- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Strange behavior with fwaccel dos...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Strange behavior with fwaccel dos...
Greetings!
I'm noticing a strange behavior in our Security Gateways related to fwaccel dos after upgrading from R81.10.
Environment
- 1 Management (virtual machine) - R81.20 Take 53
- 2 Security Gateways - R81.20 Take 53
Assuming the enforcement on internal interfaces is disabled and the SecureXL Penalty Box is enabled.
fwaccel dos config get:
rate limit: enabled (without policy)
rule cache: enabled
pbox: enabled
deny list: enabled (with policy)
drop frags: disabled
drop opts: disabled
internal: disabled
monitor: disabled
log drops: enabled
log pbox: enabled
...
The strange behavior: after a while, the enforcement on internal interfaces becomes enabled WITHOUT DOING ANYTHING (internal: enabled). And then, I have to disable it again with fwaccel dos config set --disable-internal. It remains disabled for a while, but then, after a while it becomes enabled again.
Are you also experiencing the same "issue" ? Do you have any advice about the above ?
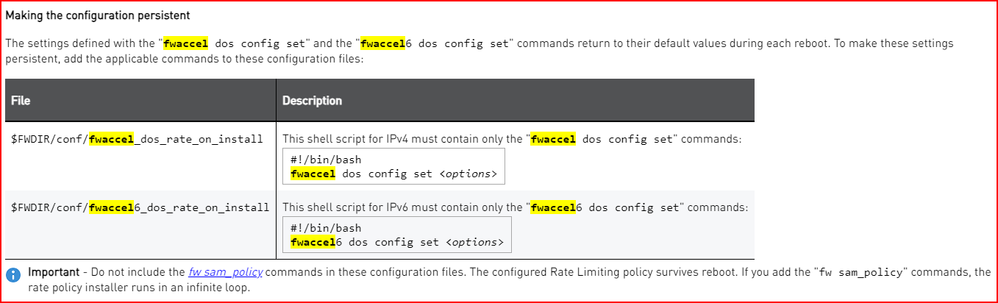
I also suppose the guide fwaccel dos config (R81.20 Performance Tuning Administration Guide) contains wrong information. On bottom of the article, it is reported:
$FWDIR/conf/fwaccel_dos_rate_on_install:
#!/bin/bash
#
# Automatically generated by fwaccel - DO NOT EDIT THIS FILE
rate.--set-enabled=1
global.--set-enforce-internal=0
pbox.--set-enabled=1
pbox.--set-log-reported=1
deny.--set-enabled=1
drop_frags.--set-enabled=0
drop_opts.--set-enabled=0
global.--set-monitor-only=0
rate.--set-rule-cache=1
global.--set-log-drops=1
...
deny.--set-name=
deny.--set-monitor-only=0
deny.--set-tcp-rst=0
pbox.--set-monitor-only=0
- The format of the file fwaccel_dos_rate_on_install (R81.20) is pretty different by the format mentioned in the article
- It seems it is not necessary to modify the file fwaccel_dos_rate_on_install in R81.20 for making settings persistent: the file is modified every time the fwaccel dos config set... is launched; and also inside the file there is written "# Automatically generated by fwaccel - DO NOT EDIT THIS FILE"
- I already sent feedback to Check Point about these wrong information -
That's it. I hope someone could help me with first two questions.
7 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I suspect what you discovered about the configuration file is related to the problem you're having.
Which means a consult with TAC if you haven't already opened a case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @PhoneBoy ,
thank you for your reply. Nope, I didn't opened a case yet (but I'll do that).
What do you mean: the config. file fwaccel_dos_rate_on_install I have in R81.20 shouldn't be in that format (so the article is correct ?) ...Or there is something wrong related to fwaccel dos and config. file in general, in R81.20 ?
Thank you,
Luca
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I assume it's related to whatever is auto-generating that configuration file.
Can you check the last modified date on that file and see if it tracks when you notice the issue occur?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @PhoneBoy,
Enforcement on internal interfaces disabled:
-rwxr-x--- 1 **** **** 498 Apr 18 23:34 /opt/CPsuite-R81.20/fw1/conf/fwaccel_dos_rate_on_install
Enforcement on internal interfaces enabled:
-rwxr-x--- 1 **** **** 498 Apr 19 00:08 /opt/CPsuite-R81.20/fw1/conf/fwaccel_dos_rate_on_install
# more $FWDIR/conf/fwaccel_dos_rate_on_install
#!/bin/bash
#
# Automatically generated by fwaccel - DO NOT EDIT THIS FILE
rate.--set-enabled=1
global.--set-enforce-internal=1
pbox.--set-enabled=1
pbox.--set-log-reported=1
deny.--set-enabled=1
drop_frags.--set-enabled=0
drop_opts.--set-enabled=0
global.--set-monitor-only=0
rate.--set-rule-cache=1
global.--set-log-drops=1
...
deny.--set-name=
deny.--set-monitor-only=0
deny.--set-tcp-rst=0
pbox.--set-monitor-only=0
# fwaccel dos config get
rate limit: enabled (without policy)
rule cache: enabled
pbox: enabled
deny list: enabled (with policy)
drop frags: disabled
drop opts: disabled
internal: enabled
monitor: disabled
log drops: enabled
log pbox: enabled
...
Set back to disabled:
# fwaccel dos config set --disable-internal
Configuration saved to /opt/CPsuite-R81.20/fw1/conf/fwaccel_dos_rate_on_install
When the config. file changes (automatically) the output shows the change (of course).
It would be interesting to know what "global.--" prefix in config. file, means.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sounds like a TAC case is in order
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Case opened.
Let's see...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
did you check out this one https://support.checkpoint.com/results/sk/sk179706 ?
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 17 | |
| 13 | |
| 8 | |
| 7 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 2 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter