- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud Cloud Network Security CloudMates General CNAPP CloudGuard - WAF Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Open Garden In Action:
Find and Remediate Threats Everywhere!
New Appliance Announcements
and Faster Threat Prevention
Remote Access VPN – User Experience
Help us with the Short-Term Roadmap
It's Here!
CPX 2025 Content
CheckMates Go:
AI Agents
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Security Gateways
- :
- BLOCK BAD REPUTATION IPS IN A DYNAMIC WAY
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
BLOCK BAD REPUTATION IPS IN A DYNAMIC WAY
Hello experts,
Kindly guide me if its possible to have like a rule, blade or external connector or any recommended configuration in order to have protection on the Gateway perimeter to block malicious reported IP address range like botnets, hackers etc? This is with the purpose to reduce having to create objects and manually applied to specific existing block rule on the network access layer.
Thanks!
2 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ioc_feeds, available natively in R81 SmartConsole - refer sk132193.
Other options exist depending on your enabled blades and might leverage dynamic / imported objects (sk167210) or the available APIs.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey bro,
What I always do is use below link, get all IPs from the txt file, slap it in .csv file, import in mgmt, create a rule with group object containing the file you import and thats it.
Andy
You can also use below sites to confirm if site might be malicious.
32 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ioc_feeds, available natively in R81 SmartConsole - refer sk132193.
Other options exist depending on your enabled blades and might leverage dynamic / imported objects (sk167210) or the available APIs.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
known bad IP shouldn´t that be filtered within the IPS blade?
https://www.youtube.com/c/MagnusHolmberg-NetSec
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Anti-bot & Anti-virus have such reputation based protections but if you wish to leverage external or custom feeds you need to use something else.
- ioc_feed
- Network feed objects (R81.20)
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sure but correct me out am wrong.
anti bot us for outgoing.
having a checkpoint provided ip list of bad stuff for incoming would be great, such as know bot network. Ips would be perfect for this.
https://www.youtube.com/c/MagnusHolmberg-NetSec
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
"perfect" is relative, some also might prefer fwaccel dos (SecureXL) level mitigation of such similar lists.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sure, seen also from check point side as IPS is something you pay for.
I would be more than happy to have this as a regular dynamic object just as O365 to have “suspected IP ranges and DNS”
https://www.youtube.com/c/MagnusHolmberg-NetSec
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
so true 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The “incoming only” block for Anti-Bot was fixed in R81.
Even in R80.40 and earlier, while an outbound packet was allowed, the inbound replies were correctly blocked.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you mean that Anti-Bot would block incoming attempts from known “bad” ip addresses to a web server based on these lists it has?
my understanding was been that anti-not was a post infection blade killing the C&C traffic or similar originating from the inside network to destination to C&C “bad ip”
if it dose both then it’s great 🙂
Maybe something I just misunderstood.
https://www.youtube.com/c/MagnusHolmberg-NetSec
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I had it reversed prior to R81: Inbound wasn't blocked, but the outbound reply was.
Either way, in R81 and above, feeds imported via ioc_feeds will be blocked inbound or outbound.
This is documented here: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How about anti bot without using custom feeds?
https://www.youtube.com/c/MagnusHolmberg-NetSec
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
On ThreatCloud feeds, I don't believe we block inbound (but could be wrong about that).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To utilise custom feeds do need both AB and AV blades enabled not just one of them in R81.10 anyway
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey bro,
What I always do is use below link, get all IPs from the txt file, slap it in .csv file, import in mgmt, create a rule with group object containing the file you import and thats it.
Andy
You can also use below sites to confirm if site might be malicious.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi the_rock!
can you please let me know how to block multiple IP's on Locally managed R81.10.
Thanks & Regards,
Shanil
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey @shanil420 ,
Im not overly familiar with SMB appliances, so dont know if same method would work or not, but Im sure there is a way to import a list that can be blocked. Let me spin up a demo and will check for you,
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you so much for your quick reply. Much appreciate the support 👍
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Im still checking if there is good way to do this on locally managed SMB.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please look at IOC Feeds feature:
sk132193 What is the "Custom Intelligence Feeds" feature?
https://support.checkpoint.com/results/sk/sk132193
Also refer to:
https://community.checkpoint.com/t5/Threat-Prevention/CheckMates-Tips-and-Tricks-IOCs-TAXII-feeds-an...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I was more thinking of adding generic data center object that can be used with .json file to block the bad known IPs, but I dont believe thats possible on locally managed SMB?
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you so much Tal, appreciate your support.
Since im a newbie is there any way i can apply this using GUI.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
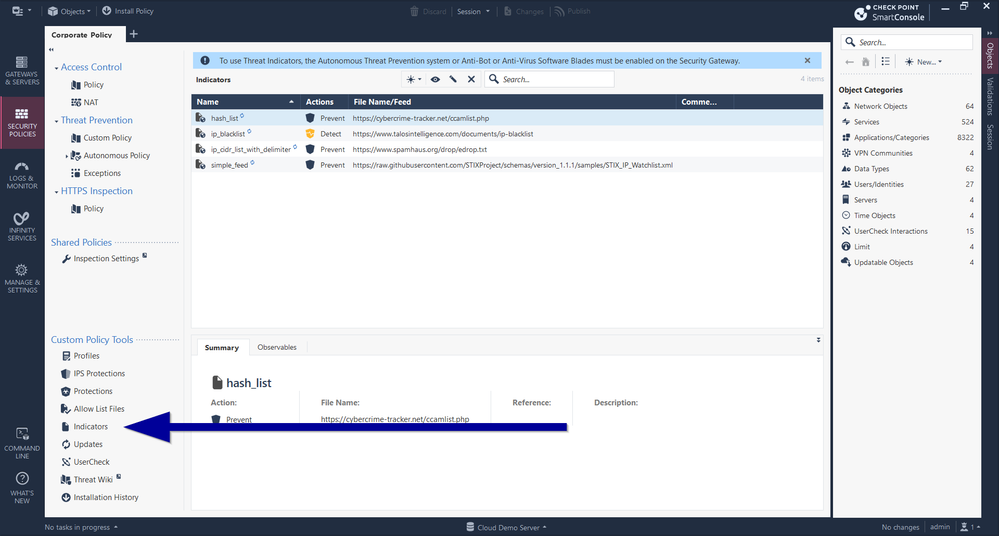
Sure! in SmartConsole go to - Security Policies > Threat Prevention > Select any Threat Prevention Policy > At the bottom go to - Custom Policy Tools > Indicators
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
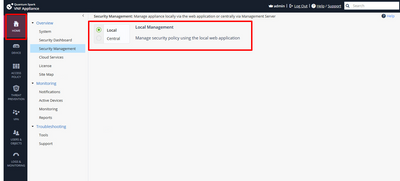
That would work if it was centrally managed, but its NOT...its locally managed.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
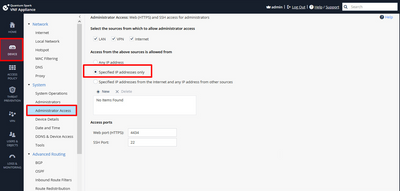
Yes this is locally managed. Is there a way to limit Web console & SSH access by geolocation.?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
awsome! guess this will help. Thank you so much!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Since this is locally managed how can i add Smartconsole. Will it interfere with the LAN network ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Will changing this affect my LAN network? As per your view what is the best method to manage checkpoint? can you share me an guide pls
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 9 | |
| 7 | |
| 7 | |
| 7 | |
| 4 | |
| 4 | |
| 4 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Wed 16 Jul 2025 @ 10:00 AM (CEST)
Master GCP Security with the Cloud Architects Series (Multilingual Webinar)Wed 16 Jul 2025 @ 04:00 PM (CEST)
Operationalizing Threat Intelligence, Part II: Threat Hunting & Incident ResponseTue 22 Jul 2025 @ 10:00 AM (CEST)
Cyber Security Training in the Era of AI Threats: Managed SmartAwareness Explained - EMEATue 22 Jul 2025 @ 05:00 PM (CEST)
Cyber Security Training in the Era of AI Threats: Managed SmartAwareness Explained - AMERThu 31 Jul 2025 @ 10:00 AM (CEST)
CloudGuard Network Security for Nutanix - Full Deployment with Tenant & Transit VPC - EMEA/APACWed 16 Jul 2025 @ 04:00 PM (CEST)
Operationalizing Threat Intelligence, Part II: Threat Hunting & Incident ResponseTue 22 Jul 2025 @ 10:00 AM (CEST)
Cyber Security Training in the Era of AI Threats: Managed SmartAwareness Explained - EMEATue 22 Jul 2025 @ 05:00 PM (CEST)
Cyber Security Training in the Era of AI Threats: Managed SmartAwareness Explained - AMERThu 31 Jul 2025 @ 10:00 AM (CEST)
CloudGuard Network Security for Nutanix - Full Deployment with Tenant & Transit VPC - EMEA/APACThu 31 Jul 2025 @ 05:00 PM (CEST)
CloudGuard Network Security for Nutanix - Full Deployment with Tenant & Transit VPC - AMER/EMEAAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter