- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Quantum Spark Management Unleashed!
Check Point Named Leader
2025 Gartner® Magic Quadrant™ for Hybrid Mesh Firewall
HTTPS Inspection
Help us to understand your needs better
CheckMates Go:
SharePoint CVEs and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- SMB Gateways (Spark)
- :
- Latest firmware builds for 77.20.xx SMB appliances
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Latest firmware builds for 77.20.xx SMB appliances
In sk165875: Check Point Response to CVE-2020-8597 (PPP buffer overflow vulnerability) we found the latest 77.20.xx firmware builds for SMB appliances - but now in response to DNSpooQ (CVE-2020-25686, CVE-2020-25684, CVE-2020-25685), CP TAC provided fixed versions also for older models (2021-02):
- R77.20.80 Build 990172507 for 600/1100 Appliances
- R77.20.81 Build 990172611 for 1200R Appliances
- R77.20.87 Build 990173120 for 700/900/1400
With sk176148: Check Point response to CVE-2021-26414 - "Windows DCOM Server Security Feature Bypass" customers using MS DC/AD received fixed firmware versions that are available from TAC only (01-Nov-2021):
- R77.20.87 build 990173127 for 700/1400 appliances
- R77.20.81 Build 990172625 for 1200R appliances
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
67 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R77.20.87 ist now B990173049
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not really:
- R77.20.87 Build B990173042 for 700/900/1400 and sk153433: Jumbo Hotfix Accumulator for R77.20.87 say that B990173042 is the latest R77.20.87 Jumbo Hotfix Accumulator GA version that can be directly downloaded from these articles.
- R77.20.87 B990173049 is a version where you need to Contact Check Point Support to get a Hotfix for this issues: sk167693: Various issues with emails and Outlook when using IMAPS or POP3S on SMB appliances and sk168797: Traffic routes out of the wrong interface after updating an SMB image with ISP redundancy ...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes really, 3049 is mentioned here https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
"This problem was fixed. The fix is included in:
If you do not wish to upgrade, please Contact Check Point Support to get a Hotfix for this issue. "
So the JHF article just lacks an upgrade as the SK clearly points to the JHF article.
BTW the OP did not mention anything about GA anyhow.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, it certainly is GA. But the link to the wrong source is nice, i would add some feedback there 8) I assume that people writting sk168797 thought that B990173049 would be GA soon, but as we see the phrase "If you do not wish to upgrade" it rather seems that something was mistaken, as a GAiA Embedded Hotfix always is a new firmware version including it.
So you can turn it anyway you want, R77.20.87 B990173049 is private and only available thru TAC - sk168797 is wrong as the R77.20.87 B990173049 is no GA version (yet)....
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Even if it is still not GA, you never mentioned GA in the OP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It seems that now there is r77.20.87 B3055 if you ask TAC. Very confusing and determining what are some of the fixes made above B3042? Debating do I upgrade?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sk167693 (from build 3044) and sk168797 (from build 3049) are two fixes included.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yet if you call into TAC to get the fix for sk167693. They seem to give a different build number each time, now it's up to B3057 which they release so am sure it contains more than just those two fixes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HFA is updated to 3068.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you - i updated my post !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I saw that too, but the resolved issues list is unchanged? Still lists B3042 as the latest (aside from the private builds).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It looks like there is an issue with the latest build. See the updated sk.
Maybe there will be a new build coming soon.
Jumbo Hotfix Accumulator for R77.20.87
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
IMPORTANT: We have detected a problem with the latest build (Build 990173068). As a result, we have temporarily removed the download links below. We are investigating the issue and will update the article as soon as it is resolved.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HFA is updated to build 3072
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
... but no information about fixes in Build 990173072 is available yet ! I have corrected the build in my post, link is the same as before, and i have left Feedback in the sk153433. I have installed this firmware yesterday...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Probably the ones in the upcomimg section.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No - response was: The new build consists of some general stability fixes. provided by TAC.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sk153433 now contains:
| R77.20.87 Jumbo Hotfix build 990173072 | |
| - | General stability improvements and fixes. |
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well, not entirely. 😀 For example we have a new process now:
/pfrm2.0/bin/jitterentropy_rngd
Using the Jitter RNG core, the rngd provides an entropy source that feeds into the Linux /dev/random device if its entropy runs low. It updates the /dev/random entropy estimator such that the newly provided entropy unblocks /dev/random.
The seeding of /dev/random also ensures that /dev/urandom benefits from entropy. Especially during boot time, when the entropy of Linux is low, the Jitter RNGd provides a source of sufficient entropy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
fwtmp directory default value is now 60MB (changed from 40MB since B3051) 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, that is quite a change:
# df -h
Filesystem Size Used Available Use% Mounted on
tmpfs 30.0M 224.0K 29.8M 1% /tmp
tmpfs 60.0M 11.2M 48.8M 19% /fwtmp
ubi2_0 65.6M 992.0K 61.3M 2% /logs
ubi3_0 259.8M 134.4M 120.7M 53% /storage
ubi1_0 159.4M 127.6M 31.9M 80% /pfrm2.0
tmpfs 14.0M 36.0K 14.0M 0% /tmp/log/local
tmpfs 100.0M 0 100.0M 0% /tetmp
See the new size of /fwtmp. Also /tmp size was changed manually:
Maximum possible size is 4 times 20 = 80MB. These 80MB seem to be reserved for /tmp as even when set to 80MB, other partitions do not shrink:
Filesystem Size Used Available Use% Mounted on
tmpfs 80.0M 224.0K 79.8M 0% /tmp
tmpfs 60.0M 11.2M 48.8M 19% /fwtmp
ubi2_0 65.6M 988.0K 61.3M 2% /logs
ubi3_0 259.8M 134.4M 120.7M 53% /storage
ubi1_0 159.4M 127.6M 31.9M 80% /pfrm2.0
tmpfs 14.0M 36.0K 14.0M 0% /tmp/log/local
tmpfs 100.0M 0 100.0M 0% /tetmp
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have the 1400, noticed the /fwtmp set to the new size of 60.0M but my /tmp is still sitting on 20.0M yet as I understand this was increased to 30.0M?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
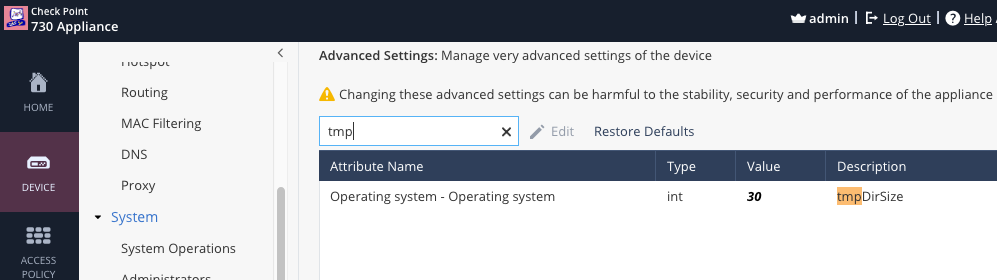
/tmp is still 20MB as long as you do not change the value in Advanced Settings !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok thanks, I thought there may have been some sort of a bug during upgrade that it did not take into affect on the configurations. Appreciate the response.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Any feedback on how's latest JHF (3072) working in production environment ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
so far so good and far better build than B3042. Clearly a lot of code optimization GUI is far more responsive, however, still doing some testing to see if it resolved the GUI core. When I would not login into the firewall and its been running for 20 plus days. logging into the GUI and navigating would cause a no response, core. I also have B3077 that may install to fix the other issues especially with SSL and HTTPS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
3077 is for which sk?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SMB-14108 Policy installation for the 1400 Security Gateway with IPS blade enabled fails with the following error message: "Installation failed. Reason: Failed to load Policy on Security Gateway". Refer to sk170930.
SMB-14072 When HTTPS Inspection is enabled and the application is blocked, the user may not receive a user-check block page for some websites.
SMB-13454 If you create a new Application Group that contains one application that does not require SSL inspection and another application that does, the custom application group icon shows a lock icon even after you delete application signatures that require SSL inspection.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
NP, let me know if you have upgraded and any issues identified.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 12 | |
| 5 | |
| 4 | |
| 4 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Tue 16 Sep 2025 @ 02:00 PM (EDT)
Securing Applications with Check Point and AWS: A Unified WAF-as-a-Service Approach - AmericasWed 17 Sep 2025 @ 04:00 PM (AEST)
Securing Applications with Check Point and AWS: A Unified WAF-as-a-Service Approach - APACWed 17 Sep 2025 @ 03:00 PM (CEST)
Securing Applications with Check Point and AWS: A Unified WAF-as-a-Service Approach - EMEAThu 18 Sep 2025 @ 03:00 PM (CEST)
Bridge the Unmanaged Device Gap with Enterprise Browser - EMEAThu 18 Sep 2025 @ 02:00 PM (EDT)
Bridge the Unmanaged Device Gap with Enterprise Browser - AmericasTue 16 Sep 2025 @ 02:00 PM (EDT)
Securing Applications with Check Point and AWS: A Unified WAF-as-a-Service Approach - AmericasWed 17 Sep 2025 @ 04:00 PM (AEST)
Securing Applications with Check Point and AWS: A Unified WAF-as-a-Service Approach - APACWed 17 Sep 2025 @ 03:00 PM (CEST)
Securing Applications with Check Point and AWS: A Unified WAF-as-a-Service Approach - EMEAThu 18 Sep 2025 @ 03:00 PM (CEST)
Bridge the Unmanaged Device Gap with Enterprise Browser - EMEAThu 18 Sep 2025 @ 02:00 PM (EDT)
Bridge the Unmanaged Device Gap with Enterprise Browser - AmericasAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter