- CheckMates
- :
- Products
- :
- Quantum
- :
- SMB Gateways (Spark)
- :
- Replace Internal CA - SSL Inspection with own cert...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Replace Internal CA - SSL Inspection with own certificate.
Hello Checkmates,
I'm testing the SSL Inspection on Checkpoint 790 with R77.20.75 firmware. With the dafault internal certificate it works as described in the instructions.
According to the sk121214, I can use my own certificate by replacing the internal CA.
I'm trying to use one issued by our Private PKI server. I can preview the certificate, but when I apply, the firewall appliance load it, but with error: Invalid certificate file.
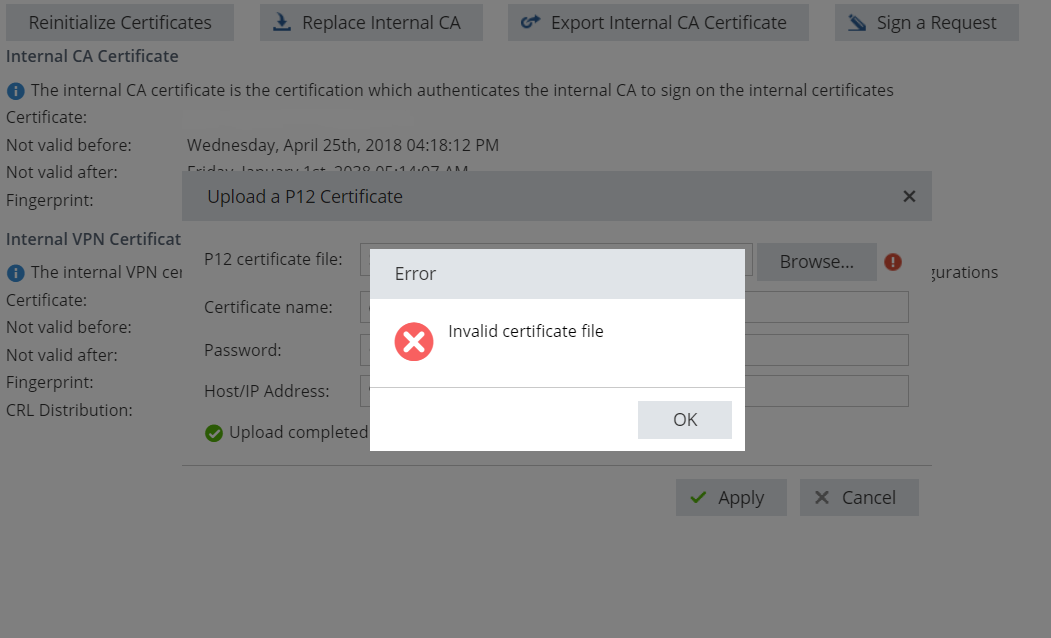
As a result also the VPN service is affected, and my only option to recover is to Reinitialize Certificates.
What are the specific requirements for the replacing certificate, in addition to that it should be .p12 or .pfx?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you confirm your private PKI server is issuing a certificate authority key?
If it's not a CA key, it will not be considered valid.
You may also need to provide the entire certificate chain to the root CA so the gateway can validated the certificate.
This is because HTTPS Inspection generates certificates on the fly based on the CA key (either the one you provide or the one internally generated).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No it wasn't. I've missed that explanation ![]() . Now I understand that the Checkpoint should act as a sub issuing CA in our enterprise PKI.
. Now I understand that the Checkpoint should act as a sub issuing CA in our enterprise PKI.
It would be easier, if the firewall can create a request file for a subordinate CA certificate, as it will contain the required attributes. I assume the subject field can be anything and should have the following key usages KEY_CERT_SIGN_KEY_USAGE CERT_DIGITAL_SIGNATURE_KEY_USAGE.
Is the checkpoint also going to create a new certificate for the VPN, based on the uploaded valid sub CA cert?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, a new certificate for the VPN is only created if you trigger that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That sounds right to me.


