If you're using R80.20 and above management (API v1.3), the API can do some of the work for you using the option "show-as-ranges true" to the the API call show access-rulebase.
However, this will not work for rules that use Access Roles or things that aren't host/network objects.
This also will only output up to 20 rules at a time, so you'll have to iterate this command multiple times using the limit/offset parameter.
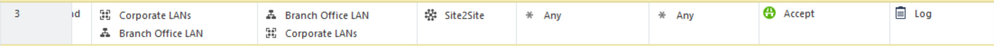
Here's an example that shows what is returned for Rule 3 in the Demo Mode Corporate Policy.
The rule looks like this:
The API returns the following when I dump this one rule (using limit/offset parameters to control this):
[Expert@mumford:0]# mgmt_cli --format json -m demoXXXXXXXX.mgmt.cloud -u aa -p aaaa \
show access-rulebase name "Network" show-as-ranges true limit 1 offset 2
{
"uid": "c0264a80-1832-4fce-8a90-d0849dc4ba33",
"name": "Network",
"rulebase": [
{
"uid": "bda1b370-55ec-473f-9ce0-9ad32a4c0c2e",
"name": "VPN",
"type": "access-section",
"from": 3,
"to": 3,
"rulebase": [
{
"uid": "318147cb-86ec-45b5-b7e4-715b84b81e52",
"name": "VPN between Internal LANs and Branch office LAN",
"type": "access-rule",
"domain": {
"uid": "41e821a0-3720-11e3-aa6e-0800200c9fde",
"name": "SMC User",
"domain-type": "domain"
},
"rule-number": 3,
"track": {
"type": "598ead32-aa42-4615-90ed-f51a5928d41d",
"per-session": false,
"per-connection": true,
"accounting": false,
"enable-firewall-session": false,
"alert": "none"
},
"source-ranges": {
"ipv4": [
{
"start": "145.80.110.0",
"end": "145.80.110.255"
},
{
"start": "22.20.105.0",
"end": "22.20.105.255"
},
{
"start": "198.51.100.15",
"end": "198.51.100.15"
},
{
"start": "198.51.100.16",
"end": "198.51.100.16"
}
],
"ipv6": [],
"others": [],
"excluded-others": []
},
"destination-ranges": {
"ipv4": [
{
"start": "198.51.100.16",
"end": "198.51.100.16"
},
{
"start": "198.51.100.15",
"end": "198.51.100.15"
},
{
"start": "22.20.105.0",
"end": "22.20.105.255"
},
{
"start": "145.80.110.0",
"end": "145.80.110.255"
}
],
"ipv6": [],
"others": [],
"excluded-others": []
},
"service-ranges": {
"tcp": [
{
"start": "0",
"end": "65535"
}
],
"udp": [
{
"start": "0",
"end": "65535"
}
],
"others": [],
"excluded-others": []
},
"vpn": [
"d5c1d927-1b7c-4505-930c-6d047313be60"
],
"action": "6c488338-8eec-4103-ad21-cd461ac2c472",
"action-settings": {
"enable-identity-captive-portal": false
},
"content": [
"97aeb369-9aea-11d5-bd16-0090272ccb30"
],
"content-negate": false,
"content-direction": "any",
"time": [
"97aeb369-9aea-11d5-bd16-0090272ccb30"
],
"custom-fields": {
"field-1": "",
"field-2": "",
"field-3": ""
},
"meta-info": {
"lock": "unlocked",
"validation-state": "ok",
"last-modify-time": {
"posix": 1557068539739,
"iso-8601": "2019-05-05T15:02+0000"
},
"last-modifier": "Saul",
"creation-time": {
"posix": 1557068474330,
"iso-8601": "2019-05-05T15:01+0000"
},
"creator": "admin"
},
"comments": "",
"enabled": true,
"install-on": [
"6c488338-8eec-4103-ad21-cd461ac2c476"
]
}
]
}
],
"objects-dictionary": [
{
"uid": "6c488338-8eec-4103-ad21-cd461ac2c472",
"name": "Accept",
"type": "RulebaseAction",
"domain": {
"uid": "a0bbbc99-adef-4ef8-bb6d-defdefdefdef",
"name": "Check Point Data",
"domain-type": "data domain"
}
},
{
"uid": "97aeb369-9aea-11d5-bd16-0090272ccb30",
"name": "Any",
"type": "CpmiAnyObject",
"domain": {
"uid": "a0bbbc99-adef-4ef8-bb6d-defdefdefdef",
"name": "Check Point Data",
"domain-type": "data domain"
}
},
{
"uid": "64a0417e-d5b0-471b-931f-5e3c31d9ae09",
"name": "Branch Office LAN",
"type": "network",
"domain": {
"uid": "41e821a0-3720-11e3-aa6e-0800200c9fde",
"name": "SMC User",
"domain-type": "domain"
},
"subnet4": "145.80.110.0",
"mask-length4": 24,
"subnet-mask": "255.255.255.0"
},
{
"uid": "51b9a5cf-84b8-47ce-82db-686a35b9ef35",
"name": "Corporate LANs",
"type": "group",
"domain": {
"uid": "41e821a0-3720-11e3-aa6e-0800200c9fde",
"name": "SMC User",
"domain-type": "domain"
}
},
{
"uid": "598ead32-aa42-4615-90ed-f51a5928d41d",
"name": "Log",
"type": "Track",
"domain": {
"uid": "a0bbbc99-adef-4ef8-bb6d-defdefdefdef",
"name": "Check Point Data",
"domain-type": "data domain"
}
},
{
"uid": "6c488338-8eec-4103-ad21-cd461ac2c476",
"name": "Policy Targets",
"type": "Global",
"domain": {
"uid": "a0bbbc99-adef-4ef8-bb6d-defdefdefdef",
"name": "Check Point Data",
"domain-type": "data domain"
}
},
{
"uid": "d5c1d927-1b7c-4505-930c-6d047313be60",
"name": "Site2Site",
"type": "vpn-community-meshed",
"domain": {
"uid": "41e821a0-3720-11e3-aa6e-0800200c9fde",
"name": "SMC User",
"domain-type": "domain"
}
}
],
"from": 3,
"to": 3,
"total": 14
}
As the data is formatted in JSON format, you can probably use jq to extract and output the required data in the required format.
Note the object dictionary at the end which may be necessary to dereference some of the data.



