- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Detecting Threats Across the Open, Deep
and Dark Web With Infinity ERM
Four Ways to SASE
It's Here!
CPX 2025 Content
Remote Access VPN – User Experience
Help us with the Short-Term Roadmap
CheckMates Go:
What is UPPAK?
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Threat Prevention
- :
- Re: Cannot create exception for "Phishing_website....
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Cannot create exception for "Phishing_website.mzle" protection
I am on a verge of loosing my cool after spending half a day on a seemingly trivial task of trying to create an exception for the Threat Prevention policy.
The goal is to allow my client's PCs to receive the Phishing training communication from the KnowBe4.
The vendor has three IPs but each campaign generates new resources.
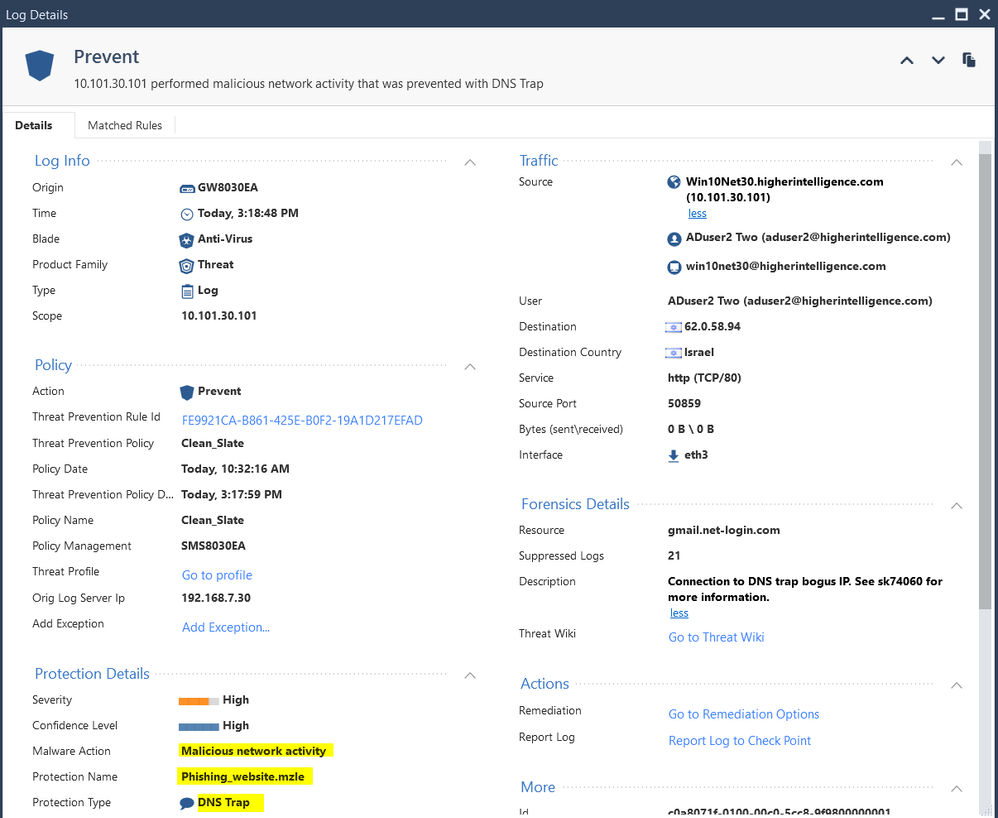
Every time client tries to go to the spoofed site, i.e. "gmail.net-login.com", the gateway promptly bags it with:
Time: 2019-04-30T19:18:48Z
Interface Direction: inbound
Interface Name: eth3
Id: c0a8071f-0100-00c0-5cc8-9f9800000001
Sequencenum: 1
Threat Prevention Policy: Clean_Slate
Threat Prevention Policy Date:2019-04-30T19:17:59Z
Source: 10.101.30.101
Source Port: 50859
Destination Country: Israel
Destination: 62.0.58.94
Destination Port: 80
IP Protocol: 6
Session Identification Number:0x5cc89f98,0x1,0x1f07a8c0,0xc0000001
Protection Name: Phishing_website.mzle
Description: Connection to DNS trap bogus IP. See sk74060 for more information.
Confidence Level: High
Severity: High
Malware Action: Malicious network activity
Protection Type: DNS Trap
Threat Prevention Rule Id: FE9921CA-B861-425E-B0F2-19A1D217EFAD
Protection ID: 0018B6567
Log ID: 2
Scope: 10.101.30.101
Source User Name: ADuser2 Two (aduser2@higherintelligence.com)
Source Machine Name: win10net30@higherintelligence.com
User: ADuser2 Two (aduser2@higherintelligence.com)
Action: Prevent
Type: Log
Policy Name: Clean_Slate
Policy Management: SMS8030EA
Db Tag: {BAC69145-F44A-4148-9603-7CEBB47B7A42}
Policy Date: 2019-04-30T14:32:16Z
Blade: Anti-Virus
Origin: GW8030EA
Service: TCP/80
Product Family: Threat
Resource: gmail.net-login.com
Marker: @A@@B@1556596801@C@31302
Log Server Origin: 192.168.7.30
Orig Log Server Ip: 192.168.7.30
Index Time: 2019-04-30T19:19:54Z
Lastupdatetime: 1556651989000
Lastupdateseqnum: 1
Rounded Sent Bytes: 0
Rounded Bytes: 0
Stored: true
Rounded Received Bytes: 0
Suppressed Logs: 21
Sent Bytes: 0
Received Bytes: 0
Interface: eth3
Description: 10.101.30.101 performed malicious network activity that was prevented with DNS Trap
Threat Profile: Go to profile
Bytes (sent\received): 0 B \ 0 B
Trying to exempt the traffic by negating the destination group in the TP rules, creating manual exemptions with either "Detect" or "Inactive", doing same by creating the exemptions from the logs, does not change the behavior. DNS trap is activated every time.
Searching for the Protection Name: "Phishing_website.mzle" in either "Protections" or IPS Protections, does not help. The thing is not there.
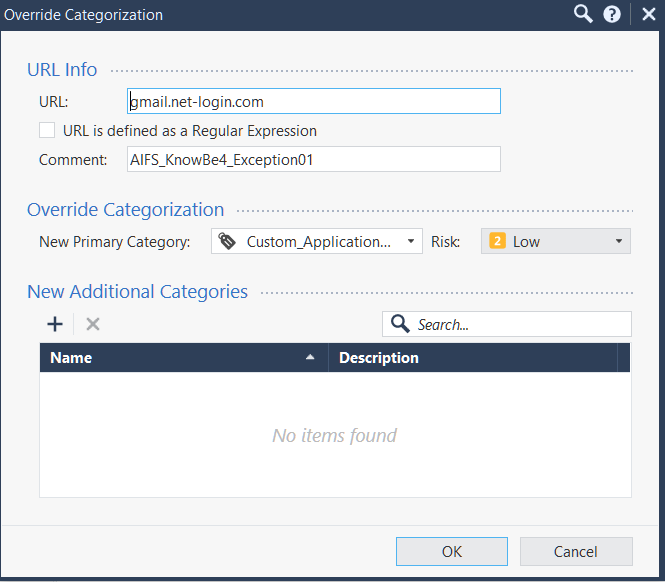
Even creating a Categorization Exception:
As unfeasible as it is for this particular task, still does not work.
HELP!!!
16 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I believe you can create a Threat Prevention rule where if the destination of the traffic is one of those specific IP addresses, the profile is a Detect only profile, inactive, or similar.
Have you tried that?
Have you tried that?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You would not believe how many different combinations of rules, policies, profiles and exceptions I have tried 🙂
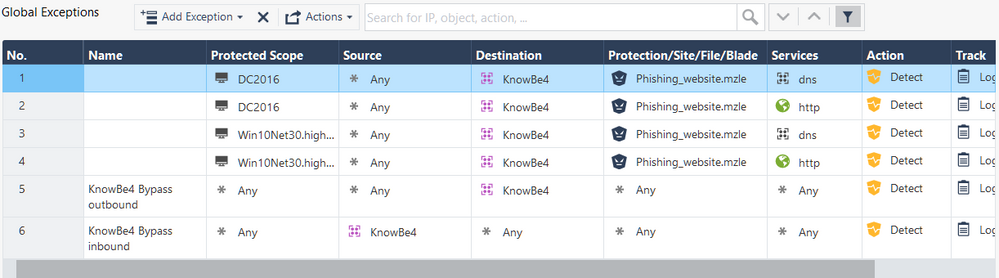
Presently, this is the policy with 2 profiles, one of them has no AV blade, as that's the one that seem to be triggering this protection, but I have tried it with single profiles with negated cells as well:
The exceptions are now in "Detect" mode, but I have tried it with "Inactive" as well:
Not to mention that the actual spoofed domain resolving to those IPs is in the "Categorization Exemption".
All of it is still does not work.
Even if it would, it is not really a long term solution for Spoofing training vendors: they spin-up instances on AWS behind dynamically allocated IPs and newly crafted domains every time.
That being said, the exemptions must work and they do not.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
P.S. I think that the best solution for all involved will be for these companies to feed their exercise domains to the Threat Cloud for whitelisting and differentiated categorization.
This way, they will not be bagged by the protections and reduce manual labor for admins fighting with this issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Vladimir
Categorization Exemption is for URLF, not AV/AB ..
After setting up all those exception experiments - what logs do you see in SmartLog? Prevent logs for what?
Maybe the issue is that you didn't exempt the internal DNS server from inspection? is there one? if so - IT asks for gmail.net-login.com's IP address and gets the bogus address...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@TP_Master , please see the very first post in this threat describing the event that I am seeing.
Of course the internal DNS forwarded itself is not exempt from overall inspection, but how does this figures into the AV triggering DNS Trap?
while gmail.net-login.com is definitely a spoofing URL, it does resolve to a number of IPs when tested from outside of Check Point protected environment.
What then decides that the returned address supposed to be replaced by the DNS Trap?
How that action could be exempt, if neither IPs nor application or URL exceptions are working?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My theory is this - the DNS request is sent from your computer to the internal DNS server. It is then forwarded by the internal DNS server to the exteranl one through the Check Point GW. *this request is found by AV and the response is with the DNS Trap bogus IP*.
Subsequently, it is sent to the computer which tries to access gmail.net-login.com but goes to the bogus IP which is blocked...
Try to add exemption for this domain when the protected scope is your internal DNS server.
Does that make sense?
Subsequently, it is sent to the computer which tries to access gmail.net-login.com but goes to the bogus IP which is blocked...
Try to add exemption for this domain when the protected scope is your internal DNS server.
Does that make sense?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@TP_Master , in this environment there is a common protection scope for the entire organization (i.e single default TP rule with scope "Any".
So the exception should, theoretically, work for both, the clients as well as internal DNS forwarders.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is actually funny: KnowBe4 emailed me response with the URLs to the txt files listing their phishing domains.
Along the way it was bagged by:
1. Office 365
2. Check Point gateway
3. Kaspersky AV on the endpoint
The only solution that did not pay any heed to this message was Check Point CloudGuard SaaS for Office 365.
Makes me wander if it is a good sign or the bad one...
I am yet to see the darned lists.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Having the same issue and CG SAAS is bagging our messages as well. We have overcome the SAAS issues but the gateway doesn't seem to like any exception we put in KB4 support is little no help
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is true if you had an exception with "any" in the scope, source and destination fields. In your screenshot there isn't one..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@TP_Master , in client's environment it is, but as you've rightly noticed, in my lab it is different.
Regardless, the problem is that the destination IPs of the spoofed domains are dynamic.
So trying to exempt them in the TP policy using scope, source and/or destination will not work.
I have to figure out how to bypass the TP based on domain names and FQDNs which TP Policy does not support and categorization exception does not work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have you tried to add a site and add it to the exception? (in the site/protection column)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have you try to disable dns trap on tp profile?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Marco_Valenti , I think KnowBe4 got this site whitelisted with the Threat Cloud, because it does not cause same issues anymore in my clients case.
Their other landing page was being blocked by Quad9 secure DNS service and I have notified KB4 about all of these issues.
Got the response that they are working with the threat intelligence vendors to get their domains cleared.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm having this same issue only with a vendor named InfoSec IQ, used to be Security IQ. Anyway, I tried basically everything you tried. I am now asking the vendor to whitelist their domains with the Threat Cloud.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We use KB4 too and this is exactly the issue I'm running into. I right clicked the Prevent log card and "added exception" and then removed the source so it is ANY, but the URL is still blocked. Based on your solution I opened a case up with KB4. I tried to get the category changed, but CP still marked it as phishing. Waiting to see if that would help or I might open a CP case up to see how I can add an exception there since our spam filter also did mark it as phishing.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |
Trending Discussions
Upcoming Events
Tue 13 May 2025 @ 04:00 PM (CEST)
German Session: NIS2- Compliance: Effiziente Vorbereitung und UmsetungTue 13 May 2025 @ 04:00 PM (CEST)
Maestro Masters EMEA: Quantum Maestro Architectures and OptimizationTue 13 May 2025 @ 02:00 PM (EDT)
Maestro Masters Americas: Quantum Maestro Architectures and OptimizationWed 14 May 2025 @ 10:00 AM (CEST)
ATAM 360°: Elevate Your Cyber Security Strategy with Proactive services - EMEAWed 14 May 2025 @ 03:00 PM (CEST)
NIS2 Readiness: Assess, Secure, and Comply with ConfidenceWed 14 May 2025 @ 10:30 AM (BRT)
Transforme sua Segurança de Rede com Agilidade e EficiênciaTue 13 May 2025 @ 04:00 PM (CEST)
Maestro Masters EMEA: Quantum Maestro Architectures and OptimizationTue 13 May 2025 @ 02:00 PM (EDT)
Maestro Masters Americas: Quantum Maestro Architectures and OptimizationWed 14 May 2025 @ 10:00 AM (CEST)
ATAM 360°: Elevate Your Cyber Security Strategy with Proactive services - EMEAWed 14 May 2025 @ 03:00 PM (CEST)
NIS2 Readiness: Assess, Secure, and Comply with ConfidenceWed 14 May 2025 @ 10:30 AM (BRT)
Transforme sua Segurança de Rede com Agilidade e EficiênciaWed 14 May 2025 @ 05:00 PM (CEST)
ATAM 360°: Elevate Your Cybersecurity Strategy with Proactive services - AMERICASThu 15 May 2025 @ 09:00 AM (IDT)
PA In-Person CloudGuard Workshop (CGNS, WAF, & API Security)About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter