- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Detecting Threats Across the Open, Deep
and Dark Web With Infinity ERM
Four Ways to SASE
It's Here!
CPX 2025 Content
Remote Access VPN – User Experience
Help us with the Short-Term Roadmap
CheckMates Go:
What is UPPAK?
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Security Gateways
- :
- Re: Microsoft forces LDAPS march 2020, is Check Po...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Microsoft forces LDAPS march 2020, is Check Point aware of this
Hello,
starting march 2020 Microsoft forces the use of LDAPS only for connect to ActiveDirectory
2020 LDAP channel binding and LDAP signing requirement for Windows
I think there are some changes needed in the product. You can configure the LDAP-connection to AD with LDAPS, this works and is recommended. But there are still some feature they are using LDAP:
- first time wizard if enabling MOB or IA (gateway tries to connect to domain controller via LDAP not LDAPS)
- browsing ActiveDirectory (looks like problem from sk120669 is still active in R80.30)
Any statement from Check Point about this?
Wolfgang
19 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
please refer to sk164834 the solution is written in this SK.
if any further questions are needed you can contact me directly.
Thanks,
Ilya
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The referred SK only shows how to work around the IA FTW, not the browsing problem.
Other question on the same subject, is the rpoblem of using different IP's resolved while using a domain with IA?
I know in R80.10 that the browsing through the AD was using the IP of the Domain but while adding an access-role the MDS main IP was used instead. I would have to check if this is now resolved.
Other question on the same subject, is the rpoblem of using different IP's resolved while using a domain with IA?
I know in R80.10 that the browsing through the AD was using the IP of the Domain but while adding an access-role the MDS main IP was used instead. I would have to check if this is now resolved.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Maarten_Sjouw ,
I will appreciate if you could elaborate about your questions.
@Maarten_Sjouw wrote:
The referred SK only shows how to work around the IA FTW, not the browsing problem.
Which browsing problem?
@Maarten_Sjouw wrote:
Other question on the same subject, is the rpoblem of using different IP's resolved while using a domain with IA?
Can you please elaborate?
Thanks,
Royi Priov
Identity Awareness R&D.
Thanks,
Royi Priov
R&D Group manager, Infinity Identity
Royi Priov
R&D Group manager, Infinity Identity
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
as @Wolfgang mentioned:
-browsing ActiveDirectory (looks like problem from sk120669 is still active in R80.30)
In R80.10 I had issues with the connection to the AD server, while trying to add a access-role the connection was initiated from the IP of the MDS, while when you click Fetch Branches in the LDAP Account unit, the IP of the CMA was used.
-browsing ActiveDirectory (looks like problem from sk120669 is still active in R80.30)
In R80.10 I had issues with the connection to the AD server, while trying to add a access-role the connection was initiated from the IP of the MDS, while when you click Fetch Branches in the LDAP Account unit, the IP of the CMA was used.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok, I double checked this and yes the MDS IP still shows up in the logs when you work on the LDAP account unit.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I checked too some things they don't use LDAPS.
1. creating a new LDAP-Account-Unit via the MobileAccess- or IdentityAwareness-wizard fails if you don't allow LDAP on port 389 from the gateway.
2. Browsing through the LDAP-directory via Smartconsole fails if you don't allow LDAP on port 389 from the machine running the Smartconsole. There is an unencrypted LDAP-connectivity needed on port 389 between Smartconsole machine and the LDAP-server.
Problem is still in R80.30 Jumbo_111
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ilya,
after some research I found one thing which is using LDAP via TCP/389, which should be solved.
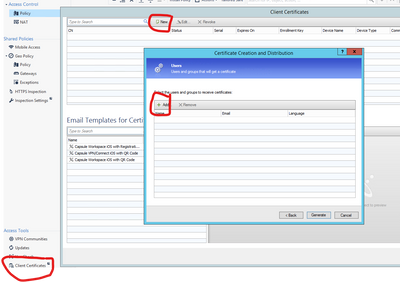
If you add user certificates like shown in the screenshot, the host running Smartconsole initiate a LDAP connection via TCP/389 to the LDAP-server. Regardless the LDAP-AccountUnit is configured to use LDAPS.
The browsing problem does no more exist. Adding users or machines to an access roles is done via a LDAPS connection from SMS to LDAP-server. Only browsing through the LDAP-AccountUnit via old SmartConsole is done via the host running SmartConsole and LDAP on TCP/389. But there is no more need for this for me.
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Another big pain point in using LDAPS for Account Units is the fingerprint fetch.
If you forget it, everything related to it is broken (IA, RA-VPN).
It would be nice to import CA chain to trust LDAPS instead of manual fingerprint fetching!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Norbert_Bohusch ,
I totally agree.
We already have plans on our road map to add this functionality.
Please ask your local office to open an RFE ticket for this, so we will be able to track this request.
Thanks,
Royi Priov
Identity Awareness R&D.
Thanks,
Royi Priov
R&D Group manager, Infinity Identity
Royi Priov
R&D Group manager, Infinity Identity
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You don't have to fetch fingerprints for it to work. LDAPS will work without fetching the fingerprint, it simply won't validate the fingerprint. If you fetch fingerprints, and all the servers have incorrect fingerprints, then it will fail.
I'm not sure if that will change with the Microsoft 2020 requirement listed in this thread...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I'm having the issue describe in sk156853 - getting error: "An error was detected while trying to authenticate against the AD server. It may be a problem of bad configuration or connectivity."
The solution in sk156853 is to malually fetch the fingerprint. After reading your comment I'm concern about this solution. Any recommandation? We are Running R80.40
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
you have to fetch manually or remove the fingerprint.
If you remove the fingerprint and don‘t adding again this is working fine but you have no validation with the LDAP servers certificate.
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just to add a clearification. It's not LDAPS(LDAP over SSL) Microsoft is enforcing, it's signed LDAP. But the work-around is to use LDAPS with Check Point.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If using LDAPS, does the fingerprint verification have anything to do with this? If I am using LDAPS already, but ignoring the fingerprint verification, will this still work after Microsoft's March patches are deployed?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Microsoft has backed off on forcing signing.
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/ADV190023
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi. Same here... the "Fetch" function seems to be a "randomizer". It did not work for me either. (R80.30)
I was looking for that cert that the "fetch" function was finding (thumbprint), but could not find such cert on the pointed Domain Controller. (But can't rule out that there is something in the process I'm not doing correctly)
Thanks for pointing it out.
I had better success by just getting the correct certificates "thumbprint/fingerprint" from the Domain Controller and copy/paste it to the field.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you ever figure this out? We also had some issues with the fetch... and the thumbprint that checkpoint fetched doesn't match up as to the cert on the DC...The thumbprint changed.. and broke IA/endpoint vpn connectivity.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi... just a quick note.
I was using non-supported PKI certificates. I re-did the whole PKI and now were only issuing certs for the computers that uses "Signature algorithm" SHAxxxRSA" (the xxx meaning how big large the signature should be).
Now we have on:
RootCA SHA512RSA
Intermediate Issuing SHA384RSA
End-device SHA256RSA
Once the signature algorithm was changed and I installed the new certificates to DC (domain controllers) the "fetch" automatically got the correct cert for the function. I think Check Point uses some Java 7 code in the background for that function, and this version of Java only supports a handful of "signature algorithms". But anyway, this was the silver bullet in our case.
Hope this helps.
Sneaky
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I came across the same thing while troubleshooting AD authentication errors today, where the fingerprints I was fetching didn't match any certificates on the domain controllers. It turns out that the fingerprint being fetched by SmartConsole is in MD5 format.
The best way I found to figure out which cert is being presented for LDAPS and what the 'Fetch' button should be getting is:
- To fetch the cert being presented for LDAPS, use openssl s_client -connect <hostname>:636
- Copy the -----BEGIN CERTIFICATE-----...-----END CERTIFICATE----- block into a text editor and save as .der (you can then open the cert to view it if you'd like)
- To calculate the MD5 fingerprint of the cert, use openssl x509 -noout -fingerprint -md5 -inform pem -in c:\temp\cert.der
The MD5 fingerprint calculated here should match the fetched value within SmartConsole.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 30 | |
| 16 | |
| 10 | |
| 7 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 3 |
Upcoming Events
Tue 13 May 2025 @ 04:00 PM (CEST)
German Session: NIS2- Compliance: Effiziente Vorbereitung und UmsetungTue 13 May 2025 @ 04:00 PM (CEST)
Maestro Masters EMEA: Quantum Maestro Architectures and OptimizationTue 13 May 2025 @ 02:00 PM (EDT)
Maestro Masters Americas: Quantum Maestro Architectures and OptimizationWed 14 May 2025 @ 10:00 AM (CEST)
ATAM 360°: Elevate Your Cyber Security Strategy with Proactive services - EMEAWed 14 May 2025 @ 03:00 PM (CEST)
NIS2 Readiness: Assess, Secure, and Comply with ConfidenceWed 14 May 2025 @ 10:30 AM (BRT)
Transforme sua Segurança de Rede com Agilidade e EficiênciaTue 13 May 2025 @ 04:00 PM (CEST)
Maestro Masters EMEA: Quantum Maestro Architectures and OptimizationTue 13 May 2025 @ 02:00 PM (EDT)
Maestro Masters Americas: Quantum Maestro Architectures and OptimizationWed 14 May 2025 @ 10:00 AM (CEST)
ATAM 360°: Elevate Your Cyber Security Strategy with Proactive services - EMEAWed 14 May 2025 @ 03:00 PM (CEST)
NIS2 Readiness: Assess, Secure, and Comply with ConfidenceWed 14 May 2025 @ 10:30 AM (BRT)
Transforme sua Segurança de Rede com Agilidade e EficiênciaWed 14 May 2025 @ 05:00 PM (CEST)
ATAM 360°: Elevate Your Cybersecurity Strategy with Proactive services - AMERICASThu 15 May 2025 @ 09:00 AM (IDT)
PA In-Person CloudGuard Workshop (CGNS, WAF, & API Security)About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter