- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Firewall Uptime, Reimagined
How AIOps Simplifies Operations and Prevents Outages
Introduction to Lakera:
Securing the AI Frontier!
Check Point Named Leader
2025 Gartner® Magic Quadrant™ for Hybrid Mesh Firewall
HTTPS Inspection
Help us to understand your needs better
CheckMates Go:
SharePoint CVEs and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- HTTPS Inspection Action:Error
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
HTTPS Inspection Action:Error
Hello, I would like to know if anyone here has been presented with this error?
Reviewing logs I have this error towards a specific destination, but what seems strange to me that this error appears depends on the Source because with some other sources the error does not appear towards the destination that presents the problem.
As additional information, both the source and destination segments have bypass rules in HTTPS INSPECTION.
Thanks a lot for the help.
............................................................................................................................................................................
Id Generated By Indexer: false
First: true
Sequencenum: 205
HTTPS Validation: The probe detected that this destination cannot be inspected and its identity cannot be verified due to a TLS alert (TLS alert: bad_certificate)
Description: Bypassing request as configured in engine settings of HTTPS Inspection
Source: x.x.x.x
Source Port: 60374
Destination: x.x.x.x
Destination Port: 443
IP Protocol: TCP (6)
Action: Bypass
Type: Log
Policy Name: YYYY
Policy Management: YYYY
Policy Date: 23 may
Blade: HTTPS Inspection
Origin: XXXX
Service: https (TCP/443)
Product Family: Network
HTTPS Inspection Action: Error
Labels
- Labels:
-
HTTPS Inspection
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks a lot for your support.
The problem that we had specifically was with some servers with Workload Security agents that were not synchronizing with the cloud. One of our team had created a rule in the FW but at the destination it had only one IP that was the one that gave us the HTTPS Inspection error.
Reading the Trend Micro documentation, you have to add some domains (130) the Security, APCL and HTTPS INSPECTION rules were created with said group of Trend Micro domains and Problem solved.
https://cloudone.trendmicro.com/docs/workload-security/communication-ports-urls-ip/#Deep3
By the way, although the problem is solved I have to update the certificate database so I will follow your recommendation @the_rock
Regards!!
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The error states that the GW cannot validate the server certificate. If it only happens to some of the connections to the same server and not all, look if you have any intermittent connectivity failures on that GW. Also, it might be that the destination IP hosts multiple web servers, some of them with bad certificates.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for answering _Val_.
Do you think that updating the certificate database can help?
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
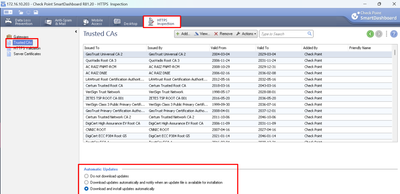
100% that can only help, not make it worse. So, make sure below is enabled as per my screenshots and if you need zip file, happy to send it over. Just a small disclaimer, though couple of people on here used it and was fine, dont "shoot" the messenger if something goes sideways lol
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks a lot for the help Andy.
I really appreciate it.
Regards
Carlos Isaac!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Any time, happy to help. Let us know if any issues, I have working R81.20 lab with windows 10 and https inspection on, so can test anything needed.
Cheers,
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It might, but we need to figure out first, what we are dealing with. If it is an intermittent issue for the same server, connectivity is the prime suspect.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@_Val_ makes a good point Isaac. It really depends if its intermittent issue or not. I mean, you can certainly update certificate list, its not going to make it worse, but there is no guarantee it would make it better either.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks a lot for your support.
The problem that we had specifically was with some servers with Workload Security agents that were not synchronizing with the cloud. One of our team had created a rule in the FW but at the destination it had only one IP that was the one that gave us the HTTPS Inspection error.
Reading the Trend Micro documentation, you have to add some domains (130) the Security, APCL and HTTPS INSPECTION rules were created with said group of Trend Micro domains and Problem solved.
https://cloudone.trendmicro.com/docs/workload-security/communication-ports-urls-ip/#Deep3
By the way, although the problem is solved I have to update the certificate database so I will follow your recommendation @the_rock
Regards!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sounds good...keep us posted.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey mate,
I wanted to tell you something else, just my own experience, as well as one customer I worked with for https inspection. So, when I tested this in the lab (R80.40, R81.10 and R81.20), I would simply install https inspection cert generated (follow on screen prompt) and it would work without any issues. Customer first tested it on one machine and had problem, so he reinstalled the cert and placed it in trusted root and worked fine. Then they tried few machines and some worked okay, some did not, following exact same process.
They had Trend Micro before going with CP, told me they never had this sort of problem, but turns out after they upgraded their environment to R81.10, all just worked fine. So, I would say if you have cert in trusted root, thats 100% correct.
Cheers,
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is an interesting fact, to comment that the environment we have is R80.40 and we plan to update it to R81.10.
So I hope that by updating the Certificates and upgrading to R81.10 there will be no more problems in the future.
Regards
Isaac.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Im sure it would be better.
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 24 | |
| 13 | |
| 9 | |
| 8 | |
| 8 | |
| 6 | |
| 5 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Wed 22 Oct 2025 @ 11:00 AM (EDT)
Firewall Uptime, Reimagined: How AIOps Simplifies Operations and Prevents OutagesTue 28 Oct 2025 @ 11:00 AM (EDT)
Under the Hood: CloudGuard Network Security for Google Cloud Network Security Integration - OverviewAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter