- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure Users and Access)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
May the 4th (+4)
Roadmap Session and Use Cases for
Cloud Security, SASE, and Email Security
SASE Masters:
Deploying Harmony SASE for a 6,000-Strong Workforce
in a Single Weekend
Paradigm Shifts: Adventures Unleashed!
Capture Your Adventure for a Chance to WIN!
Mastering Compliance
Unveiling the power of Compliance Blade
CPX 2024 Content
is Here!
Harmony SaaS
The most advanced prevention
for SaaS-based threats
CheckMates Go:
CPX 2024 Recap
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Security Gateways
- :
- The source port of the SIP protocol passing throug...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The source port of the SIP protocol passing through the checkpoint is automatically changed.
Hi
Today, I received notification from a customer that the Source Port of the SIP protocol will be automatically changed.
It appears to be connecting to a new server, not the previously used service.
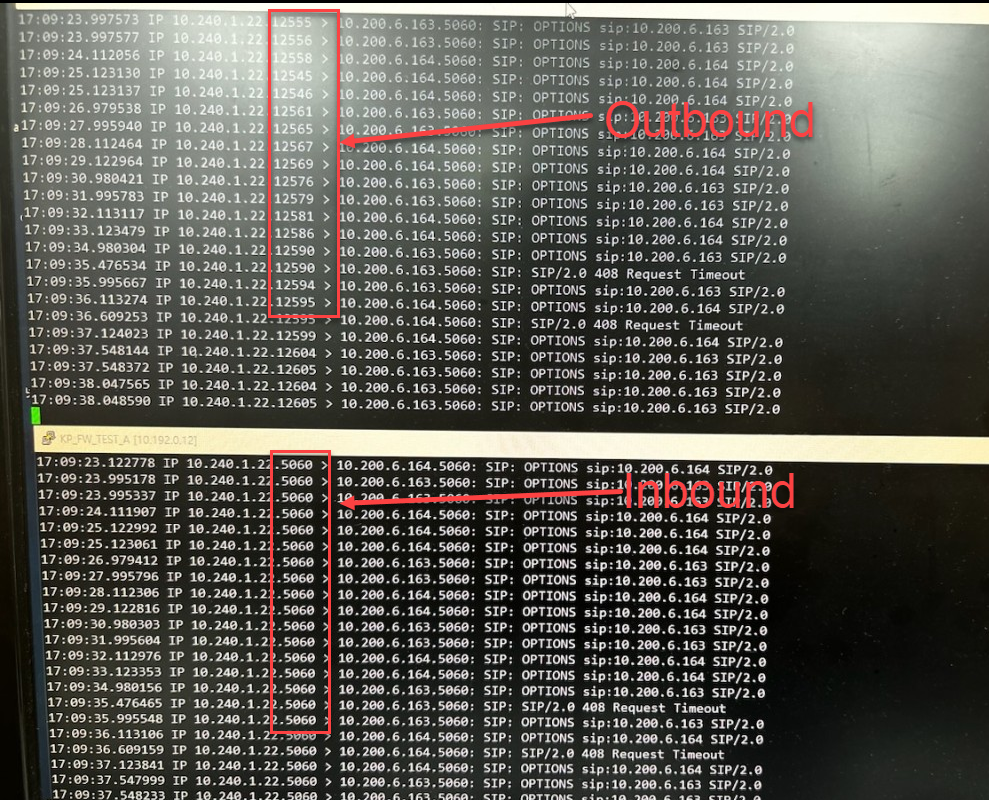
Looking at tcpdump, it looks like this:
Inbound - Source Port 5060 / Destination Port 5060
Outbound - Source Port high-num port / Destionation Port 5060
It is not determined whether this is the normal logic of the checkpoint.
And I have checked the below things to resolve the current situation:
1. NAT configuration
- The customer's firewall is not using NAT rules.
2. SIP Rule
- Uses SIP protocol provided by Check Point
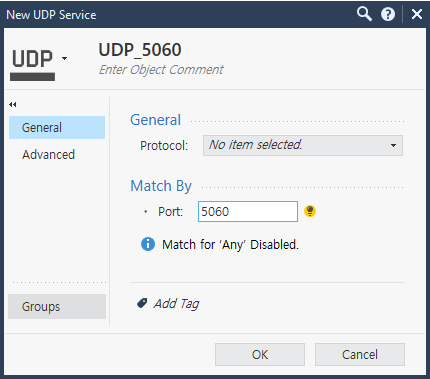
- Manually create TCP and UDP 5060 and apply them to policy --> the result is the same
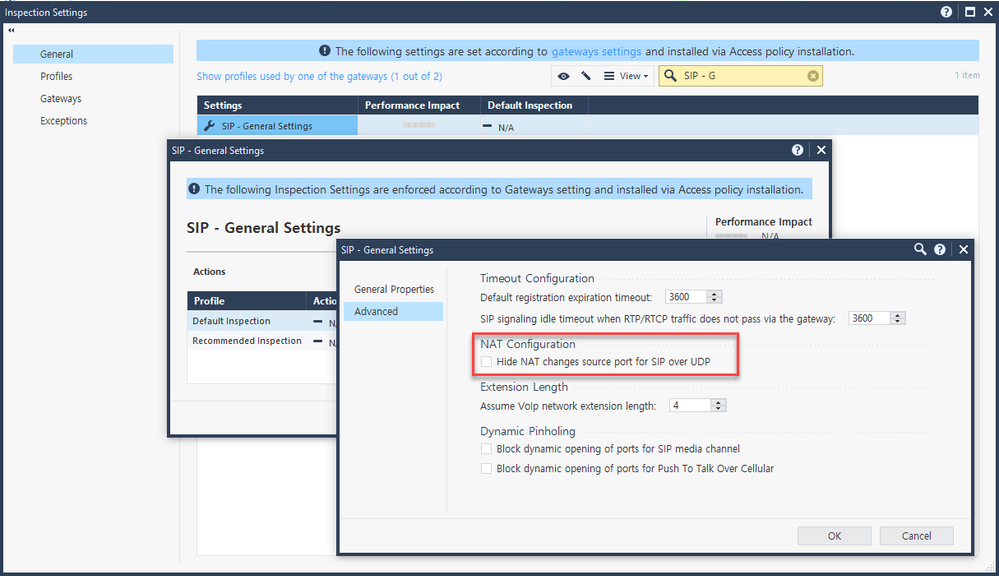
3. Inspection Setting
- SIP - General Settings - Advanced - NAT Configuraion (unchecked)
Can you give me some advice on my current situation?
Thank you in advance for those who responded
15 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What version/JHF?
Can you please provide a screenshot showing the services used in relevant rules?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Firewall version is R81.10 Take78
No screenshots of the policy, but the policy is simple
Source IP = Server A Network, Server B Network
Destination IP = Server A Network, Server Network
Service port = udp 5060 (manual)
Action = Accept
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have you performed the steps here for disabling Early SIP NAT?
https://support.checkpoint.com/results/sk/sk65072
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not sure source port really matters at all, the only thing you truly care is that dst port is right.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Unfortunately, it is very important for the src port to be tampered with.
When the server sends SIP Options or Invite, the server on the other side sends a response packet with 200ok
Packets flow as follows:
request--> Server A / S-Port 5060, D-Port 5060 --> CP Firewwall / S-Port High-num port, D-Port 5060 --> Server B
Response--> Server B / S-Port 5060, D-Port High-num port --> CP Firewall / S-Port 5060, D-Port High-num port --> Server A
Looking at the above flow, the session is not connected normally because the server receives a response through the high-num port.
I think it is normal logic for the checkpoint to map the high-num port back to 5060 through the late NAT function.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Maybe best to open TAC case to investigate further.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am currently inquiring by opening a case with TAC.
However, no clear solution has been proposed yet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
same issue.... any news from TAC?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My issue solved by changing back to use "SIP_Any" for R81.10.
Previously customer used "Custom SIP without SIP Handler" on R80.30.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thats been a "fix" since probably 2000 lol. I would not personally say thats the best solution, but it does work. Reason I say that is because there is no inspection being done on protocol with such setting.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Actually before using the Custom SIP ,Customer used the Pre-defined SIP_Any before and rule not match at that time then they need to use the "Custom" SIP instead. then we faced issue again after upgraded to R81.10 and "Custom SIP" did "Source NAT" without any technical explanation in any SK. Then after opened the case , TAC asked to try to change back to use "SIP_Any".
So We don't have any solid technical explanation to customer, Why "Custom SIP" did source NAT in R81.10??
Even Now, Customer's afraid to use SIP_Any (SIP Handler) every time they need to do version upgrade.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I get what you are saying, and in all honesty, I dont have logical explanation for it either. Maybe you could check with escalation/R&D on it and see what they say. I dont know if it could be version related, but its possible. Had not see issue like that myself in R81.20 as of yet.
Regards,
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm facing the same issue , Do we have the final solution?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I had a similar situation. IP phones were not working because the port was changed. Then the problem was solved by writing a NAT rule.
I don't have a connection to the customer, if I did I would send a screenshot, but this is how I wrote the rule.
Network Rule:
Source Adress: LAN-Network
Destination Address= B network
Service Port= udp 5060
NAT Rule:
Original Source Address: LAN-Network
Origial Destination Address= B network
Original Service Port= udp 5060
Translate Source Address: orginal
Translate Destination Address= orginal
Translate service Por= udp 5060
Can you try and check this way?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you!
We seem to be dealing with a seemingly similar issue as others have reported in this thread, and we are trying the NAT rule like you described as a workaround.
We are running R81.10 Take 110, and I am also interested to hear if there is anything from TAC/R&D about this issue.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 14 | |
| 13 | |
| 7 | |
| 7 | |
| 6 | |
| 5 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 02 May 2024 @ 10:00 AM (CEST)
CheckMates Live BeLux: How Can Check Point AI Copilot Assist You?Thu 02 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - Keine Kompromisse - Sicheres SD-WANThu 02 May 2024 @ 10:00 AM (CEST)
CheckMates Live BeLux: How Can Check Point AI Copilot Assist You?Thu 02 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - Keine Kompromisse - Sicheres SD-WANAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
Facts at a Glance
User Center