- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Quantum Spark Management Unleashed!
Check Point Named Leader
2025 Gartner® Magic Quadrant™ for Hybrid Mesh Firewall
HTTPS Inspection
Help us to understand your needs better
CheckMates Go:
SharePoint CVEs and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Threat Prevention
- :
- Zero Phishing - will it work without FQDN configur...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
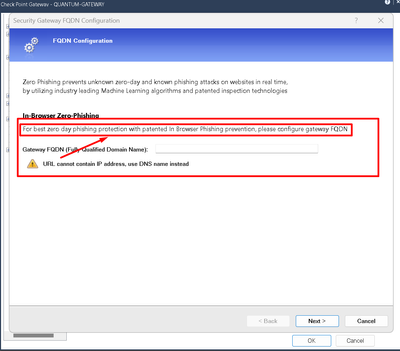
Zero Phishing - will it work without FQDN configured on SecGW?
Hi,
Testing the 81.20 in the lab and since there's no FQDN configured on SecGW the JS script won't load to the browser (fails to resolve)
So is it a hard requirement? There's no mention of it in the documentation that I could find...
I've setup a hostname via Gaia portal but that didn't fix it.
UPDATE:
After standing up a DNS server browser still can't download the script.
this time error is
GET https://server.checkpoint.local/zph/js/zp.js?api_key={XXXXXXX-0002-5648-A0A0-XXXXXXXX} net::ERR_CONNECTION_REFUSED
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi there jdoe1979,
FQDN is currently required for the full operation of the blade.
You can enable Zero Phishing without HTTPSi but that would negate most of the benefit the blade provides as most websites are HTTPS nowadays.
If you want to fix your issue in the lab, you can either configure a new record in your DNS server so the end clients will be able to resolve the FQDN entered in Zero Phishing configuration or you can manually edit the hosts file on your client/s with the FQDN you entered in Zero Phishing configuration and the IP of the interface facing the client.
We are working on a solution that will require no configuration from the admin and it will just be click and play, so to speak.
Let me know if you have any more questions.
Thanks,
Hertsel
20 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Maybe someone from CP can confirm, but Im 99.99% sure it is a hard requirement. I will try "crack" it in my lab as well, but no luck so far 🙂
Plus, you need https inspection for it to work to begin with, as probably 99% of the sites now days are https.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i don't mind the https but this fqdn requirement is bit odd...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just my logical thinking, but the key is what I pointed out...for BEST protection...
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
doesn't that kinda imply in browser protection can work without FQDN?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
True, I get your point, but I also get what @PhoneBoy is saying. I would confirm 100% with TAC, though Im fairly certain zero phishing will never work without valid FQDN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can overcome this by typing www.google.com (does not even matter what website is there), but obviously it probably wont work once you push policy, because your gateway IP wont resolve to that fqdn. I may test after making the change by giving my windows VM the default gateway of my R81.20 gateway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
won't do as it will then go and GET request the script from the FQDN Url.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Agreed!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It’s expected that all security gateways and management have functional DNS server(s) configured.
This isn’t a requirement that’s specific to Zero Phishing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i mean that without domain name assigned to SecGW Zero Phishing doesn't work.
Browser fails to resolve URL to grab the script.
I got it configured, but now it's
GET https://server.checkpoint.local/zph/js/zp.js?api_key={XXXXXXX-0002-5648-A0A0-XXXXXXXX} net::ERR_CONNECTION_REFUSED
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi there jdoe1979,
FQDN is currently required for the full operation of the blade.
You can enable Zero Phishing without HTTPSi but that would negate most of the benefit the blade provides as most websites are HTTPS nowadays.
If you want to fix your issue in the lab, you can either configure a new record in your DNS server so the end clients will be able to resolve the FQDN entered in Zero Phishing configuration or you can manually edit the hosts file on your client/s with the FQDN you entered in Zero Phishing configuration and the IP of the interface facing the client.
We are working on a solution that will require no configuration from the admin and it will just be click and play, so to speak.
Let me know if you have any more questions.
Thanks,
Hertsel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Appreciate the clarification,
What about the error message I'm seeing?
GET https://server.checkpoint.local/zph/js/zp.js?api_key={XXXXXXX-0002-5648-A0A0-XXXXXXXX} net::ERR_CONNECTION_REFUSED
That's after standing up a DNS server and configuring FQDN on SecGW
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey jdoe1979,
Are you able to test the ZPH portal on the GW using the test URL - https://<FQDN>/zph/zp-test.html
If you are able to access it, run a test to check the feature works correctly with the following website - https://zp-demo.com/verification/zphi_check.html
If any of those fail, I suggest to open a ticket with support for further debugging.
Let me know how it goes.
Thanks,
Hertsel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yeah so it's not working and I got sent to
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
And tada - ZPH doesn't work without Public IP.
This is truly an alpha release feature...
I'm gonna wait till they actually get this thing documented and running as prescribed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The way I read this SK is that the limitation itself comes from the browser, not something we impose as a result of our implementation.
And it only applies to HTTP (not HTTPS) traffic.
Which means a TAC case is definitely in order here so we can see what's really going on.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for that explanation @Sprunknwn . I think its great info when someone asks about it.
Have a nice day!
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
We are currently working on enabling the Zero Phishing blade. However, our organization does not use FQDNs. Has there been any update or change in functionality that allows Zero Phishing to work without relying on FQDNs?
thnx
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Im fairly positive it canNOT work without fqdn.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Okay. thnx Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Of course! Just tested in R82 lab and did not work, so Im 10% sure it needs fqdn.
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 1 | |
| 1 |
Upcoming Events
Wed 17 Sep 2025 @ 04:00 PM (AEST)
Securing Applications with Check Point and AWS: A Unified WAF-as-a-Service Approach - APACWed 17 Sep 2025 @ 03:00 PM (CEST)
Securing Applications with Check Point and AWS: A Unified WAF-as-a-Service Approach - EMEAThu 18 Sep 2025 @ 03:00 PM (CEST)
Bridge the Unmanaged Device Gap with Enterprise Browser - EMEAThu 18 Sep 2025 @ 02:00 PM (EDT)
Bridge the Unmanaged Device Gap with Enterprise Browser - AmericasWed 17 Sep 2025 @ 04:00 PM (AEST)
Securing Applications with Check Point and AWS: A Unified WAF-as-a-Service Approach - APACWed 17 Sep 2025 @ 03:00 PM (CEST)
Securing Applications with Check Point and AWS: A Unified WAF-as-a-Service Approach - EMEAThu 18 Sep 2025 @ 03:00 PM (CEST)
Bridge the Unmanaged Device Gap with Enterprise Browser - EMEAThu 18 Sep 2025 @ 02:00 PM (EDT)
Bridge the Unmanaged Device Gap with Enterprise Browser - AmericasMon 22 Sep 2025 @ 03:00 PM (CEST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh Security EMEAAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter