- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- VPN tunnel does not ping the address
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
VPN tunnel does not ping the address
Good afternoon friends.
Tell me please, I have checkpoint 1590 under local control. I set up a vpn tunnel with the address, the tunnel is active, but after that this address is not pinged and the tracert command does not work.
What else do I need to do to get access to the desired address.
Grateful for any help
30 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What is your precise configuration?
Please provide descriptions (with screenshots) and a basic network diagram.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We definitely need some more info...please provide IP in question, basic routing, config, maybe as @PhoneBoy asked, also network diagram would help (even something in MS paint).
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My external address is (for example) 194.1.1.1, the tunnel is set from 86.1.1.1, the internal address of the desired network is 172.17.0.0 in the tunnel settings, on the other hand my network is 192.168.1.0. There is no ping. I turn off the tunnel - there is a ping on 86.1.1.1. I allow the addresses 86.1.1.1 and 172.0.0.0 in the policies - there is no ping.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What shows up in the logs when you attempt to do this ping?
Have you done any troubleshooting with tcpdump and similar to see if traffic is actually being encrypted and sent to the remote end?
Precise configuration steps taken (with screenshots) would go a long way towards helping you solve the issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
when I ping 172.17.0.172 - the log is empty.
if you can write the exact tunnel setup to get from the network 192.168.1.0 to 172.17.0.0?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I did everything in your link, but it still doesn't work.
I have in the device-routing section - when creating a new route, the next hop vti (tunnel) is not active.
this is normal?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What is the remote end of the VPN in this case?
What precisely (with screenshots) have you configured on your end?
If you don't want to share this publicly, I recommend working with our TAC.
Also, for debugging, see: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
on my side, a tunnel is configured to address 194.1.1.1. its internal network is 172.17.0.0. On its side is my address 86.1.1.1. and my internal network is 192.168.0.0. In the tunnel settings, ipsec is specified - the tunnel is active.
But, there is no ping to the address 194.1.1.1, I turn off the tunnel - there is a ping.
In politicians allowed everything to the address 194.1.1.1. and 172.17.0.0.
What else needs to be done?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
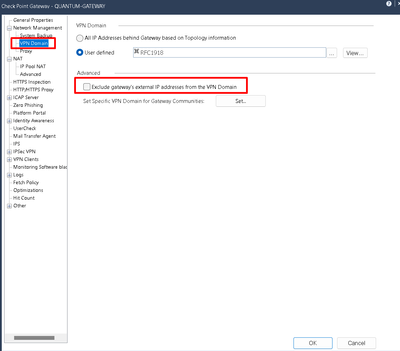
I am sorry I have not looked up the entire configuration but are you trying to ping peer IP from your firewall which is establishing a VPN tunnel? And if so then you wont be able to as a design. You can probably excldue echo-request from the VPN community and try?
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes - It wont be able to ping peer IP address for VPN.
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
why, please tell me the solution?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As I said you can create a custom tunnel with crypt.def and exclude the peer IP since this is known and documented solution or exclude echo-request from tunnel but this way no one will be able to ping through tunnel.
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We automatically include the Peer IP as part of the encryption domain on our end.
It’s covered in scenario 3 here: https://supportcenter.checkpoint.com/supportcenter/portal?action=portlets.SearchResultMainAction&eve...
If this SMB device is self-managed, you can apply the same fix.
However, getting it to be effective will mean making a change to the access policy or forcing it via the CLI (forget the exact command for this).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just curious, what happens if you trace route to that IP? Does it even take any hops? If you say it works without VPN, can you send us the path you get?
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes that is right!! It never goes out. It drops the connection
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I ask you to be condescending, I'm just starting to master checkpoint1590,
tell me what exactly I need to do to set it up, step by step?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey @Dmitryfd ,
No one is condescending, we are simply doing our best to help you. @Blason_R actually gave good suggestion. I believe he was referring to below article:
But, can you please answer what I asked before if you dont mind? It would be good if we could see trace route to that external IP through the tunnel and when it works.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@the_rockhas given the correct link and @Dmitryfd as I said unfortunately its not possible without those efforts. I am not sure how do you exclude the IP address from community the way we do it on mgmt server. I use to do the same way. exclude the echo-request from vpn community and then PING if that succeed then add it in community again.
Or here is one more trick. NAT the traffic going to PEER IP Address behind other IP and you should be able to ping to Peer IP like this
Lets suppose your encryption domain is 10.1.1.0/24
FW IP is 1.1.1.1
Peer IP is 2.2.2.2
Then nat one of the IP fro 10.1.1.0 like 10.1.1.100 behind 1.1.1.2 - Since now 1.1.1.2 and 2.2.2.2 is not a part of vpn tunnel you should be able to ping from encryption domain.
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good point indeed. Something slightly unrelated, but pretty cool feature in R81.20
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Something came to my mind about this...apologies, I dont deal with those SMB appliances much, so forgive me for my ignorance, but I wonder if it gives you ability to create groups with exclusions that you can use as enc domain? If so, I have a good feeling that may work.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Gentlemens, unfortunately, my knowledge does not allow me to quickly and fully immediately implement all the tips.
Thank you for your help. I will study your answers.
Thanks again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Message me, lets do quick remote, I will help you.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
how can you connect?
maybe through anydesk?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I dont like using anydesk, sorry, not a trusting software for me. Zoom or webex is fine.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you offer video conferencing connection?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why cant we simply do zoom or webex? We dont need video conferencing lol
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
provide a link to the webex-client?
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter