- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Explore New Wave of Web Based
DDoS Attacks and Mitigations
Four Ways to SASE
It's Here!
CPX 2025 Content
Remote Access VPN – User Experience
Help us with the Short-Term Roadmap
CheckMates Go:
What is UPPAK?
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Security Gateways
- :
- "LDAP Account Unit" Username - What AD permissions...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
"LDAP Account Unit" Username - What AD permissions?
Hi all,
we have an "LDAP Account Unit" object, and in this object we have two AD servers. And this AD servers has a username in the properties:
At the moment this account has very high permissions in the AD.
But we want to decrease the permissions, so we need to know what roles this user needs.
I can't find anything in the documentations etc.
So i hope you can help me here.
Many thanks.
Best regards
Matt
Labels
- Labels:
-
Appliance
-
Identity Awareness
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Identity Collector only collects usernames from the configured AD servers.
Gateways use LDAP to query for the group, which must be configured with the relevant AD servers.
See: https://support.checkpoint.com/results/sk/sk113747 (LDAP setps also applicable for Identity Collector)
15 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hy,
I would say we need more details, like why or for what you use that AD account .
Were/are you with "AD Query" implemented on the Checkpoint ?
We're using CheckPoint Identity with Identity Collector and the account used in IC set-up and in the LDAP objects has only ad read and AD log read writes. (there is an SK that explain the rights, I'll check and come back)
Ty,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
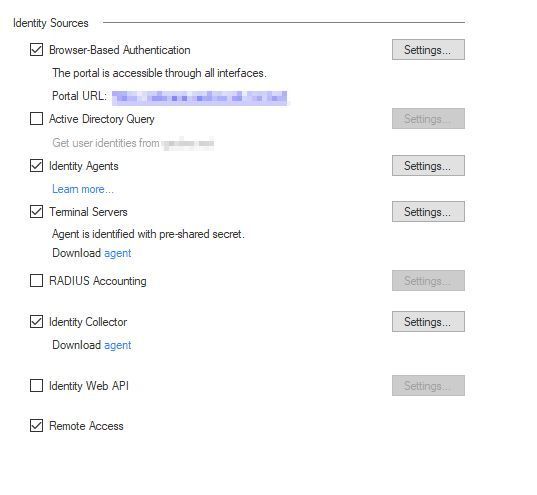
Mainly we use Identity Agents and Identity Collector:
The users have the ability to change their AD password with the Check Point Endpoint client if the password needs to be renewed. But i don't know if this is done by that user or if there is a different user managing the password change.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Timothy_Hall gave you the sk I was thinking of as well, though I will say this. I was on the phone with customer once going through that sk and we spent literally 3 hours on the line with TAC without any success. Eventually, we made it work few days later, but did not last long, so we just gave up on it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Matthew81 password change via MOB or VPN client will be done with the expired users credentials, not with the user from the ldap account unit. With the old Smartdashboard you could walk through the AD via LDAP and change the values of every AD object. To do such changes your ldap account unit user needs write rights. I think with newer Smartconsole GUI these feature is not available. And I would prefer to change anything in AD with ADs own management tools.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Short answer is that it can be a Domain Administrator, but read only.
Long answer is that you can take a regular domain user and grant it the bare minimum privileges it needs for AD Query to function. See here: sk93938: Using Identity Awareness AD Query without Active Directory Administrator privileges on Wind...
Attend my Gateway Performance Optimization R81.20 course
CET (Europe) Timezone Course Scheduled for July 1-2
CET (Europe) Timezone Course Scheduled for July 1-2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you’re using a Windows Server with the latest patches and using ADQuery, you need to use a full admin user.
However, that’s only for the WMI portion, pretty sure for LDAP you only need read only permissions to the directory.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Does a regular user with read permissions on the LDAP tree suffice for lets say, AD groups reading and VPN authentication?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
By the way, as this is CP official recommendation and I will also tell you, its super EASY to set up, if you can go with identity collector, I recommend it 100%, Im positive you will like it much better.
Happy to show you basics of it in my lab if you like.
Andy
https://support.checkpoint.com/results/sk/sk108235
Also, even though its not mentioned in the sk, but you can easily install the software on windows 10 and 11, works with no issues, though maybe I would not in production, as its not officially stated as supported : - )
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you all.
We will try with read only and see what happens 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Having migrated to Identity Collectors (BTW that sk above doesn't seem to exist anymore) and it is working perfectly. The LDAP account unit is still in the configuration on the gateway object (Identity Collector --> Authentication settings). Is this account used by the gateway to retrieve user info and/or roles ? I suppose the Identity Collectors are responsable for this ?
How do I check if the account is actually retrieving the correct user info if i.e. a new server (Domain Controller) is added ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Identity Collector only collects usernames from the configured AD servers.
Gateways use LDAP to query for the group, which must be configured with the relevant AD servers.
See: https://support.checkpoint.com/results/sk/sk113747 (LDAP setps also applicable for Identity Collector)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Dameon. My assumptions confirmed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
There is a new SK which states what rights are needed for the LDAP Account Unit account, if you are using Identity Collector.
sk182905 - Non-Admin service account for LDAP AU (Account Unit) with Identity collector
https://support.checkpoint.com/results/sk/sk182905
Date Created 2024-12-06
Regards
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Domain Users, as I understand it from reading the relevant Microsoft documentation, is something all users created on an AD domain get added to by default.
From reviewing the SR associated with the SK, it's not clear why this is required, but the request was for the requirement to be formally documented (it wasn't before).
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 30 | |
| 14 | |
| 10 | |
| 8 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 3 |
Upcoming Events
Tue 13 May 2025 @ 04:00 PM (CEST)
German Session: NIS2- Compliance: Effiziente Vorbereitung und UmsetungTue 13 May 2025 @ 04:00 PM (CEST)
Maestro Masters EMEA: Quantum Maestro Architectures and OptimizationTue 13 May 2025 @ 02:00 PM (EDT)
Maestro Masters Americas: Quantum Maestro Architectures and OptimizationWed 14 May 2025 @ 10:00 AM (CEST)
ATAM 360°: Elevate Your Cyber Security Strategy with Proactive services - EMEAWed 14 May 2025 @ 03:00 PM (CEST)
NIS2 Readiness: Assess, Secure, and Comply with ConfidenceWed 14 May 2025 @ 10:30 AM (BRT)
Transforme sua Segurança de Rede com Agilidade e EficiênciaTue 13 May 2025 @ 04:00 PM (CEST)
Maestro Masters EMEA: Quantum Maestro Architectures and OptimizationTue 13 May 2025 @ 02:00 PM (EDT)
Maestro Masters Americas: Quantum Maestro Architectures and OptimizationWed 14 May 2025 @ 10:00 AM (CEST)
ATAM 360°: Elevate Your Cyber Security Strategy with Proactive services - EMEAWed 14 May 2025 @ 03:00 PM (CEST)
NIS2 Readiness: Assess, Secure, and Comply with ConfidenceWed 14 May 2025 @ 10:30 AM (BRT)
Transforme sua Segurança de Rede com Agilidade e EficiênciaWed 14 May 2025 @ 05:00 PM (CEST)
ATAM 360°: Elevate Your Cybersecurity Strategy with Proactive services - AMERICASThu 15 May 2025 @ 09:00 AM (IDT)
PA In-Person CloudGuard Workshop (CGNS, WAF, & API Security)About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter