Your question is covered by the new 2-day Check Point Threat Prevention Specialist class which was just released to the ATCs this week.
Your first example will exempt all matching traffic from any Threat Prevention deep inspection whatsoever and improve performance at the cost of security. This approach is also called a "null profile". The only thing to watch out for here is that if you have more than one Threat Prevention layer (not common), you need to ensure the null profile rule appears at the top of all TP layers.
The other option is to do a blade-based global exception like this which will achieve exactly the same effect (include Zero Phishing if you are on R81.20+):
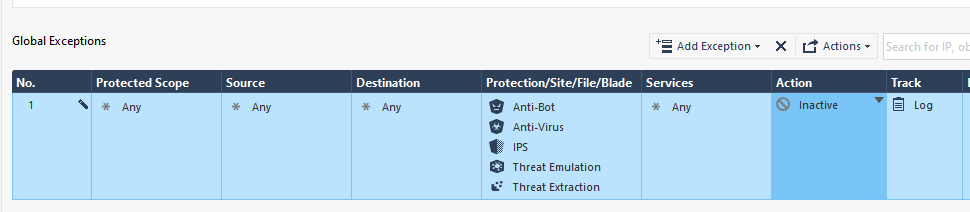
In my opinion this would be the preferred technique as the global exception will apply across all TP layers, it keeps your main TP policy concise, and is a little easier to understand.
However your example of leaving Protection/Site/File/Blade as "N/A" in the exception I'm not completely sure about. Inactive does not always mean what you think it means, if you put a signature/protection in Protection/Site/File/Blade and set the action to Inactive, the firewall is still expending the overhead to find that signature but just ignoring it if it is found. I'll have to test leaving it at N/A in my Gateway Performance Optimization Class lab and update the thread. But I know for sure the blade-based exception shown above will do what you want.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course





