- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Detecting Threats Across the Open, Deep
and Dark Web With Infinity ERM
Four Ways to SASE
It's Here!
CPX 2025 Content
Remote Access VPN – User Experience
Help us with the Short-Term Roadmap
CheckMates Go:
What is UPPAK?
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Security Gateways
- :
- Re: https inspection performance issue - F2F traff...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
https inspection performance issue - F2F traffic 82%..
we have 2x open server in cluster XL r81 with a 4x cpu license
running https://openspeedtest.com/ (run on https) we notice an important drop in terms of performance, instead of 450-500 mbps that we get from a standard speedtest liko ookla that run on port 8080 the performance drops to max 150 mbps
we investigate the https inspection module but we do not understand the following behaviour.
1) if we create a rule in first position that bypass the entire https inspection for a specific host openspeedtest run at 450 mbps but if we insert the same host in a rule in position 5 that bypass the https inspection if you're member of a group of hosts the same host run at 150 mbps.
To note that in both case the url https://openspeedtest.com/ is bypassed due his categorization..
how is possible such a performance drop based on the https rule position?
why there's such a drop considering that this service is not even inspected?
we did some debug and we notice that lot's of traffic is goes through F2F below some usefull outputs.
any suggestions? tx
[Expert@checkpoint-1:0]# fwaccel stats -s
Accelerated conns/Total conns : 135/1570 (8%)
Accelerated pkts/Total pkts : 13101094681/73808428002 (17%)
F2Fed pkts/Total pkts : 60707333321/73808428002 (82%)
F2V pkts/Total pkts : 65943865/73808428002 (0%)
CPASXL pkts/Total pkts : 16454023/73808428002 (0%)
PSLXL pkts/Total pkts : 12372846626/73808428002 (16%)
CPAS pipeline pkts/Total pkts : 0/73808428002 (0%)
PSL pipeline pkts/Total pkts : 0/73808428002 (0%)
CPAS inline pkts/Total pkts : 0/73808428002 (0%)
PSL inline pkts/Total pkts : 0/73808428002 (0%)
QOS inbound pkts/Total pkts : 0/73808428002 (0%)
QOS outbound pkts/Total pkts : 0/73808428002 (0%)
Corrected pkts/Total pkts : 0/73808428002 (0%)
[Expert@checkpoint-1:0]# fwaccel stat
+---------------------------------------------------------------------------------+
|Id|Name |Status |Interfaces |Features |
+---------------------------------------------------------------------------------+
|0 |SND |enabled |eth4,eth5,eth0,eth6,eth3 |Acceleration,Cryptography |
| | | | | |
| | | | |Crypto: Tunnel,UDPEncap,MD5, |
| | | | |SHA1,3DES,DES,AES-128,AES-256,|
| | | | |ESP,LinkSelection,DynamicVPN, |
| | | | |NatTraversal,AES-XCBC,SHA256, |
| | | | |SHA384,SHA512 |
+---------------------------------------------------------------------------------+
Accept Templates : enabled
Drop Templates : enabled
NAT Templates : enabled
[Expert@checkpoint-1:0]#
[Expert@checkpoint-1:0]# fwaccel stats
Name Value Name Value
---------------------------- ------------ ---------------------------- ------------
Accelerated Path
--------------------------------------------------------------------------------------
accel packets 13105476237 accel bytes 9576220636092
outbound packets 13306779203 outbound bytes 9868235245852
conns created 65305430 conns deleted 65304144
C total conns 1286 C TCP conns 478
C non TCP conns 808 nat conns 31963228
dropped packets 2907232 dropped bytes 629465065
fragments received 1831431 fragments transmit 1126
fragments dropped 0 fragments expired 111439
IP options stripped 374709 IP options restored 115724
IP options dropped 0 corrs created 0
corrs deleted 0 C corrections 0
corrected packets 0 corrected bytes 0
Accelerated VPN Path
--------------------------------------------------------------------------------------
C crypt conns 115 enc bytes 201667504
dec bytes 682230912 ESP enc pkts 528421
ESP enc err 0 ESP dec pkts 708080
ESP dec err 0 ESP other err 0
espudp enc pkts 0 espudp enc err 0
espudp dec pkts 0 espudp dec err 0
espudp other err 0
Medium Streaming Path
--------------------------------------------------------------------------------------
CPASXL packets 16454121 PSLXL packets 12377039895
CPASXL async packets 16454023 PSLXL async packets 12376375499
CPASXL bytes 16508578013 PSLXL bytes 8937294264245
C CPASXL conns 3 C PSLXL conns 1157
CPASXL conns created 50783 PSLXL conns created 64697868
PXL FF conns 0 PXL FF packets 29416
PXL FF bytes 23581461 PXL FF acks 12056
PXL no conn drops 0
Pipeline Streaming Path
--------------------------------------------------------------------------------------
PSL Pipeline packets 0 PSL Pipeline bytes 0
CPAS Pipeline packets 0 CPAS Pipeline bytes 0
Inline Streaming Path
--------------------------------------------------------------------------------------
PSL Inline packets 0 PSL Inline bytes 0
CPAS Inline packets 0 CPAS Inline bytes 0
Buffer Path
--------------------------------------------------------------------------------------
Buffer path buffers 0 Buffer path bytes 0
TLS PARSER
--------------------------------------------------------------------------------------
RECORD INFO 0
TLS DECRYPT
--------------------------------------------------------------------------------------
TLS INSPECTION 0 TLS HANDSHAKE 0
TLS RECORD LAYER 0 TLS CRYPTO 0
HTTP DISP
--------------------------------------------------------------------------------------
ACTIVATE WS MAIN 0 EXEC NO HTTP CMI CONTEXT 0
WS LITE
--------------------------------------------------------------------------------------
WS TX COMPLETED 0 WS FORWARD TO MAIN 0
WS NOTIFY TIMEOUT 0 WS HANDLE EVENT 0
WS CHUNKED ERROR 0 WS GZIP EVENT 0
WS ADD MAC HEADER 0 WS IS STICKY ACTIVE 0
WS TIER1 JOB ERROR 0 WS TIER1 HAS MATCHES 0
CML MATCHES 0 TOTAL UPLOADED JOBS 0
TOTAL JOBS 0
ADVP
--------------------------------------------------------------------------------------
ADVP FORW TO MAIN 0 ADVP HOLD TIMEOUT 0
QoS Paths
--------------------------------------------------------------------------------------
QoS General Information:
------------------------
Total QoS Conns 0 QoS Classify Conns 0
QoS Classify flow 0 Reclassify QoS policy 0
FireWall QoS Path:
------------------
Enqueued IN packets 0 Enqueued OUT packets 0
Dequeued IN packets 0 Dequeued OUT packets 0
Enqueued IN bytes 0 Enqueued OUT bytes 0
Dequeued IN bytes 0 Dequeued OUT bytes 0
Accelerated QoS Path:
---------------------
Enqueued IN packets 0 Enqueued OUT packets 0
Dequeued IN packets 0 Dequeued OUT packets 0
Enqueued IN bytes 0 Enqueued OUT bytes 0
Dequeued IN bytes 0 Dequeued OUT bytes 0
Firewall Path
--------------------------------------------------------------------------------------
F2F packets 60736129970 F2F bytes 50320444505511
TCP violations 16 F2V conn match pkts 703989
F2V packets 65971694 F2V bytes 5570164544
GTP
--------------------------------------------------------------------------------------
gtp tunnels created 0 gtp tunnels 0
gtp accel pkts 0 gtp f2f pkts 0
gtp spoofed pkts 0 gtp in gtp pkts 0
gtp signaling pkts 0 gtp tcpopt pkts 0
gtp apn err pkts 0
General
--------------------------------------------------------------------------------------
memory used 103915120 C tcp handshake conns 14
C tcp established conns 454 C tcp closed conns 10
C tcp pxl handshake conns 14 C tcp pxl established conns 351
C tcp pxl closed conns 10 DNS DoR stats 291
(*) Statistics marked with C refer to current value, others refer to total value
[Expert@checkpoint-1:0]#
ragione del non accelerazione
[Expert@checkpoint-1:0]# fwaccel stats -p
F2F packets:
--------------
Violation Packets Violation Packets
-------------------- --------------- -------------------- ---------------
Pkt has IP options 374766 ICMP miss conn 249518305
TCP-SYN miss conn 215843802 TCP-other miss conn 29156577762
UDP miss conn 920603464 Other miss conn 5798272
VPN returned F2F 128716 Uni-directional viol 0
Possible spoof viol 0 TCP state viol 547
SCTP state affecting 0 Out if not def/accl 0
Bridge src=dst 0 Routing decision err 0
Sanity checks failed 0 Fwd to non-pivot 0
Broadcast/multicast 0 Cluster message 109434977
Cluster forward 635 Chain forwarding 0
F2V conn match pkts 705245 General reason 0
Route changes 0 VPN multicast traffic 0
GTP non-accelerated 0 Unresolved nexthop 38438
[Expert@checkpoint-1:0]# fwaccel stats -t
F2Fed bytes/Total bytes : 50329254032099/59906647972752 (84%)
F2V bytes/Total bytes : 5571144798/59906647972752 (0%)
Medium path bytes/Total bytes : 8954924374718/59906647972752 (14%)
Pipeline path bytes/Total bytes : 0/59906647972752 (0%)
Inline path bytes/Total bytes : 0/59906647972752 (0%)
Buffer path bytes/Total inline bytes: 0/0 (0%)
[Expert@checkpoint-1:0]# fwaccel stats -p
F2F packets:
--------------
Violation Packets Violation Packets
-------------------- --------------- -------------------- ---------------
Pkt has IP options 408329 ICMP miss conn 272317499
TCP-SYN miss conn 239969254 TCP-other miss conn 31278648253
UDP miss conn 1009197422 Other miss conn 6353935
VPN returned F2F 129009 Uni-directional viol 0
Possible spoof viol 0 TCP state viol 634
SCTP state affecting 0 Out if not def/accl 0
Bridge src=dst 0 Routing decision err 0
Sanity checks failed 0 Fwd to non-pivot 0
Broadcast/multicast 0 Cluster message 119931860
Cluster forward 635 Chain forwarding 0
F2V conn match pkts 1053535 General reason 0
Route changes 0 VPN multicast traffic 0
GTP non-accelerated 0 Unresolved nexthop 62227
[Expert@checkpoint-1:0]# fw ctl affinity -l -r
CPU 0:
CPU 1: fw_1 (active)
mpdaemon fwd rad lpd rtmd wsdnsd in.asessiond core_uploader cprid usrchkd vpnd in.acapd pepd pdpd cprid cpd
CPU 2:
CPU 3:
CPU 4:
CPU 5:
CPU 6:
CPU 7:
CPU 8:
CPU 9: fw_0 (active)
mpdaemon fwd rad lpd rtmd wsdnsd in.asessiond core_uploader cprid usrchkd vpnd in.acapd pepd pdpd cprid cpd
CPU 10:
CPU 11:
CPU 12:
CPU 13:
CPU 14:
CPU 15:
All:
The current license permits the use of CPUs 0, 1, 8, 9 only.
Interface eth4: has multi queue enabled
Interface eth5: has multi queue enabled
Interface eth0: has multi queue enabled
Interface eth6: has multi queue enabled
Interface eth3: has multi queue enabled
[Expert@checkpoint-1:0]# fw ctl multik stat
ID | Active | CPU | Connections | Peak
----------------------------------------------
0 | Yes | 9 | 5940 | 11921
1 | Yes | 1 | 6379 | 13536
[Expert@checkpoint-1:0]# enabled_blades
fw vpn urlf av appi ips identityServer SSL_INSPECT anti_bot mon
38 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You said R81, what JHF level?
The fact you see this issue when you put the host in Rule 5 (versus as a separate rule up top) suggests that the rules before Rule 5 are potentially problematic.
Please provide the precise rules used in your HTTPS Inspection policy (specifically up to and including Rule 5)..
Note that, in general, bypass rules should be listed first.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
r81 take 77
the problem seems not related to the https rules order. the rule set is very simple with rules 1 to 5 that bypass several hosts by source, by destination ip or by url then we have an ispection rule for some dangerous categories and at the end the bypass for any as suggested in the following link
Solved: Re: HTTPS Inspection Setup - Check Point CheckMates
the problem cause seems related to the high percentage of traffic that pass through the slow path.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sk32578 describes common scenarios causing F2F traffic processing e.g. PPPoE connections and the use of certain object types / IPS protections (sk105079) etc.
As Tim said high F2F stats are also expected on a standby member of a cluster.
SQLNET2 traffic may also be a factor per sk179919.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Recommend reviewing HTTPS inspection policy structure per the recommendations here & here to start.
Refer also:
sk98871 : HTTP-based speed test shows strong degradation in download speed when Anti-Virus is set to inspect all HTTP and HTTPS traffic
sk163595 : HTTPS Inspection bypass list object
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
the problem seems not related to the https rules order. the rule set is very simple with rules 1 to 5 that bypass several hosts by source, by destination ip or by url then we have an ispection rule for some dangerous categories and at the end the bypass for any as suggested in the following link
Solved: Re: HTTPS Inspection Setup - Check Point CheckMates
the problem cause seems related to the high percentage of traffic that pass through the slow path.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As I mentioned earlier HTTPS Inspection by itself does not typically cause high F2F. It is almost certainly due to the configuration of your IPS blade. Try the following technique which is mentioned in my Gateway Performance Optimization Course during your firewall's busiest period if possible, keeping in mind doing so may expose your organization to attacks, use at your own risk!
fwaccel stats -s (note F2F percentage)
ips off -n
fwaccel stats -r
(wait 120 seconds)
fwaccel stats -s (has F2F dropped substantially? If so IPS is to blame)
ips on
Attend my Gateway Performance Optimization R81.20 course
CET (Europe) Timezone Course Scheduled for July 1-2
CET (Europe) Timezone Course Scheduled for July 1-2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i reset the stats, disabled ips but I still have 78% F2F
as you see I can't run the hcp for TP so I run all available tests
[Expert@checkpoint-1:0]# hcp --enable-product "Threat Prevention"
[Expert@checkpoint-1:0]# hcp -r "Threat Prevention"
Requested test cannot be executed on current system. Please run 'hcp -r all' to see the results for all available tests.
[Expert@checkpoint-1:0]# hcp -r all
Test name Status
============================================================
ARP Cache Limit...................................[PASSED]
Bond Health.......................................[SKIPPED]
CPview Diagnostic.................................[INFO]
Check Point Processes.............................[PASSED]
Cluster...........................................[PASSED]
Connectivity to UC................................[PASSED]
Core Dumps........................................[ERROR]
Custom Applications RegEx.........................[PASSED]
Debug flags - FW..................................[PASSED]
Debug flags - fwaccel.............................[ERROR]
Disk Space........................................[PASSED]
Dynamic Objects Database..........................[PASSED]
FW Configuration File Sanity......................[ERROR]
FW tables limit...................................[ERROR]
File Descriptors..................................[PASSED]
Gaia DB...........................................[PASSED]
Hardware validation...............................[PASSED]
IPv4 forwarding...................................[PASSED]
Identity Awareness - Sharing mechanism error......[PASSED]
Identity Awareness - tables limit.................[PASSED]
Identity Awareness - tables mismatch..............[PASSED]
Interface Errors..................................[ERROR]
Kernel crash......................................[PASSED]
Local Logging.....................................[PASSED]
MAC magic.........................................[ERROR]
MTU...............................................[PASSED]
Memory Usage......................................[PASSED]
Neighbour table overflow..........................[PASSED]
SIM Configuration File Sanity.....................[PASSED]
SSD Health........................................[ERROR]
SecureXL status...................................[PASSED]
Soft lockup.......................................[PASSED]
Software Version..................................[PASSED]
Transceivers Support..............................[PASSED]
Zombie processes..................................[PASSED]
Generating Topology...............................[Done]
Generating Story..................................[Done]
Generating Charts.................................[Done]
any suggestions?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Those "Threat Prevention" reports won't work on any version lower than R81.20.
also, look into the errors you already have
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
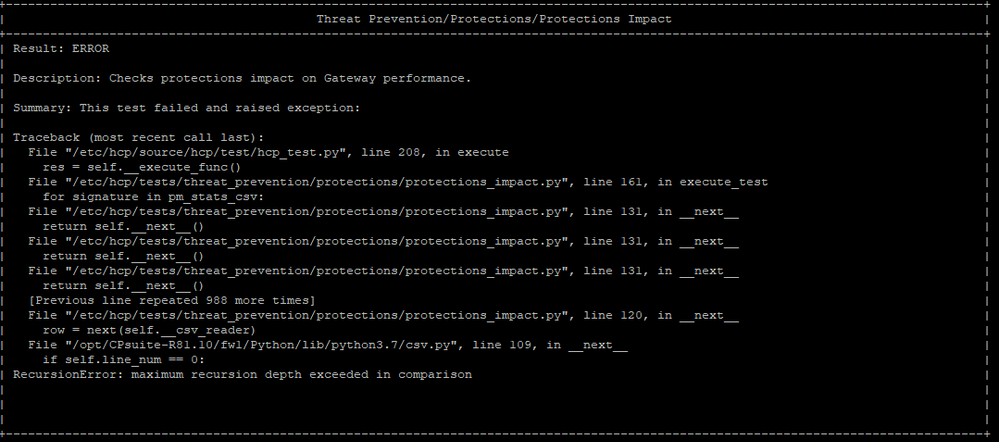
It does run on R81.10 JHF78.
Although with a recursion error meant to be fixed in the next release, as stated by an employee in this post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@_Val_ ...Are you 100% sure thats the case? We had clients run them back in R80.20 and worked just fine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
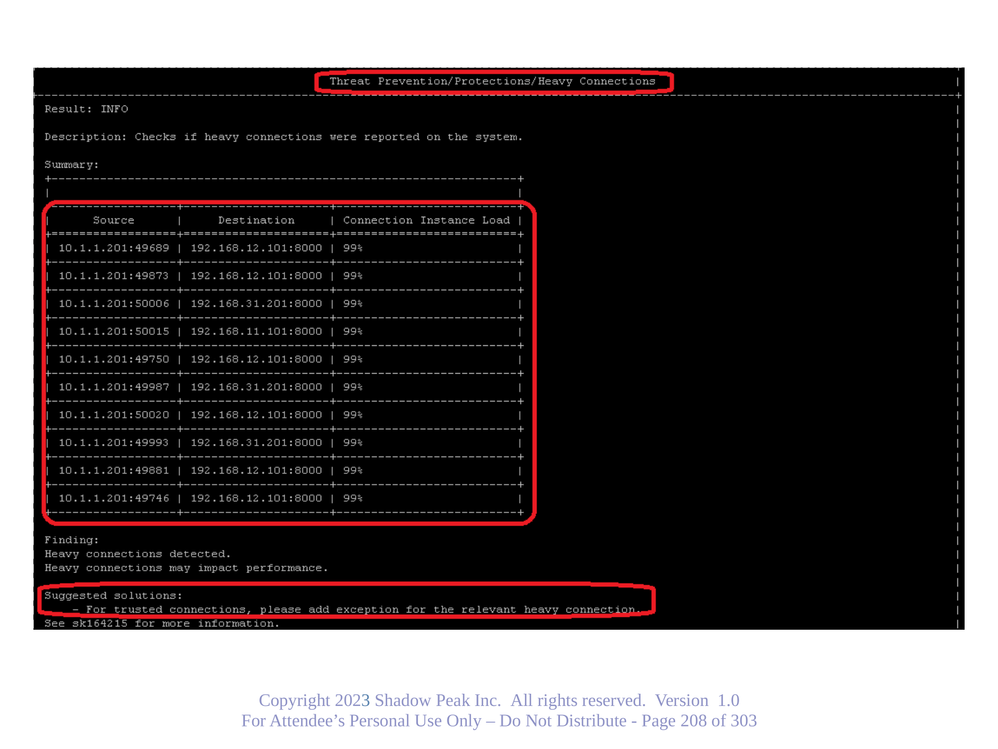
Next step to determine mysterious F2F is a debug, schedule a maintenance window for this! First determine a connection and its attributes that always seems to go F2F using some of the commands I mentioned earlier in this thread like fw_mux all. Let's suppose that it is traffic sourced from 10.1.1.201 to both destinations 192.168.11.101 and 192.168.12.101 on port 8000. The following commands are from my Gateway Optimization Course and are run in a live lab exercise:
fw ctl debug 0
fw ctl debug -buf 8192
fw ctl set str simple_debug_filter_saddr_1 10.1.1.201
fw ctl set str simple_debug_filter_daddr_1 192.168.11.101
fw ctl set str simple_debug_filter_daddr_2 192.168.12.101
fw ctl set int simple_debug_filter_dport_1 8000
fw ctl debug -m fw + connstats
fw ctl kdebug -T -f > /var/log/f2f.log (this command will run until manually terminated)
Start a NEW connection going F2F matching this criteria. Once this has been done run fw ctl debug 0 (VERY IMPORTANT). Now grep the output f2f.log file for string "accelerated, reason" to see why it went F2F (note that there must be a space character after the comma).
Attend my Gateway Performance Optimization R81.20 course
CET (Europe) Timezone Course Scheduled for July 1-2
CET (Europe) Timezone Course Scheduled for July 1-2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i run the debug as you explained
traffic is not accelerated, reason="SPII active"
what does it mean?
@;1827982694;13Feb2023 15:10:37.615351;[cpu_1];[fw4_1];fwconn_stats_opq_update_offload_stats: connection stats app updated successfully. conn <dir 0, 192.168.111.154:61576 -> 172.115.78.107:443 IPP 6> is not accelerated, reason="SPII active", sxl_dev_id=4;
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
An IPS ThreatCloud Protection, Core Activation, or even an Inspection Setting is calling for inspection that must occur in the Medium Path which is preventing full acceleration; it has nothing to do with HTTPS Inspection beyond making the decrypted traffic available to be scanned by the IPS blade. Any signature with a Performance Impact of Medium/High/Critical could be causing it. You could use fast_accel to force this traffic into the fully-accelerated path if you want sk156672: SecureXL Fast Accelerator (fw fast_accel) for R80.20 and above. If you have stopped IPS with the ips off command and the traffic is still not accelerated in your debug, it is likely an Inspection Setting that is the culprit.
Attend my Gateway Performance Optimization R81.20 course
CET (Europe) Timezone Course Scheduled for July 1-2
CET (Europe) Timezone Course Scheduled for July 1-2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not trying to hijack your post but to add that I am having a similar issue and might be related.
Env:
Maestro R81.10 JHF 78
Mostly all blades enabled AND HTTPSi
Issue:
Usually F2F 95%
Have unloaded amw policy and checked stats and it certainly decreases, but F2F still around 65%, too much.
Main violation is TCP-other miss conn
In cpview, offload decision says SPII Active
Run debug:
fwaccel dbg + offload
fwaccel dbg + pkt + f2f
And I see:
;cphwd_chain_to_vm_connkey: obtained vm_connkey <dir 1, x:58180 -> x:443 IPP 6>;
@;235926526; 8Feb2023 15:47:37.404890;[vs_0];[tid_2];[fw4_2];cphwd_chain_to_vm_connkey: obtained vm_connkey <dir 1, x:58180 -> 52.97.211.226:443 IPP 6>;
@;235926526; 8Feb2023 15:47:37.404895;[vs_0];[tid_2];[fw4_2];cpxl_chain_handler: entered (conn <dir 0, 10.x7:58180 -> 52.x6:443 IPP 6>);
@;235926526; 8Feb2023 15:47:37.404897;[vs_0];[tid_2];[fw4_2];cphwd_is_conn_already_offloaded: conn_already_offloaded=0, reoffload_conn=0, created_from_template=0, policy_id=354827077, up_policy_id=1675859405;
@;235926526; 8Feb2023 15:47:37.404898;[vs_0];[tid_2];[fw4_2];cphwd_chain_to_vm_connkey: obtained vm_connkey <dir 1, 1x:58180 -> 52.x:443 IPP 6>;
@;235926526; 8Feb2023 15:47:37.404900;[vs_0];[tid_2];[fw4_2];cphwd_is_non_accelerated_conn: entered...orig_conn=<dir 0, 1x:58180 -> 52.x:443 IPP 6>, vm_conn=<dir 1, 10.x7:58180 -> 52.9x:443 IPP 6>;
@;235926526; 8Feb2023 15:47:37.404903;[vs_0];[tid_2];[fw4_2];cphwd_conn_should_accelerate_by_features: spii is active -> not offloading;
@;235926526; 8Feb2023 15:47:37.404904;[vs_0];[tid_2];[fw4_2];cphwd_handle_conn_acceleration: cphwd_conn_should_accelerate_by_features - not accelerating;
@;235926526; 8Feb2023 15:47:37.404912;[vs_0];[tid_2];[fw4_2];cpxl_chain_handler: connection <dir 0, x58180 -> 5x6:443 IPP 6> will not be accelerated;
and then for return traffic:
;pkt_handle_no_match: connection <52.x,443,10.x,55119,6> not found -> forwarding to firewall;
Flags for slow connections if it means anything to somebody
Path: Slow, InZone: INTERNAL_ZONE, OutZone: EXTERNAL_ZONE, Flags: 0x4b01
C2S side:
TCP State: PSL_TCP_ESTABLISHED, Number of segments: 0, Hold: 0, Side flags: 0x2c4
S2C side:
TCP State: PSL_TCP_ESTABLISHED, Number of segments: 0, Hold: 0, Side flags: 0x2c4
Application info:
MUX_PASSIVE, Flags: 0x13
Connection matches an HTTPSi bypass rule as well.
Currently with TAC but still early stages.. they are still beating around the bush
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SPII = IPS.
Amw unload does not stop IPS. After ips off -n and stats reset you may need to wait longer if you have long running connections as they will continue F2F until they end.
Attend my Gateway Performance Optimization R81.20 course
CET (Europe) Timezone Course Scheduled for July 1-2
CET (Europe) Timezone Course Scheduled for July 1-2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Any debug or way to find out the protection causing it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, run hcp's "secret" Threat Prevention reports:
hcp --enable-product "Threat Prevention"
hcp -r "Threat Prevention"
You may need to update to the latest version of hcp and/or these reports may not be supported on R81.10. I am currently attending CPX Denver for Partners in person and will post the relevant pages from my Gateway Performance Optimization course later today.
Attend my Gateway Performance Optimization R81.20 course
CET (Europe) Timezone Course Scheduled for July 1-2
CET (Europe) Timezone Course Scheduled for July 1-2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just to make sure, this "secret" is not much of a secret, since you just published it here, @Timothy_Hall, and also teach them in your class.
However, this specific command and some other, similar ones, are intended for TAC exclusive use. There are some performance-related reasons for that. It is an issue of responsibility and liability.
That said, some strictly internal tools of Check Point keep leaking into the public space, which is not always good and sometimes even dangerous, if used without understanding and caution (like zdebug)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for this, I was wondering if we can obtain HCP update take 59 or release 59 for troubleshooting in anyway. I got a case that is time sensitive and needs to progress.
So far all symptoms match to some IPS core protection, but we need to determine which protection is culprit. The kernel debug does show phwd_conn_should_accelerate_by_features: spii is active -> not offloading for my customer has well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
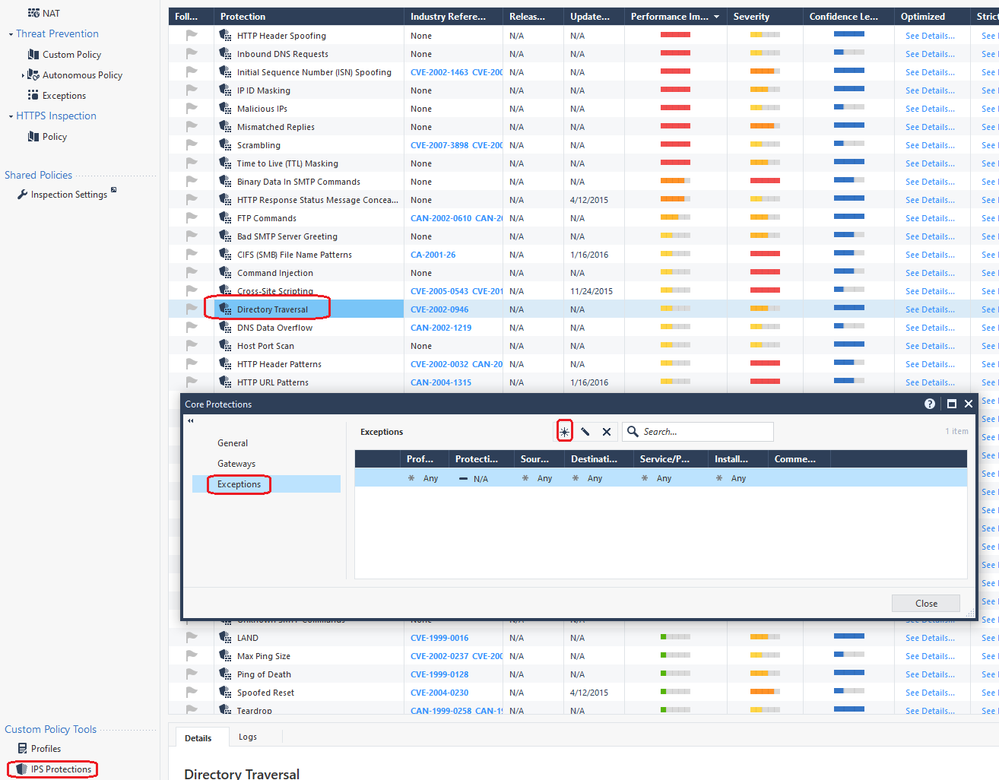
Not surprising that you suspect an IPS Core protection, those signatures have all kinds of wacky behavior. Here is a list of all the Medium or higher ones that could be causing it, you can try manually disabling these one by one:
| HTTP Header Spoofing |
| Inbound DNS Requests |
| Initial Sequence Number (ISN) Spoofing |
| IP ID Masking |
| Malicious IPs |
| Mismatched Replies |
| Scrambling |
| Time to Live (TTL) Masking |
| Binary Data In SMTP Commands |
| HTTP Response Status Message Concealment |
|
FTP Commands |
Or better yet try creating an exception for all Core Activations as shown below, but for IPS Core Activations specifically I'm not sure if the Any exception will suddenly make the traffic eligible for full acceleration, or just change the final decision from Prevent to something else and have no effect on acceleration. If you try it be sure to install both the Access Control & Threat Prevention policies after creating this exception, and note that Core Activations Fingerprint Scrambling, LAND, and teardrop will not be included in this exception and you may need to manually disable those.
Attend my Gateway Performance Optimization R81.20 course
CET (Europe) Timezone Course Scheduled for July 1-2
CET (Europe) Timezone Course Scheduled for July 1-2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here are the pages from my Gateway Performance Optimization course covering the secret hcp TP reports with screenshots, as you can see there is a vast wealth of useful information.
Attend my Gateway Performance Optimization R81.20 course
CET (Europe) Timezone Course Scheduled for July 1-2
CET (Europe) Timezone Course Scheduled for July 1-2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Same error for me.. HCP take 58 / R80.10 JHF 78
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry for the inconvenience,
We fixed the issue and it will integrated in the next HCP version (59).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thankyou, that is great.
Great product, keep up the good work
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HCP 59 was released and Threat Prevention report works 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have a few more interesting bits but still don't fully get there:
fw_spii_is_activated: spii matrix includes application not registered over PSL = 726, returning SPII is activated.;
ips_cmi_handler_match_cb_ex: conn=dir 0, 10.x.x.x:57715 -> 195.122.177.135:443 IPP 6 ctx=404 sig_id=3797 prot_id=0x655c1477 (type=1 h=1603)cmi_execute_inspect: Executing handler 'HTTP_SLOW_matchcode' (id 1603) on context 404; log_id=0 session_id=0;
ips_get_tp_action_by_prot_id: ipspkg prot_id(32bit)=0x47a40e5d severity=4 performance=5 confidence=0 flags=0xa;
fw_spii_add_inspection: SPII message writen (726, 0, 0);
So how to know what application is not registered on PSL?
Is there perhaps a table?
Is 726 a meaningful reference number?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No but 0x655c1477 and 0x47a40e5d may be, run ips protection 0x655c1477 & ips protection 0x47a40e5d to see what protections those are.
Attend my Gateway Performance Optimization R81.20 course
CET (Europe) Timezone Course Scheduled for July 1-2
CET (Europe) Timezone Course Scheduled for July 1-2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To add to what Tim gave you, below is what you need:
[Expert@quantum-firewall:0]# ips protection 0x655c1477
Web Servers Slow HTTP Denial of Service
[Expert@quantum-firewall:0]# ips protection 0x47a40e5d
TCP Window Size Enforcement
[Expert@quantum-firewall:0]#
You can also refer to post I made about it, hope it will help you.
Cheers,
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 32 | |
| 16 | |
| 11 | |
| 7 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 3 |
Upcoming Events
Wed 14 May 2025 @ 10:00 AM (CEST)
ATAM 360°: Elevate Your Cyber Security Strategy with Proactive services - EMEAWed 14 May 2025 @ 03:00 PM (CEST)
NIS2 Readiness: Assess, Secure, and Comply with ConfidenceWed 14 May 2025 @ 10:30 AM (BRT)
Transforme sua Segurança de Rede com Agilidade e EficiênciaWed 14 May 2025 @ 05:00 PM (CEST)
ATAM 360°: Elevate Your Cybersecurity Strategy with Proactive services - AMERICASThu 15 May 2025 @ 09:00 AM (IDT)
PA In-Person CloudGuard Workshop (CGNS, WAF, & API Security)Thu 15 May 2025 @ 10:00 AM (CEST)
EMEA: Spotlight on AI-Powered Cyber Security Platform Assessment 2025 - Tested By 3rd Party LabWed 14 May 2025 @ 10:00 AM (CEST)
ATAM 360°: Elevate Your Cyber Security Strategy with Proactive services - EMEAWed 14 May 2025 @ 03:00 PM (CEST)
NIS2 Readiness: Assess, Secure, and Comply with ConfidenceWed 14 May 2025 @ 10:30 AM (BRT)
Transforme sua Segurança de Rede com Agilidade e EficiênciaWed 14 May 2025 @ 05:00 PM (CEST)
ATAM 360°: Elevate Your Cybersecurity Strategy with Proactive services - AMERICASThu 15 May 2025 @ 10:00 AM (CEST)
EMEA: Spotlight on AI-Powered Cyber Security Platform Assessment 2025 - Tested By 3rd Party LabThu 15 May 2025 @ 05:00 PM (CEST)
AMER: Spotlight on AI-Powered Cyber Security Platform Assessment 2025 - Tested By 3rd Party LabThu 15 May 2025 @ 09:00 AM (IDT)
PA In-Person CloudGuard Workshop (CGNS, WAF, & API Security)About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter