- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Announcing Quantum R82.10!
Learn MoreOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- CLI Anti-Spoofing Information
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
CLI Anti-Spoofing Information
Does anyone know of a way to see your anti-spoofing configuration per interface on the CLI?
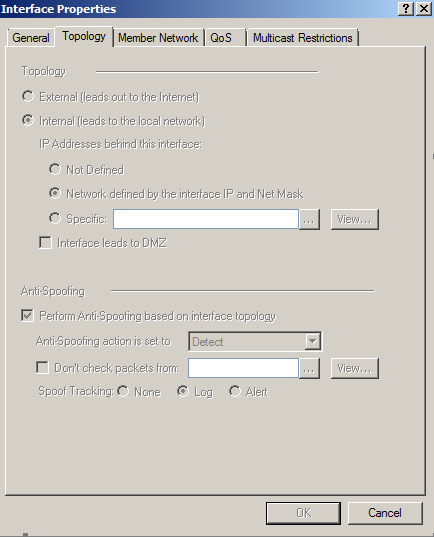
Basically --
- Anti-Spoofing is Enabled (y/n)
- Anti-Spoofing Action (Detect/Prevent)
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Look at this article:
Show Address Spoofing Networks via CLI
Regards
Heiko
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
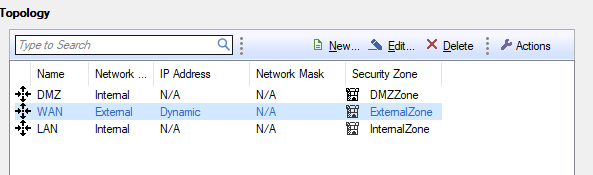
Hello for each interface in the topology you can set the anti-spoofing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes - I know it can be done in the GUI.
I want to know if anyone has found a way to check it on the local gateway. The GUI is currently very time consuming to audit, but scripting to gateways is very simple.
I'm guessing since its part of the policy, it won't be super easy to find on the local gateway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Bryce I think this info should be useful
fw ctl set int fw_antispoofing_enabled 0
sim feature anti_spoofing off ; fwaccel off ; fwaccel on
fw ctl set int fw_antispoofing_enabled 1
sim feature anti_spoofing on ; fwaccel off ; fwaccel on
This was posted on the https://community.checkpoint.com/thread/5319-my-top-3-check-point-cli-commands
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Isn't that just a global anti-spoofing setting? I can't tell what the configuration per interface is.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Pablo,
How can we disable anti spoofing from command line in R80.20?
In R80.20 GA the following command has been removed:
sim feature anti_spoofing off
[Expert@pa:0]# sim feature anti_spoofing off
Command 'sim feature' has been replaced. Use 'fwaccel feature' instead.
[Expert@pa:0]# fwaccel feature anti_spoofing off
Invalid feature 'anti_spoofing'
Usage: fwaccel feature <name> {on|off|get}
Available features: sctp
Any suggestions?
Many thanks.
Kind regards,
Kris
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Firewall CLI or R80+ SMS CLI?
--
My Book "Max Power: Check Point Firewall Performance Optimization"
Second Edition Coming Soon
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Firewall CLI at the moment.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't think there is a direct way to pull this info from the running firewall kernel (I originally thought it could be provided by the sim ranges command), but what you can do is first run fw ctl iflist on the firewall to get the list of interfaces, and then view (not edit!) the firewall's $FWDIR/state/local/FW1/local.set file. In that file you will find a section called "if_info" and under that "objtype (gw)" and then an indented list of firewall interfaces. Under each firewall interface you will see two values:
has_addr_info (true|false)
true: antispoofing enabled on that interface
false: antispoofing is disabled on that interface
monitor_only (true|false)
true: antispoofing action is Detect on that interface
false: antispoofing action is Prevent on that interface
I'm sure someone could script something to pull this info out of the file a bit easier...
--
My Book "Max Power: Check Point Firewall Performance Optimization"
Second Edition Coming Soon
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Tim - this is great information! I'm going to build a script to check for these settings on the gateway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Looking on my R80.10 gateway, for each interface, I also see interface_topology which tells you what subnets are "valid" on a given interface (assuming that's useful to your task).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yep that same $FWDIR/state/local/FW1/local.set on the firewall does show the calculated network topology for each interface as well as the anti-spoofing settings. Could definitely be handy if there are lots of nested groups specified in the anti-spoofing settings that makes figuring out the actual topology (and resulting anti-spoofing enforcement) difficult from the SmartDashboard/SmartConsole.
--
My Book "Max Power: Check Point Firewall Performance Optimization"
Second Edition Coming Soon
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Look at this article:
Show Address Spoofing Networks via CLI
Regards
Heiko
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think there is an opportunity to leverage GUIDBedit from the management CLI to look at the policy, but even if its changed in the policy - if it hasn't been deployed, the gateway doesn't actually have the anti-spoofing settings.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 27 | |
| 20 | |
| 16 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 3 | |
| 3 |
Upcoming Events
Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


