- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure Users and Access)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
May the 4th (+4)
Roadmap Session and Use Cases for
Cloud Security, SASE, and Email Security
SASE Masters:
Deploying Harmony SASE for a 6,000-Strong Workforce
in a Single Weekend
Paradigm Shifts: Adventures Unleashed!
Capture Your Adventure for a Chance to WIN!
Mastering Compliance
Unveiling the power of Compliance Blade
CPX 2024 Content
is Here!
Harmony SaaS
The most advanced prevention
for SaaS-based threats
CheckMates Go:
CPX 2024 Recap
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Security Gateways
- :
- Policy Routing on Traffic Hitting Firewall Interfa...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Policy Routing on Traffic Hitting Firewall Interfaces
Hi All,
We were trying to influence routing via PBR to not use an Express Route interface. We essentially have Microsoft Cloud PCs that we want to get connected to remote access VPN.
fw monitor shows traffic coming in the Public WAN interfaces and return traffic being sent via Express Route. We wanted to change this behaviour without messing with link selection or route redistribution as the Cloud PC external IP falls under BGP learned ranges.
When trying with PBR to set the table action to use the Public WAN GW as next hop, and matching source to the FW interface range with destination of the cloud PC the traffic still went out the Express Route interface. TAC suggested to change the matching logic to match the interface and use the Microsoft IP as the source instead which also didn't solve the asymmetry.
Do PBRs not apply for traffic related to initiating remote access VPN connections?
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just finished up a call with TAC, and he said it was limitation 10. We were testing with just checking the connectivity to the IP over port 443 via powershell script instead of using the endpoint connect software.
So that solves that - limitation with PBR which we'll have to keep in mind for the future.
Thanks all
Rahul
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
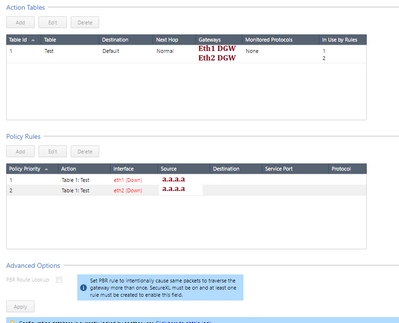
Just to update on this quick, @rsingh-a2n and I had a look together at customer's config and he showed me what was initially configured and what TAC suggested, but neither method worked. I asked him to upload some screenshots to this post.
I could be mistaken when I say this, but Im fairly positive that PBR takes precedence over regular static route, but still does not work.
Anyway, lets see if someone can clear any confusion.
Cheers,
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Andy.
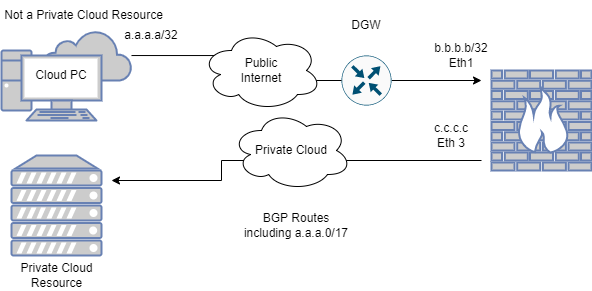
To get a sense of the environment, here is the Cloud PC going out over public WAN and the pre-existing express route going over the private cloud/private WAN.
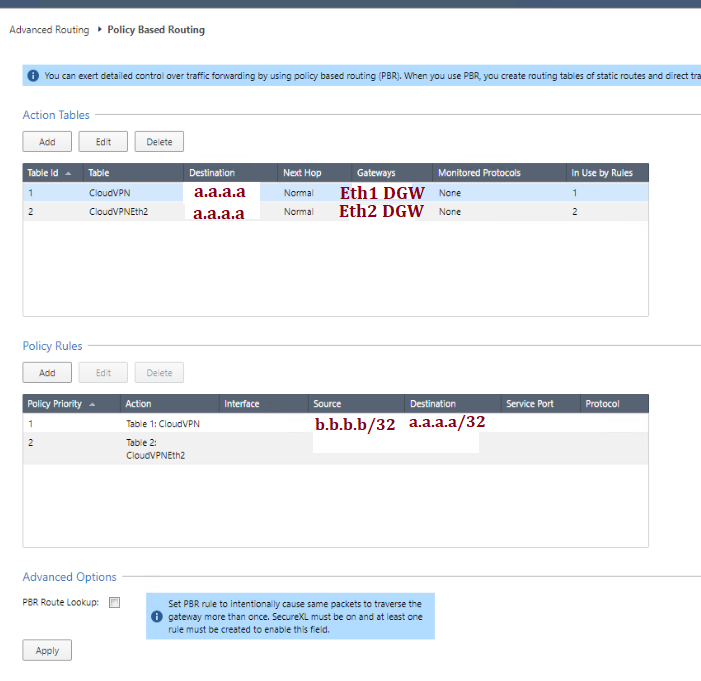
In the Checkpoint WebUI I tried a couple thing. The first attempt with PBR was using a matching rule of traffic coming from src Eth1 and with destination a.a.a.a, use table action 1. I also tried to put in the Eth1 subnet itself in the source column but fw monitor and tcpdump showed that even if traffic came in on Eth1, it would go out Eth3.
TAC recommended to change the action table to be a Default Destination using the same GW and set the matching logic to
Interface = Eth1 and Source = a.a.a.a (Cloud PC).
This also didn't work (confirmed via fw monitor). I've tried enabling the advanced PBR option and pushing policy but no luck so I thought I'd make the community post.
Best,
Rahul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To use PBR, you will need to be on R80.40 above and use Route-based VPNs.
See: https://support.checkpoint.com/results/sk/sk167135
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Customer actually ONLY has route based VPNs and they are on R81.10 + jumbo 78
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm guessing this will need a TAC case to investigate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's not clear from the diagram which is the VPN.
Why PBR vs just normal more specific static routes to correct this?
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I believe we did try regular static route, but Rahul can confirm for sure. Either way, there is an ongoing TAC case.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Chris,
The traffic from the Cloud PC to the Gateway over Public WAN is where the Remote VPN connection is attempting to establish. The return traffic is sent over the private cloud instead of back the way it came.
Static routes would work yes, but we don't want to run into an event where we are negatively impacting traffic that goes over the private wan link, that's why I wanted to use policy routes in the first place.
Rahul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the link PhoneBoy,
I guess limitation 10 applies here, since the Remote Access VPN reply traffic is treated as locally generated, it won't bother with PBR.
Rahul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I actually assume Remote Access would fall under Limitation 9, since Remote Access is basically domain-based VPN.
To confirm this 100%, I recommend a TAC case: https://help.checkpoint.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just finished up a call with TAC, and he said it was limitation 10. We were testing with just checking the connectivity to the IP over port 443 via powershell script instead of using the endpoint connect software.
So that solves that - limitation with PBR which we'll have to keep in mind for the future.
Thanks all
Rahul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 13 | |
| 13 | |
| 7 | |
| 7 | |
| 6 | |
| 5 | |
| 3 | |
| 3 | |
| 3 | |
| 2 |
Upcoming Events
Thu 02 May 2024 @ 10:00 AM (CEST)
CheckMates Live BeLux: How Can Check Point AI Copilot Assist You?Thu 02 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - Keine Kompromisse - Sicheres SD-WANThu 02 May 2024 @ 10:00 AM (CEST)
CheckMates Live BeLux: How Can Check Point AI Copilot Assist You?Thu 02 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - Keine Kompromisse - Sicheres SD-WANAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
Facts at a Glance
User Center