- CheckMates
- :
- Products
- :
- Quantum
- :
- Threat Prevention
- :
- Re: IPS conditions to generate alert
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
IPS conditions to generate alert
Hi,
I have a doubt. Is there any way we can validate the conditions of an IPS protections? I have found some false positives in IPS signatures, and I would like to see the reason (conditions) for generating alert.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would love to see this too. Our legacy IPS solution permitted this which made troubleshooting potential false positives immensely easier.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
What do you mean by "Our legacy IPS solution permitted this which made troubleshooting potential false positives immensely easier."? Which solution?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Omer,
The legacy product I am thinkin of is the old Cisco IPS (IronPort) system. It allowed you to drill into the details of a signature that showed the specific pattern being looked for, often a REGEX statement (this could even be edited at your own risk). It would also show the part of the packet that matched this in an alert, I think they called this "context data". Overall it was a clunky, tedious system but these features were very helpful in troubleshooting.
Cisco's current Firepower solution allows viewing rule match conditions as it is based on Snort. Of course you can also create your own rules and upload them, much like you can with Checkpoint.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you have (suspected) false positives, please take relevant packet captures and open a TAC case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Agree with Dameon that IPS packet captures are the best way to figure out false positives, however there are definitely some things to be aware of when taking packet captures with IPS, the following is from my IPS Immersion class:
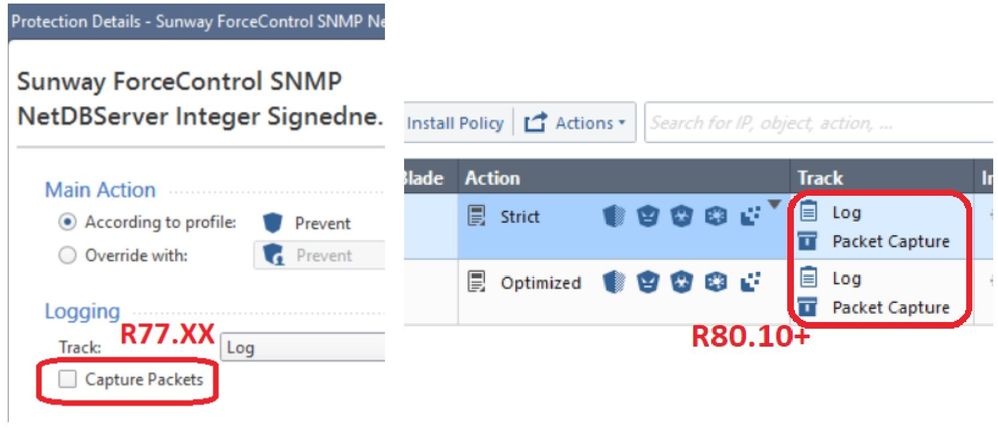
• Note that specifying a Packet Capture to be taken every time an IPS Protection is matched differs depending on the GATEWAY version.
• For R77.XX gateways, the setting is located on the IPS Protection itself.
• For R80.10+ gateways, the setting is located in the Track field of the TP policy rule.
• The packet capture can be downloaded from the IPS log entry itself on the Logs & Monitor tab in the SmartConsole; format will be EML containing a pcap.
• The first time a ThreatCloud IPS Protection is matched and the logging of it is not suppressed (i.e. a completely new IPS log entry is created), a packet capture will automatically be taken by default regardless of the settings on the prior page.
• Note that unless a packet capture is called for at all times on the IPS Protection itself (R77.XX gateway) or the Track column of the TP policy (R80.10+) gateway, only one packet capture per ThreatCloud IPS Protection will be stored by default. So only the latest non–suppressed log entry for a ThreatCloud IPS Protection will have a packet capture available by default.
• Typically the packet captured will be only the single “offending” packet and not include any prior packets in the stream, unless the attack pattern spanned more than one packet.
• Packet Captures are not supported on Gaia Embedded appliances (models 600–1400).
• Specifying Packet Capture in the Track field of a TP rule applied to a R77.XX gateway will NOT cause the IPS blade to take packet captures for all ThreatCloud IPS Protections that are matched. The Packet Capture checkbox must still be selected directly on the desired IPS Protection(s) for an R77.XX gateway.
• For R77.XX gateways, the IPS packet captures are stored locally on the gateway itself in directory $FWDIR/log/captures_repository. By default up to 500 MBytes of disk storage may be consumed by packet captures in a rotating buffer.
• For R80.10+ gateways, IPS packet captures are automatically transferred to the Log Server (usually the SMS or CMA) and stored in the $FWDIR/log/forensics and /var/spool/mail directories.
• For IPS Core Activations and Inspection Settings, packet captures will not be taken at all regardless of gateway version, unless the Capture Packets checkbox is explicitly set on the configuration screen of the individual Core Activation or Inspection Setting itself.
now available at maxpowerfirewalls.com