt $(cpopenssl rand -base64 2) 'Mypaswd!') adminExpirationBaseData.create "com.checkpoint.objects.classes.dummy.CpmiAdminExpirationBaseData" adminExpirationBaseData.owned-object.expirationDate "10-Apr-2018" userc.create "com.checkpoint.objects.classes.dummy.CpmiSpecificUserc" userc.owned-object.useGlobalEncryptionValues "true" userc.owned-object.ike.create "com.checkpoint.objects.classes.dummy.CpmiSpecificUsercIke" | jq -r '.uid')
# Get UID of existing group Clientless-vpn-user
varUidGrp=$(mgmt_cli -s id.txt -d "SMC User" -f json show generic-objects name "Clientless-vpn-user" | jq -r '.objects[] | select (.["type"] | contains ("CpmiUserGroup")) | .uid')
# Add user myvpnuser to existing group Clientless-vpn-user
mgmt_cli -s id.txt -d "SMC User" -f json set generic-object uid "$varUidGrp" emptyFieldName.add.1 "$varUidUsr"
mgmt_cli -s id.txt -d "SMC User" -f json publish
mgmt_cli -s id.txt -d "SMC User" -f json logout
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
Thank you for your information.
It's really useful!
I would like to create users to be authenticated with a 3rd party certicate. Do you know the property to enable the "public key" option on the user object?
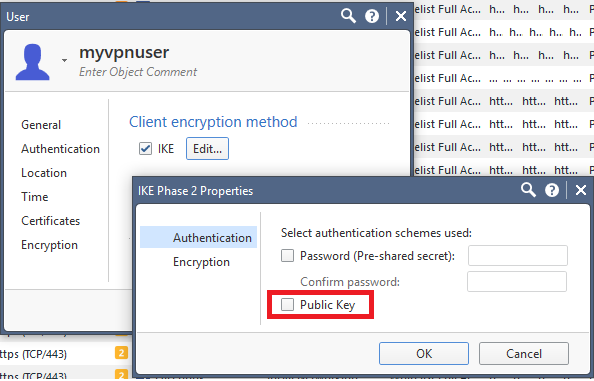
Thanks,
Regards,
Laurent
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
field name - "userc.ike.isakmpAuthmethods"
value - "SIGNATURES"
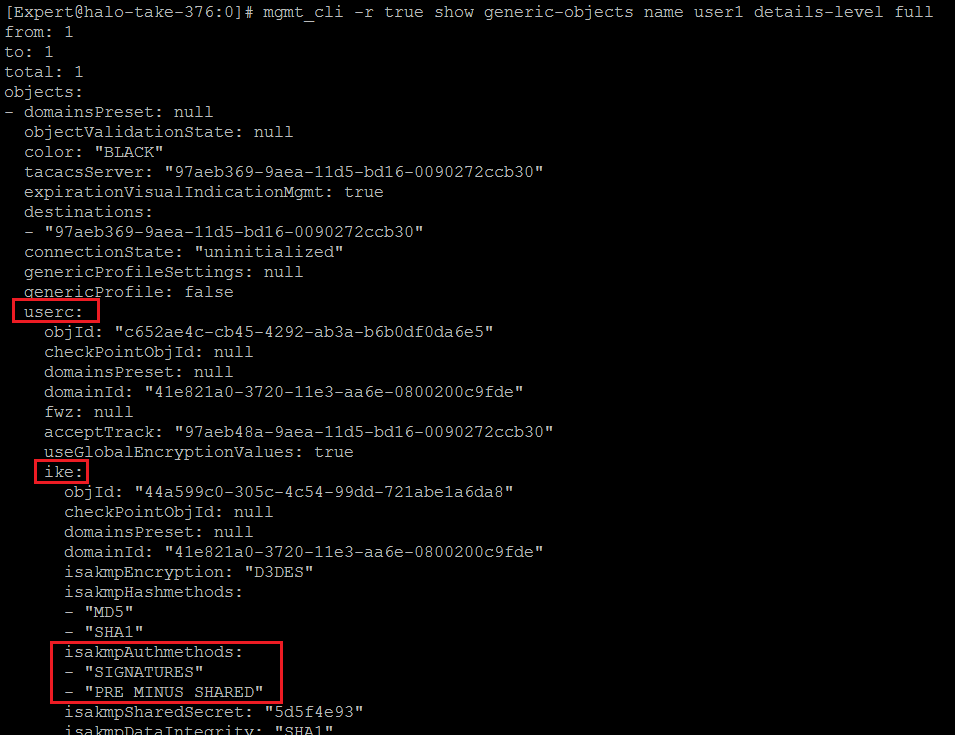
pay attention that this is a container field.
robert.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you please help me out with the correct syntax for adding something to a container field?
During object creation, I get either an error message or the container field stays empty:
add generic-object create "com.checkpoint.objects.classes.dummy.CpmiUser" name "myvpnuser" comments "My VPN User" color "BLUE" adminExpirationBaseData.create "com.checkpoint.objects.classes.dummy.CpmiAdminExpirationBaseData" adminExpirationBaseData.owned-object.expirationDate "31-Jan-2030" userc.create "com.checkpoint.objects.classes.dummy.CpmiSpecificUserc" userc.owned-object.useGlobalEncryptionValues "true" userc.owned-object.ike.create "com.checkpoint.objects.classes.dummy.CpmiSpecificUsercIke" userc.owned-object.ike.owned-object.isakmpAuthmethods.add.1 "SIGNATURES"
code: "generic_server_error"
message: "Management server failed to execute command"
add generic-object create "com.checkpoint.objects.classes.dummy.CpmiUser" name "myvpnuser" comments "My VPN User" color "BLUE" adminExpirationBaseData.create "com.checkpoint.objects.classes.dummy.CpmiAdminExpirationBaseData" adminExpirationBaseData.owned-object.expirationDate "31-Jan-2030" userc.create "com.checkpoint.objects.classes.dummy.CpmiSpecificUserc" userc.owned-object.useGlobalEncryptionValues "true" userc.owned-object.ike.create "com.checkpoint.objects.classes.dummy.CpmiSpecificUsercIke" userc.ike.owned-object.isakmpAuthmethods.add.1 "SIGNATURES"
> show generic-objects name myvpnuser details-level full
objects:
...
userc:
objId: "20088ef8-1124-4389-a49b-163cb837d34c"
...
ike:
objId: "c8ab8e39-3fcc-43b0-8175-2e2a3e0d2e06"
checkPointObjId: null
domainId: "41e821a0-3720-11e3-aa6e-0800200c9fde"
isakmpEncryption: "D3DES"
isakmpHashmethods: []
isakmpAuthmethods: []
isakmpSharedSecret: ""
isakmpDataIntegrity: "SHA1"
isakmpTransform: "ESP"
isakmpEncmethods: []
folderPath: "0b48c71a-1820-439e-b744-d0bb17b8f68d"
text: null
folder: "0b48c71a-1820-439e-b744-d0bb17b8f68d"
is_owned: false
ownedName: ""
...
uid: "53a0e295-1b70-4edf-b55b-d63f27cdc4b9"
When I try to manuipulate that container field later, I am not successfull at all:
> set generic-object uid "53a0e295-1b70-4edf-b55b-d63f27cdc4b9" userc.ike.isakmpAuthmethods.add.1 "SIGNATURES"
code: "generic_server_error"
message: "Management server failed to execute command"
> set generic-object uid "53a0e295-1b70-4edf-b55b-d63f27cdc4b9" userc.ike.isakmpAuthmethods.add "SIGNATURES"
code: "generic_server_error"
message: "Management server failed to execute command"
> set generic-object uid "53a0e295-1b70-4edf-b55b-d63f27cdc4b9" .userc.ike.isakmpAuthmethods.add.0 "SIGNATURES"
code: "generic_server_error"
message: "Management server failed to execute command"
Thank you in advance for your help.
Best regards,
Tobias Moritz
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Tobias,
Your syntax to change a container field via API is correct -
userc.ike.isakmpAuthmethods.add "SIGNATURES"
The problem in this specific case is that user object is a legacy R77 object that doesn't have its own API yet, therefore jim oqvist used a generic-objects approach.
It seems that sometimes this approach does't work well, because it has to deal with old database schema serializations, and this is exactly what happened for the field above - the serialization didn't work.
Robert.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Okay, so I guess there is nothing I can do now.
Nevertheless, thank you for that fast answer!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Guessing there has been no change in the IKE Public key issue since the last comments?
I'm in the same boat as Tobias.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Jim for a great guide!
Would it be possible to share how to create a user group using the same method?
Thanks!!
/Nicklas Bargell.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thx to you documentation i was able to create a lot of legacy vpn users with checkpoint password... thanks for that...
but now i found out that starting with R81 checkpoint internal users can have passwords with more than 8 characters (tested this already with secureRemote) (see https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...), so i want to create users with longer passwords, but when i call:
mgmt_cli --port 443 --root true -f json add generic-object create "com.checkpoint.objects.classes.dummy.CpmiUser" name testlong authMethod "INTERNAL_PASSWORD" color "GREEN" internalPassword $(cpopenssl passwd -crypt -salt $(cpopenssl rand -base64 2) "longPass1234") userc.create "com.checkpoint.objects.classes.dummy.CpmiSpecificUserc" userc.owned-object.ike.create "com.checkpoint.objects.classes.dummy.CpmiSpecificUsercIke"
i get this warning:
Warning: truncating password to 8 characters
...and really the password is truncated, if i set the password via GUI i can set more than 8 chars and it works...
do you know how to set long passwords via script??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you see the same behavior with the formally supported APIs for this, which were added in R81?
See: https://sc1.checkpoint.com/documents/latest/APIs/index.html#cli/add-user~v1.7%20
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
just tried the new API:
mgmt_cli --root true add user name "testlong" authentication-method "check point password" password "longPass1234" color "GREEN" expiration-date "2030-05-30" groups.1 VPN-User ignore-warnings true --format json
big thanks, the new api works!!
but beware, you need the "ignore-warnings true" otherwise the command fails...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Correct, you need ignore-warnings true in this case.
This is because a password longer than 8 characters will fail on gateway versions prior to R81.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 3 | |
| 1 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


