- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- R80.30 URL filtering blocking allowed categories
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R80.30 URL filtering blocking allowed categories
Hi
I recently rolled out a pair of small appliances to two sites.
The web filtering policy for a particular user group is layered, and it has an allow list and the next rule is a drop all, with block message. HTTPS scanning is enabled with the cert rolled out. (I have also tried breaking the layers and having the standalone accept rule and then the standalone drop all rule after it)
On one site this works perfectly.
On another site, regularly (Every day or at least every other day) from early in the morning the firewall starts blocking all requests to anything categorised 'Computers/Internet' (Which is an allowed category) and a lot of things stop working. There are no failed category updates in the system log (Before the upgrade this same behaviour occurred, but we had updates failed and then database failed to reload so i suspected this initially). It's like the allow rule is being completely ignored. User auth is working, as the user name is logged in the log entry with the message the site was blocked as it belongs to the computers/internet category.
The only way to stop this is to remove the drop rule after the allow for this user group, Once you re-enable it and install the policy it will be fine again until the next time it happens out of the blue.
I previously upgraded the appliance from R80.20, as they were getting an HTTPS inspection error around certificate length (>1000) that the fix seemed to be upgrade to R80.30.
Any ideas?
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is no downloaded database for URL categorization, all lookups are done via the cloud.
What is the exact rule that is supposed to allow the traffic?
When the traffic is blocked, what rule is it hitting?
What are examples of the site(s) in question?
Also, maybe the issue isn't the URL categorization, but the gateway is failing to do LDAP lookups on users for some reason?
What is the exact rule that is supposed to allow the traffic?
When the traffic is blocked, what rule is it hitting?
What are examples of the site(s) in question?
Also, maybe the issue isn't the URL categorization, but the gateway is failing to do LDAP lookups on users for some reason?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ah, I assumed there was a DB due to the system events about installing application/url filtering database versions (And the old errors about failing to update and failing to reload DB)
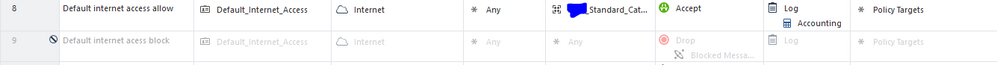
The exact rule is basic. Its from a user group, to internet and allow certain categories.
The rule immediately below is block everything else. Block rule is currently disabled.
LDAP I assume to be ok - as a username is listed with every log.
Examples of sites being blocked are
entrust.net (blocked as business/economy) - an allowed category
google.com - blocked as search engines (allowed category)
etc etc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
what is the setting for "fail mode" - blades -> appl/URLF > general > fail mode ?
When traffic is blocked, in the logs if you check "matched rule" tab, what is the number of rule?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The matched rule is the block rule, immediately below the allow rule.
I have already set fail-mode to open at the start of the problems, hoping that would fix it (It didnt)
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So there are two options, you don't hit allow rule because of source not matched access role or not matching category.
From one ticket with TAC, I was advised to put categories directly to the policy instead of creating custom application group and using it. I wasn't convinced at that time and for me it was just stupid, however it is working fine now. If your custom application group is not super lengthy, maybe you can try that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The user is communicated via AD Query, Identity Collector, etc.
LDAP is done from the gateway specifically to look up groups for the given user.
If LDAP is failing for some reason, then you would not be matching the Access Role in your allow rule.
It would explain why you're seeing the behavior you're seeing.
LDAP is done from the gateway specifically to look up groups for the given user.
If LDAP is failing for some reason, then you would not be matching the Access Role in your allow rule.
It would explain why you're seeing the behavior you're seeing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In fact on a second look, I think LDAP is working fine, because exactly the same access role is used in rule 9, so there is something wrong with matching app/urlf category.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The original poster is experiencing issues on one gateway, but not other.
The categorization should be the same and we can confirm this by looking at the log card of the dropped connection.
That pretty much leaves LDAP (or something with the lookup process) as the only culprit.
The categorization should be the same and we can confirm this by looking at the log card of the dropped connection.
That pretty much leaves LDAP (or something with the lookup process) as the only culprit.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
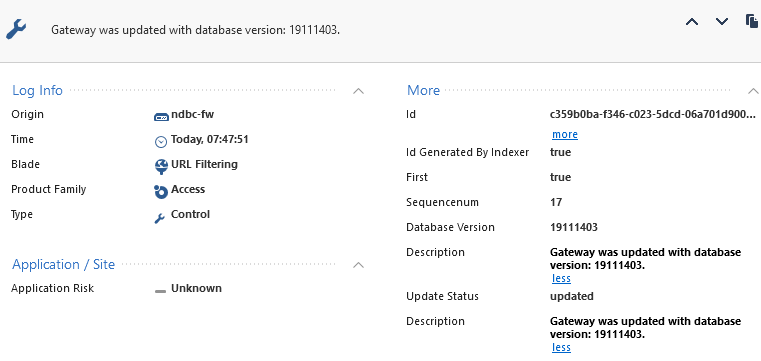
Where do you see log card of dropped connection? I fail to find this screenshot...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It wasn't provided, but I surmise, based on the original poster's description, that's what we'd find.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
oh, I see... But OP mentioned that rule 9 was matching, which has exactly the same access role as rule 8...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'll upload a few examples later - thanks so far guys for the time/consideration
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 13 | |
| 11 | |
| 10 | |
| 8 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 3 | |
| 3 |
Upcoming Events
Thu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter