- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Explore New Wave of Web Based
DDoS Attacks and Mitigations
Four Ways to SASE
It's Here!
CPX 2025 Content
Remote Access VPN – User Experience
Help us with the Short-Term Roadmap
CheckMates Go:
What is UPPAK?
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Remote Access VPN
- :
- Re: strongSwan - GUI - Network Manager - Username ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
strongSwan - GUI - Network Manager - Username / Password
Instead of using strongSwan Command Line Interface (CLI), you can also use the Network-Manager-strongSwan Plugin to create a VPN Remote Connection to a Check Point Firewall.
This is not an official guide. This is just a tutorial from my lab.
How to configure strongSwan, please see:
Environment:
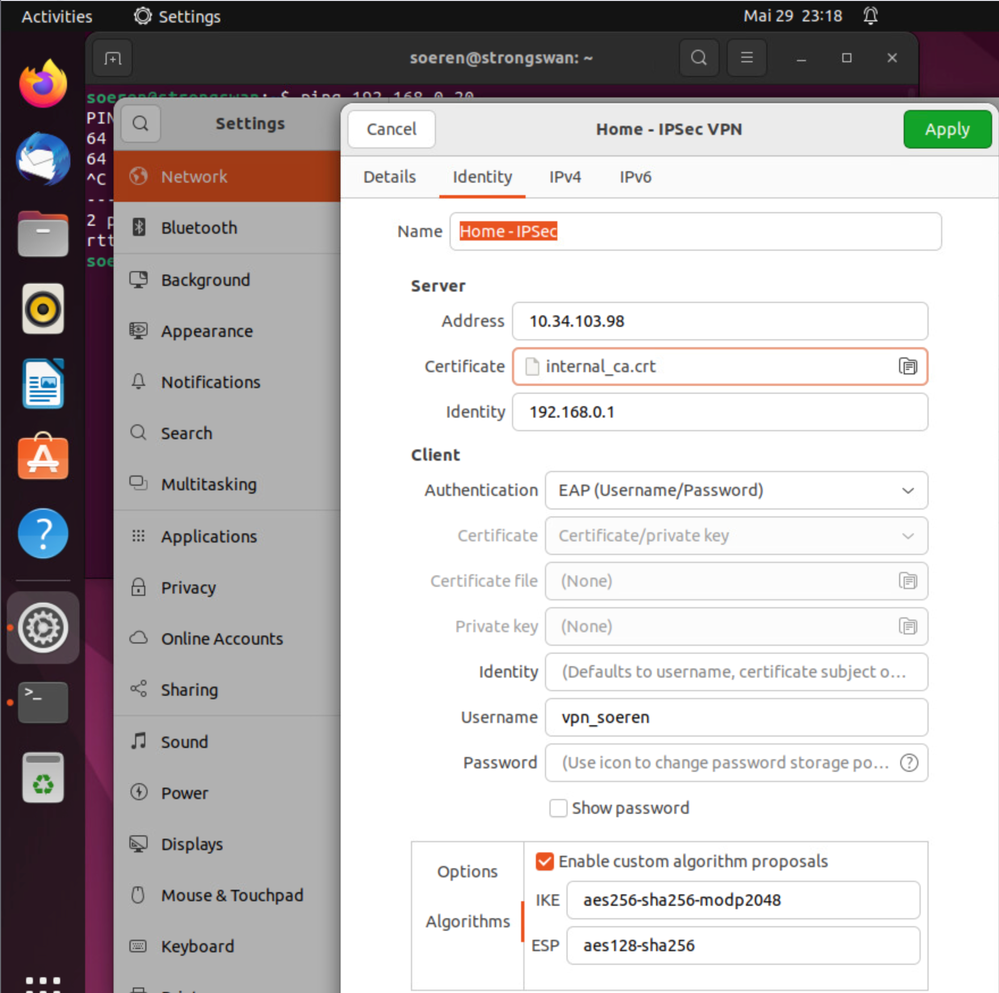
Username / Password Authentication
Gateway:
- R81.20 JF 10
Linux Client:
- Ubuntu 22.04
- strongSwan 5.9.5
- Network-Manager-StrongSwan 1.5.2
Ubuntu:
1) Install Network Manager strongSwan Plugin
$ sudo apt install network-manager-strongswan
These packages are also needed to connect successfully
$ sudo apt-get install libstrongswan-extra-plugins
$ sudo apt-get install libcharon-extra-plugins
$ sudo apt-get install strongswan
2) add the following to /etc/strongswan.conf
charon-nm {
load_modular = yes
send_vendor_id = yes
plugins {
include strongswan.d/charon/*.conf
attr {
dns = 1.1.1.1, 9.9.9.9
}
}
}
* charon-nm is used by the Network Manager only. Without the option "send_vendor_id=yes", the VPN won't come up. See also under Troubleshooting an example of the strongswan.conf file I use in my lab.
3) Restart ipsec service
$ systemctl restart ipsec
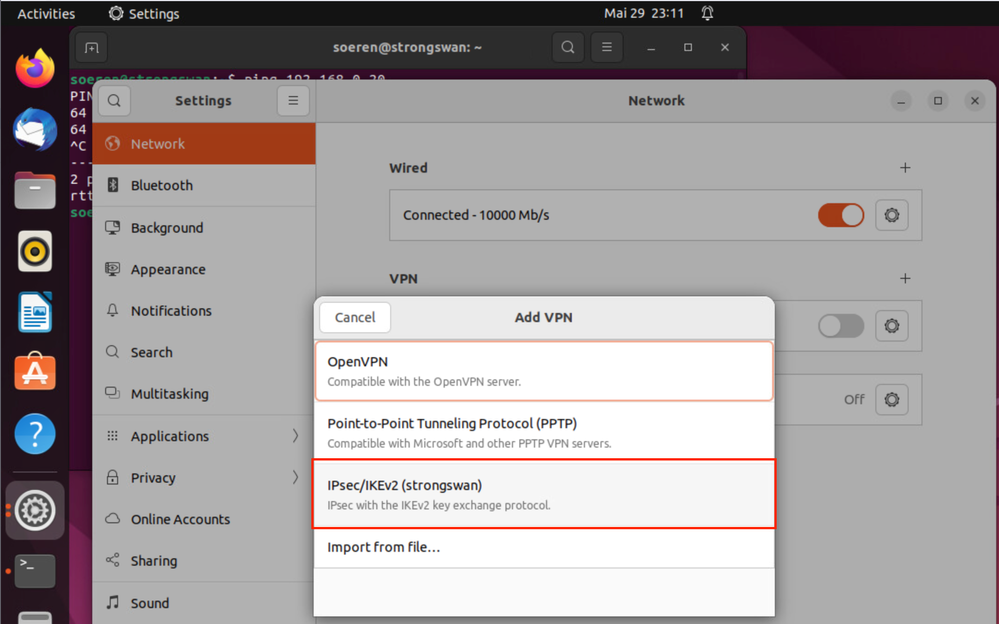
4) create IPSec Profile in Network Manager
Select: IPSec/IKEv2 (strongSwan)
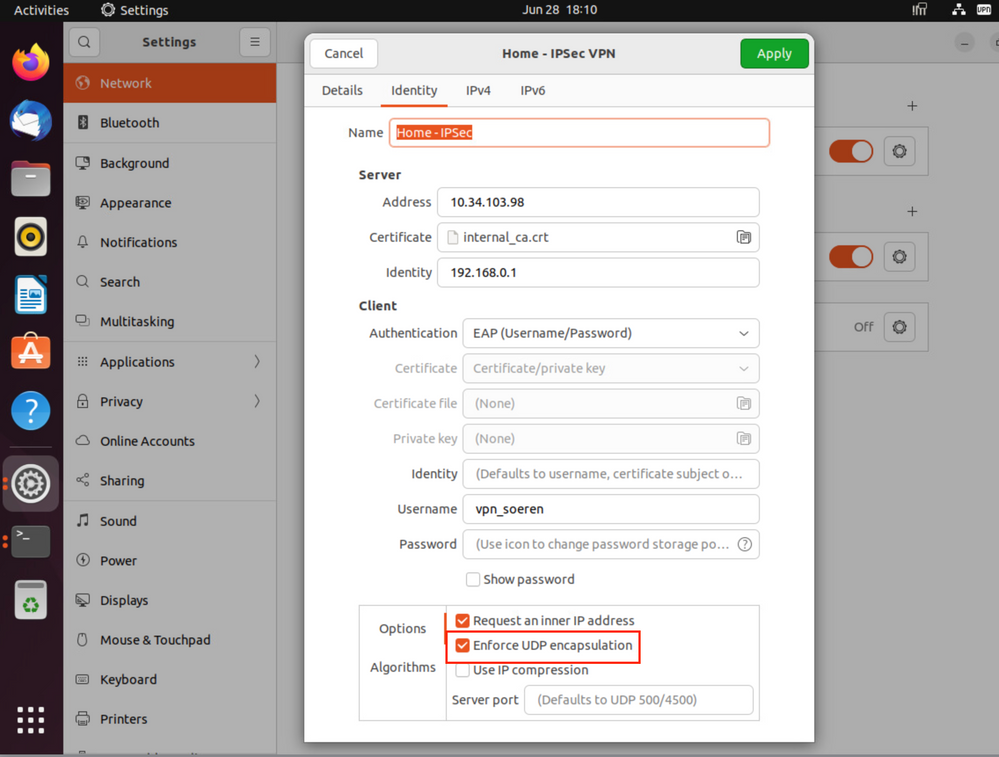
5) Configure Firewall IP Address etc. This is only an example of my Lab.
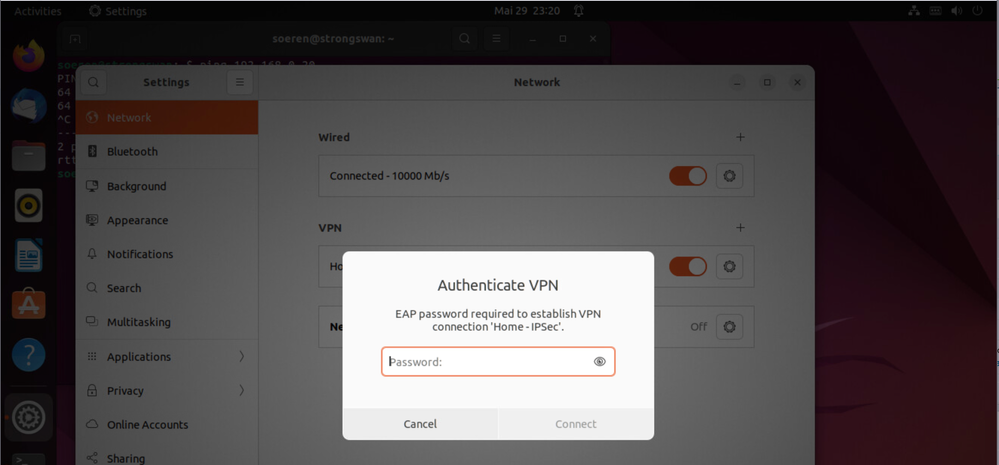
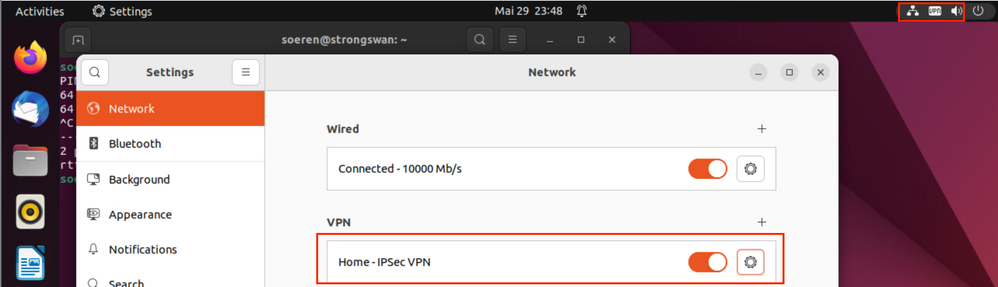
6) Connect to Gateway
Enter User Password and the Remote Access VPN should work.
7) Connected
Log Output - /var/log/syslog
May 29 23:20:21 strongswan charon-nm: 00[DMN] Starting charon NetworkManager backend (strongSwan 5.9.5)
May 29 23:20:21 strongswan charon-nm: 00[CFG] PKCS11 module '<name>' lacks library path
May 29 23:20:21 strongswan charon-nm: 00[PTS] TPM 2.0 - could not load "libtss2-tcti-tabrmd.so.0"
May 29 23:20:21 strongswan charon-nm: 00[LIB] plugin 'tpm': failed to load - tpm_plugin_create returned NULL
May 29 23:20:21 strongswan charon-nm: 00[LIB] providers loaded by OpenSSL: legacy default
May 29 23:20:21 strongswan NetworkManager[811]: <info> [1685395221.6499] manager: (tun0): new Tun device (/org/freedesktop/NetworkManager/Devices/4)
May 29 23:20:21 strongswan charon-nm: 00[LIB] created TUN device: tun0
May 29 23:20:21 strongswan systemd-udevd[4704]: Using default interface naming scheme 'v249'.
May 29 23:20:21 strongswan charon-nm: 00[CFG] loaded 0 RADIUS server configurations
May 29 23:20:21 strongswan charon-nm: 00[NET] using forecast interface ens160
May 29 23:20:21 strongswan charon-nm: 00[CFG] joining forecast multicast groups: 224.0.0.1,224.0.0.22,224.0.0.251,224.0.0.252,239.255.255.250
May 29 23:20:21 strongswan charon-nm: 00[CFG] HA config misses local/remote address
May 29 23:20:21 strongswan charon-nm: 00[CFG] loading ca certificates from '/etc/ipsec.d/cacerts'
May 29 23:20:21 strongswan charon-nm: 00[CFG] loading aa certificates from '/etc/ipsec.d/aacerts'
May 29 23:20:21 strongswan charon-nm: 00[CFG] loading ocsp signer certificates from '/etc/ipsec.d/ocspcerts'
May 29 23:20:21 strongswan charon-nm: 00[CFG] loading attribute certificates from '/etc/ipsec.d/acerts'
May 29 23:20:21 strongswan charon-nm: 00[CFG] loading crls from '/etc/ipsec.d/crls'
May 29 23:20:21 strongswan charon-nm: 00[CFG] loading secrets from '/etc/ipsec.secrets'
May 29 23:20:21 strongswan charon-nm: 00[LIB] dropped capabilities, running as uid 0, gid 0
May 29 23:20:21 strongswan charon-nm: 00[JOB] spawning 16 worker threads
May 29 23:21:53 strongswan charon-nm: 05[CFG] received initiate for NetworkManager connection Home - IPSec
May 29 23:21:53 strongswan charon-nm: 05[CFG] using gateway identity '192.168.0.1'
May 29 23:21:53 strongswan charon-nm: 05[IKE] initiating IKE_SA Home - IPSec[1] to 10.34.103.98
May 29 23:21:53 strongswan charon-nm: 05[ENC] generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) V ]
May 29 23:21:53 strongswan charon-nm: 05[NET] sending packet: from 10.34.103.200[55399] to 10.34.103.98[500] (484 bytes)
May 29 23:21:53 strongswan charon-nm: 13[NET] received packet: from 10.34.103.98[500] to 10.34.103.200[55399] (633 bytes)
May 29 23:21:53 strongswan charon-nm: 13[ENC] parsed IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_S_IP) N(NATD_S_IP) N(NATD_S_IP) N(NATD_S_IP) N(NATD_S_IP) N(NATD_S_IP) N(NATD_D_IP) CERTREQ ]
May 29 23:21:53 strongswan charon-nm: 13[CFG] selected proposal: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
May 29 23:21:53 strongswan charon-nm: 13[IKE] local host is behind NAT, sending keep alives
May 29 23:21:53 strongswan charon-nm: 13[IKE] received cert request for "O=home-fw..22erwk"
May 29 23:21:53 strongswan charon-nm: 13[IKE] received 1 cert requests for an unknown ca
May 29 23:21:53 strongswan charon-nm: 13[IKE] sending cert request for "O=home-fw..22erwk"
May 29 23:21:53 strongswan charon-nm: 13[IKE] establishing CHILD_SA Home - IPSec{1}
May 29 23:21:53 strongswan charon-nm: 13[ENC] generating IKE_AUTH request 1 [ IDi N(INIT_CONTACT) CERTREQ IDr CPRQ(ADDR ADDR6 DNS NBNS DNS6 DNS DNS6) SA TSi TSr N(MOBIKE_SUP) N(NO_ADD_ADDR) N(EAP_ONLY) N(MSG_ID_SYN_SUP) ]
May 29 23:21:53 strongswan charon-nm: 13[NET] sending packet: from 10.34.103.200[58460] to 10.34.103.98[4500] (368 bytes)
May 29 23:21:53 strongswan charon-nm: 16[NET] received packet: from 10.34.103.98[4500] to 10.34.103.200[58460] (1008 bytes)
May 29 23:21:53 strongswan charon-nm: 16[ENC] parsed IKE_AUTH response 1 [ IDr CERT AUTH EAP/REQ/ID ]
May 29 23:21:53 strongswan charon-nm: 16[IKE] received end entity cert "O=home-fw..22erwk, CN=home-fw VPN Certificate"
May 29 23:21:53 strongswan charon-nm: 16[CFG] using certificate "O=home-fw..22erwk, CN=home-fw VPN Certificate"
May 29 23:21:53 strongswan charon-nm: 16[CFG] using trusted ca certificate "O=home-fw..22erwk"
May 29 23:21:53 strongswan charon-nm: 16[CFG] reached self-signed root ca with a path length of 0
May 29 23:21:53 strongswan charon-nm: 16[CFG] checking certificate status of "O=home-fw..22erwk, CN=home-fw VPN Certificate"
May 29 23:21:53 strongswan charon-nm: 16[CFG] fetching crl from 'O=home-fw..22erwk, CN=ICA_CRL11' ...
May 29 23:21:53 strongswan charon-nm: 16[LIB] unable to fetch from O=home-fw..22erwk, CN=ICA_CRL11, no capable fetcher found
May 29 23:21:53 strongswan charon-nm: 16[CFG] crl fetching failed
May 29 23:21:53 strongswan charon-nm: 16[CFG] fetching crl from 'http://home-fw.example.de:18264/ICA_CRL11.crl' ...
May 29 23:21:53 strongswan charon-nm: 16[LIB] libcurl request failed [6]: Could not resolve host: home-fw.example.de
May 29 23:21:53 strongswan charon-nm: 16[CFG] crl fetching failed
May 29 23:21:53 strongswan charon-nm: 16[CFG] certificate status is not available
May 29 23:21:53 strongswan charon-nm: 16[IKE] authentication of '192.168.0.1' with RSA signature successful
May 29 23:21:53 strongswan charon-nm: 16[IKE] server requested EAP_IDENTITY (id 0xD4), sending 'vpn_soeren'
May 29 23:21:53 strongswan charon-nm: 16[ENC] generating IKE_AUTH request 2 [ EAP/RES/ID ]
May 29 23:21:53 strongswan charon-nm: 16[NET] sending packet: from 10.34.103.200[58460] to 10.34.103.98[4500] (96 bytes)
May 29 23:21:53 strongswan charon-nm: 07[NET] received packet: from 10.34.103.98[4500] to 10.34.103.200[58460] (80 bytes)
May 29 23:21:53 strongswan charon-nm: 07[ENC] parsed IKE_AUTH response 2 [ EAP/REQ/GTC ]
May 29 23:21:53 strongswan charon-nm: 07[IKE] server requested EAP_GTC authentication (id 0xD5)
May 29 23:21:53 strongswan charon-nm: 07[ENC] generating IKE_AUTH request 3 [ EAP/RES/GTC ]
May 29 23:21:53 strongswan charon-nm: 07[NET] sending packet: from 10.34.103.200[58460] to 10.34.103.98[4500] (96 bytes)
May 29 23:21:53 strongswan charon-nm: 08[NET] received packet: from 10.34.103.98[4500] to 10.34.103.200[58460] (80 bytes)
May 29 23:21:53 strongswan charon-nm: 08[ENC] parsed IKE_AUTH response 3 [ EAP/SUCC ]
May 29 23:21:53 strongswan charon-nm: 08[IKE] EAP method EAP_GTC succeeded, no MSK established
May 29 23:21:53 strongswan charon-nm: 08[IKE] authentication of 'vpn_soeren' (myself) with EAP
May 29 23:21:53 strongswan charon-nm: 08[ENC] generating IKE_AUTH request 4 [ AUTH ]
May 29 23:21:53 strongswan charon-nm: 08[NET] sending packet: from 10.34.103.200[58460] to 10.34.103.98[4500] (112 bytes)
May 29 23:21:54 strongswan charon-nm: 09[NET] received packet: from 10.34.103.98[4500] to 10.34.103.200[58460] (400 bytes)
May 29 23:21:54 strongswan charon-nm: 09[ENC] parsed IKE_AUTH response 4 [ AUTH N(CRASH_DET) CPRP(ADDR DNS DNS) SA TSi TSr N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) ]
May 29 23:21:54 strongswan charon-nm: 09[IKE] authentication of '192.168.0.1' with EAP successful
May 29 23:21:54 strongswan charon-nm: 09[IKE] IKE_SA Home - IPSec[1] established between 10.34.103.200[vpn_soeren]...10.34.103.98[192.168.0.1]
May 29 23:21:54 strongswan charon-nm: 09[IKE] scheduling rekeying in 35812s
May 29 23:21:54 strongswan charon-nm: 09[IKE] maximum IKE_SA lifetime 36412s
May 29 23:21:54 strongswan charon-nm: 09[IKE] installing DNS server 192.168.0.31 via resolvconf
May 29 23:21:54 strongswan charon-nm: 09[IKE] installing new virtual IP 192.168.1.168
May 29 23:21:54 strongswan avahi-daemon[808]: Registering new address record for 192.168.1.168 on ens160.IPv4.
May 29 23:21:54 strongswan charon: 10[KNL] 192.168.1.168 appeared on ens160
May 29 23:21:54 strongswan charon-nm: 09[IKE] received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
May 29 23:21:54 strongswan charon-nm: 09[CFG] selected proposal: ESP:AES_CBC_128/HMAC_SHA2_256_128/NO_EXT_SEQ
May 29 23:21:54 strongswan charon-nm: 09[IKE] CHILD_SA Home - IPSec{1} established with SPIs c0040ebd_i c0417c77_o and TS 192.168.1.168/32 === 10.34.103.1/32 10.34.103.98/32 172.18.0.1/32 192.168.0.0/24 192.168.2.0/24 192.168.4.1/32 192.168.207.0/24 192.168.222.1/32
May 29 23:21:54 strongswan charon: 15[KNL] interface tun0 activated
May 29 23:21:54 strongswan NetworkManager[811]: <info> [1685395314.8189] device (tun0): state change: unmanaged -> unavailable (reason 'connection-assumed', sys-iface-state: 'external')
May 29 23:21:54 strongswan NetworkManager[811]: <info> [1685395314.8199] device (tun0): state change: unavailable -> disconnected (reason 'connection-assumed', sys-iface-state: 'external')
May 29 23:21:54 strongswan NetworkManager[811]: <info> [1685395314.8204] device (tun0): Activation: starting connection 'tun0' (7e91075e-00b4-41ab-aea7-512e0a3ffc19)
May 29 23:21:54 strongswan NetworkManager[811]: <info> [1685395314.8207] device (tun0): state change: disconnected -> prepare (reason 'none', sys-iface-state: 'external')
May 29 23:21:54 strongswan charon: 12[KNL] fe80::5047:48eb:aeb1:877e appeared on tun0
May 29 23:21:54 strongswan charon: 08[KNL] 192.168.1.168 appeared on tun0
May 29 23:21:54 strongswan NetworkManager[811]: <info> [1685395314.8212] device (tun0): state change: prepare -> config (reason 'none', sys-iface-state: 'external')
May 29 23:21:54 strongswan dbus-daemon[809]: [system] Activating via systemd: service name='org.freedesktop.nm_dispatcher' unit='dbus-org.freedesktop.nm-dispatcher.service' requested by ':1.3' (uid=0 pid=811 comm="/usr/sbin/NetworkManager --no-daemon " label="unconfined")
May 29 23:21:54 strongswan systemd[1]: Starting Network Manager Script Dispatcher Service...
May 29 23:21:54 strongswan NetworkManager[811]: <info> [1685395314.8259] device (tun0): state change: config -> ip-config (reason 'none', sys-iface-state: 'external')
May 29 23:21:54 strongswan NetworkManager[811]: <info> [1685395314.8264] device (tun0): state change: ip-config -> ip-check (reason 'none', sys-iface-state: 'external')
May 29 23:21:54 strongswan charon-nm: 10[KNL] interface tun0 activated
May 29 23:21:54 strongswan dbus-daemon[809]: [system] Successfully activated service 'org.freedesktop.nm_dispatcher'
May 29 23:21:54 strongswan systemd[1]: Started Network Manager Script Dispatcher Service.
May 29 23:21:54 strongswan charon-nm: 14[KNL] fe80::5047:48eb:aeb1:877e appeared on tun0
May 29 23:21:54 strongswan charon-nm: 06[KNL] 192.168.1.168 appeared on tun0
May 29 23:21:54 strongswan systemd-resolved[629]: ens160: Bus client set default route setting: no
May 29 23:21:54 strongswan systemd-resolved[629]: ens160: Bus client reset DNS server list.
May 29 23:21:54 strongswan systemd-resolved[629]: tun0: Bus client set default route setting: yes
May 29 23:21:54 strongswan systemd-resolved[629]: tun0: Bus client set DNS server list to: 192.168.0.21
May 29 23:21:54 strongswan NetworkManager[811]: <info> [1685395314.8421] device (tun0): state change: ip-check -> secondaries (reason 'none', sys-iface-state: 'external')
May 29 23:21:54 strongswan NetworkManager[811]: <info> [1685395314.8430] device (tun0): state change: secondaries -> activated (reason 'none', sys-iface-state: 'external')
May 29 23:21:54 strongswan NetworkManager[811]: <info> [1685395314.8446] device (tun0): Activation: successful, device activated.
May 29 23:21:54 strongswan charon: 13[NET] using forecast interface ens160
May 29 23:21:54 strongswan charon: 13[CFG] joining forecast multicast groups: 224.0.0.1,224.0.0.22,224.0.0.251,224.0.0.252,239.255.255.250
May 29 23:21:54 strongswan charon-nm: 16[NET] using forecast interface ens160
May 29 23:21:54 strongswan charon-nm: 16[CFG] joining forecast multicast groups: 224.0.0.1,224.0.0.22,224.0.0.251,224.0.0.252,239.255.255.250
May 29 23:22:04 strongswan systemd[1]: NetworkManager-dispatcher.service: Deactivated successfully.
May 29 23:22:29 strongswan charon-nm: 16[IKE] sending keep alive to 10.34.103.98[4500]
Troubleshooting:
Linux Client:
Check /var/log/syslog for any issues.
Example:
This is my ipsec.conf and strongswan.conf.
/etc/ipsec.conf
You don't need this file for the Network Manager to work. This is only an example for the CLI connect and for comparison with the values I entered into the Network Manager GUI above.
# ipsec.conf - strongSwan IPsec configuration file
# basic configuration
config setup
# strictcrlpolicy=yes
# uniqueids = no
# Add connections here.
conn home
auto=add
type=tunnel
leftfirewall=yes
rightauth=pubkey
leftauth=eap-gtc
keyexchange=ikev2
eap_identity=install
left=%any
leftsourceip=%config
right=10.34.103.98
rightid=192.168.0.1
rightsubnet=0.0.0.0/0
ike=aes256-sha256-modp2048
esp=aes128-sha256
ikelifetime=8h
lifetime=1h
reauth=yes
rekey=yes
margintime=1m
rekeyfuzz=50%
dpdaction=restart
dpddelay=30s
dpdtimeout=60s
/etc/strongswan.conf
There are two sections, charon-nm is used by the Network Manager und charon is used for the CLI. For Network Manager to work, you only need charon-nm section.
# strongswan.conf - strongSwan configuration file
#
# Refer to the strongswan.conf(5) manpage for details
#
# Configuration changes should be made in the included files
charon-nm {
load_modular = yes
send_vendor_id = yes
plugins {
include strongswan.d/charon/*.conf
attr {
dns = 192.168.0.21, 192.168.0.31
}
}
}
charon {
load_modular = yes
send_vendor_id = yes
plugins {
include strongswan.d/charon/*.conf
attr {
dns = 192.168.0.21, 192.168.0.31
}
}
}
include strongswan.d/*.conf
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Wow, very informative, thanks for sharing 👍
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Sören,
thanks for the instructions!
Following this we were able to successfully connect to our firewall, but the connections only work for 15 minutes.
This 15 minute interval coincides exactly with the time for the dhcp leases for the machines. (We are using the option to assign Office Mode IPs automatically using a Windows DHCP Server).
After the 15 minutes the client still tries to send traffic using the vpn connection, but the firewall logs an encryption failure for every connection: "According to the policy the packet should not have been decrypted"
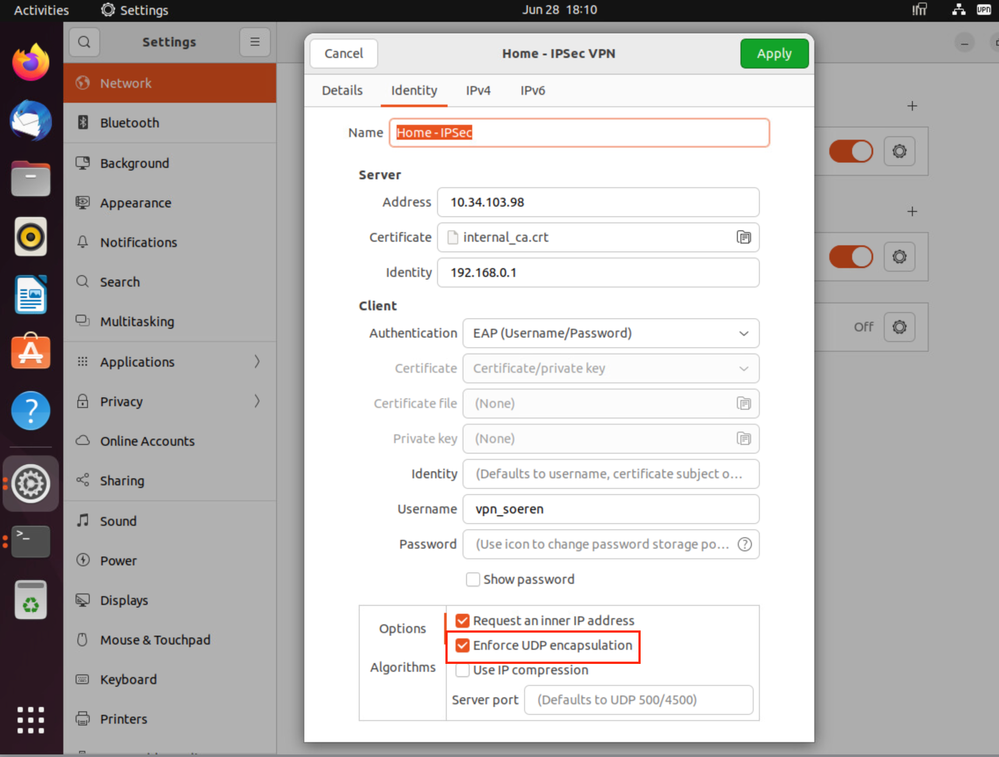
If we assign the IPs via usage of the ipassignment.conf, the connections last for nearly three hours, but still disconnect after that.
Have you experienced similar problems? How do you assign Office Mode IPs?
Thank you
Björn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I tried to replicate the issue and it happened to me too. In my setup I also use a DCHP server to get an Office Mode IP Address. The connection was established at 07:55 am and it stopped working at 10:42 am, almost 3 hours later.
I will debug this issue and I will post my results later on.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please try "Enforce UDP Encapsulation". In my lab setup it worked using this option.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Wow this was a great help.
I am running R81.20 and Linux Mint 21.2 Cinnamon.
Network manager is the way to go on Linux and VPN to Check Point.
I also managed to get 2FA working by selecting RADIUS as a authentication method on R81.20 gateway.
Thank you 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is a great guide, however my CHeckpoint is dropping my connecitons because it's using IKEv2. ANy guidance? I've tried my best to find an easy guide on getting StrongSwan to work on my Ubuntu laptop with no luck (using Certificate auth)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Which Check Point version do you use?
Did you follow the steps described here:
IKEv2 is fine and should work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have this solution support for connect Ubuntu Linux 2FA with OTP token get from the FortiToken mobile auth application.
My team uses Checkpoint Remote Access Client entering the username/password -> connecting and response -> enters OTP token get from FortiToken
But I config as tutorial IPSec/IKEv2 (strongSwan) not work, and I don't see how to input OTP token
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Please check the the following doc: https://sc1.checkpoint.com/documents/R81.10/WebAdminGuides/EN/CP_R81.10_RemoteAccessVPN_AdminGuide/T...
The 2FA is not supported with Strongswan.
Kind Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
MFA only works if you enter the token code + password at the same time, such as "123456Password" as your password.
In my lab I use a FreeIPA server with password and token authentication, connected to my Check Point Firewall via LDAP. It should also work when using RSA for example.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Soren,
I'm aware that works, I'm just saying that is not supported.
From a partner point of view that is something worth to consider when you try to deploy something. It's always what I say to my end customers. If you are willing to deal with all the issues of being on your own, then it's ok. 🙂
Regards
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 16 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Tue 13 May 2025 @ 04:00 PM (CEST)
German Session: NIS2- Compliance: Effiziente Vorbereitung und UmsetungTue 13 May 2025 @ 04:00 PM (CEST)
Maestro Masters EMEA: Quantum Maestro Architectures and OptimizationTue 13 May 2025 @ 02:00 PM (EDT)
Maestro Masters Americas: Quantum Maestro Architectures and OptimizationWed 14 May 2025 @ 10:00 AM (CEST)
ATAM 360°: Elevate Your Cyber Security Strategy with Proactive services - EMEAWed 14 May 2025 @ 03:00 PM (CEST)
NIS2 Readiness: Assess, Secure, and Comply with ConfidenceWed 14 May 2025 @ 10:30 AM (BRT)
Transforme sua Segurança de Rede com Agilidade e EficiênciaTue 13 May 2025 @ 04:00 PM (CEST)
Maestro Masters EMEA: Quantum Maestro Architectures and OptimizationTue 13 May 2025 @ 02:00 PM (EDT)
Maestro Masters Americas: Quantum Maestro Architectures and OptimizationWed 14 May 2025 @ 10:00 AM (CEST)
ATAM 360°: Elevate Your Cyber Security Strategy with Proactive services - EMEAWed 14 May 2025 @ 03:00 PM (CEST)
NIS2 Readiness: Assess, Secure, and Comply with ConfidenceWed 14 May 2025 @ 10:30 AM (BRT)
Transforme sua Segurança de Rede com Agilidade e EficiênciaWed 14 May 2025 @ 05:00 PM (CEST)
ATAM 360°: Elevate Your Cybersecurity Strategy with Proactive services - AMERICASThu 15 May 2025 @ 09:00 AM (IDT)
PA In-Person CloudGuard Workshop (CGNS, WAF, & API Security)About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter