- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud Cloud Network Security CloudMates General CNAPP CloudGuard - WAF Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Open Garden In Action:
Find and Remediate Threats Everywhere!
New Appliance Announcements
and Faster Threat Prevention
Remote Access VPN – User Experience
Help us with the Short-Term Roadmap
It's Here!
CPX 2025 Content
CheckMates Go:
AI Agents
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Threat Prevention
- :
- r80.20 - Application Control - HTTP parsing erro...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
r80.20 - Application Control - HTTP parsing error occurred (2)
hello
I have URL filtering in checkpoint and when i try to enter in some web page it's writing this error in web browser:"Error: Error: The Web Socket transport is in an invalid state, transitioning into reconnecting".
and in the smartconsol logs, there is these logs:
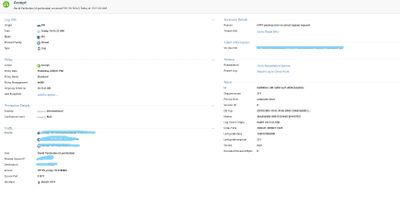
see it in screenshots.
1) IPS detect , but accept
2) Alert and Block Traffic
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Much too small screenshots !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
there are only these logs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Possible this is fixed in a recent JHF.
See: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
Recommend getting the TAC involved.
See: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
Recommend getting the TAC involved.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thanks .
i'll try it in the weekend
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am seeing similar behavior with couple of firewalls on R80.20 too. While there are IPS detect messages with same error "HTTP parsing error occurred, bypassing request" under IPS with accept action.
This is observed on different ports too (may be the nature of traffic could be HTTP).
Did you happen to get a solution.
This is observed on different ports too (may be the nature of traffic could be HTTP).
Did you happen to get a solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, anyone also seeing this issue ?
i am having in r80.20 too, i am seeing it also as an IPS logs
"HTTP parsing error occurred, bypassing request"
action is accept.
looks like it is on http(80) traffic between some app servers
no details on traffic, but i was wondering if it could be an issue in the HTTP protocol decryption process/library
thanks
- Tags:
- ips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We might be able to fix this with a TAC case and packet captures of the relevant traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
i am facing similar issue with R81.20 jhf 92,..find the logs below..
Id: d330ecfd-30a5-b4f5-6836-ff2000000001
Marker: @A@@B@1748421745@C@3663348
Log Server Origin: 14.195.0.0
Time: 2025-05-28T12:18:40Z
Interface Direction: outbound
Interface Name: bond1
Connection Direction: Outgoing
Id Generated By Indexer: false
First: false
Sequencenum: 27
Source Zone: Internal
Destination Zone: External
Service ID: http
Source: 10.199.X.X
Source Port: 56125
Destination: 199.X.X.X
Destination Port: 80
IP Protocol: 6
Xlate (NAT) Source IP: 125.X.X.X
Xlate (NAT) Source Port: 11027
Xlate (NAT) Destination Port:0
NAT Rule Number: 89
NAT Additional Rule Number: 0
User: XXX Helpdesk (XX-helpdesk@XX.local)
Source User Name: XXX Helpdesk (XX-helpdesk@XX.local)
Source Machine Name: XX-l01-ap03@XX.local
Src User Dn: CN=XX Helpdesk,OU=Administrative,DC=X,DC=local
Destination Updatable Object:Office365 Worldwide Services
Dst Uo Icon: @app/cp_ms_office365
Nat Rule Uid: 01cd4834-f23b-4f49-a121-b9f3f2113e23
Hll Key: 290745191648254730
Context Num: 1
Client Type: Other: Microsoft BITS/7.8
Precise Error: body filter failed in response
Proxied Source IP: 10.X.X.X
Reason: Application Control - HTTP parsing error occurred (2)
Action Reason: Blocking request as configured in engine settings of Application Control
Last Hit Time: 2025-05-28T12:18:40Z
Action: Block
Policy Name: RM2-Cluster-Policy
Policy Management: XX-FW-001
Db Tag: {2270F3A2-DE15-6440-9109-8B54430AD2B9}
Policy Date: 2025-05-28T11:45:24Z
Blade: Firewall
Origin: XX-RM2-FW01
Service: TCP/80
Product Family: Access
Logid: 15
Resource: http://au.download.windowsupdate.com/c/msdownload/update/software/secu/2025/05/windows10.0-kb5058383...
Access Rule Name: LAN
Access Rule Number: 35
Policy Rule UID: 595c5776-d1f0-4dec-9352-944d2eeefd8f
Layer Name: Application & URL
Interface: bond1
Description: http Traffic Blocked from XX Helpdesk (XX-helpdesk@XX.local)(10.X.X.X) to 199.X.X.X
Type: Connection, Alert
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There's an SK for this particular issue: https://support.checkpoint.com/results/sk/sk182330
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
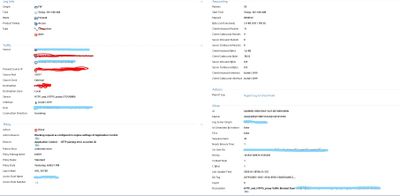
@PhoneBoy i hv flowed the SK182330 and applied the policy but after policy installation success we hv got some succeeded with warning massage ..fyi, snap attached.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is warning you that some of the Application Control signatures you've specified require HTTPS Inspection to be enabled and it's not on one of your gateways.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@PhoneBoy thnks
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Wed 16 Jul 2025 @ 10:00 AM (CEST)
Master GCP Security with the Cloud Architects Series (Multilingual Webinar)Wed 16 Jul 2025 @ 04:00 PM (CEST)
Operationalizing Threat Intelligence, Part II: Threat Hunting & Incident ResponseTue 22 Jul 2025 @ 10:00 AM (CEST)
Cyber Security Training in the Era of AI Threats: Managed SmartAwareness Explained - EMEATue 22 Jul 2025 @ 05:00 PM (CEST)
Cyber Security Training in the Era of AI Threats: Managed SmartAwareness Explained - AMERThu 31 Jul 2025 @ 10:00 AM (CEST)
CloudGuard Network Security for Nutanix - Full Deployment with Tenant & Transit VPC - EMEA/APACWed 16 Jul 2025 @ 04:00 PM (CEST)
Operationalizing Threat Intelligence, Part II: Threat Hunting & Incident ResponseTue 22 Jul 2025 @ 10:00 AM (CEST)
Cyber Security Training in the Era of AI Threats: Managed SmartAwareness Explained - EMEATue 22 Jul 2025 @ 05:00 PM (CEST)
Cyber Security Training in the Era of AI Threats: Managed SmartAwareness Explained - AMERThu 31 Jul 2025 @ 10:00 AM (CEST)
CloudGuard Network Security for Nutanix - Full Deployment with Tenant & Transit VPC - EMEA/APACThu 31 Jul 2025 @ 05:00 PM (CEST)
CloudGuard Network Security for Nutanix - Full Deployment with Tenant & Transit VPC - AMER/EMEAAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter