- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure Users and Access)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
May the 4th (+4)
Roadmap Session and Use Cases for
Cloud Security, SASE, and Email Security
SASE Masters:
Deploying Harmony SASE for a 6,000-Strong Workforce
in a Single Weekend
Paradigm Shifts: Adventures Unleashed!
Capture Your Adventure for a Chance to WIN!
Mastering Compliance
Unveiling the power of Compliance Blade
CPX 2024 Content
is Here!
Harmony SaaS
The most advanced prevention
for SaaS-based threats
CheckMates Go:
CPX 2024 Recap
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Remote Access VPN
- :
- SAML SSO asking for Authentication Method
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
SAML SSO asking for Authentication Method
I am setting up a second Checkpoint Client VPN solution using SAML SSO authentication on a new Gateway. We have the existing solution working perfectly on the old gateway. When a user tries to connect, they are passed through to the SAML provider where authentication is performed, and away they go.
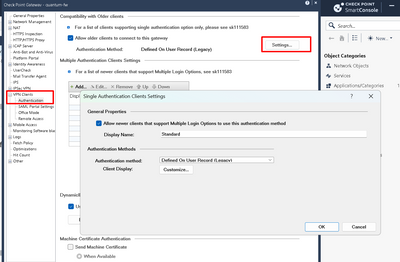
I have copied all the same settings and have set up a new Identity Provider for the new VPN, however when connecting it is asking for an authentication method despite it being set to use SSO, as per the attached picture. On the existing (working) one this option simply never comes up.
Can anyone point me in the right direction as to what might be causing this.
The gateways VPN Clients Authentication is set to use the identity provider (GCP_SSO_WOF) and the Gateway is, paired to the applicable SAML Identity provider, with the service set to Remote Access VPN.
I figure I have missed something, somewhere, but this is doing my head in. I am following the identical setup to the previous gateway and am getting a different result! Thanks
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To follow this up and close it off, though we were well above the minimum required version and patches required for this to work, something somewhere must have messed up deep inside the bowels of the firewalls. We tried a reboot, that achieved nothing. We had another permissions issue which we resolved but that also had no impact, final as we were almost ready to put these boxes into production we applied the latest available patches, and after then the option suddenly started working.
So the root cause is unknown, however somehow the patch process resolved the issue. I'm guessing somewhere some file was re-written and that fixed it. Although we spent way too long troubleshooting this I am happy that it never impacted production workloads so will not be investigating further.
If anyone comes across this thread, experiencing similar, I recommend going ahead and applying the newest available patches early on in your troubleshooting.
Thanks Matt
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Im pretty sure you are missing the right setting on gateway object in dashboard, under vpn clients or something, cant recall exact setting now, but can check in the lab tomorrow. There should be an option for authentication, just make sure its same as other working gateway.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am wanting only to permit the VPN Client, using only Check Point Mobile for Windows.
Under VPN Clients I have desktops checked with only Checkpoint Mobile for windows, nothing else (though I have tested all of these). For Authentication I have disabled to older client compatibility, and under Multiple Auth have added my Identity Provider as the first option and username/password as the second. This second option will be removed as soon as I get SSO going.
Under Dynamic ID Settings I have the Use Global settings checked.
The SAML Portal settings only have my URL and certificate set.
Office mode is set, and the ip ranges have been defined and policy permitted.
The Mobile Access section does not use SSO as we do not use it.
In the shared mobile access policy I have set all the permissions the same.
The firewalls do have outbound internet access.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is what I was referring to.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We're not enabling the older clients which don't support multiple logon, however I have tested that. There is one surprise I've just noticed and that has me scratching my head. When I tested the above, SSO/SAML was not available in the drop down box for Authentication methods. This might be normal though as that's for really old clients which wouldn't support SSO anyway as far as I am aware.
Thanks Matt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To follow this up and close it off, though we were well above the minimum required version and patches required for this to work, something somewhere must have messed up deep inside the bowels of the firewalls. We tried a reboot, that achieved nothing. We had another permissions issue which we resolved but that also had no impact, final as we were almost ready to put these boxes into production we applied the latest available patches, and after then the option suddenly started working.
So the root cause is unknown, however somehow the patch process resolved the issue. I'm guessing somewhere some file was re-written and that fixed it. Although we spent way too long troubleshooting this I am happy that it never impacted production workloads so will not be investigating further.
If anyone comes across this thread, experiencing similar, I recommend going ahead and applying the newest available patches early on in your troubleshooting.
Thanks Matt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What version/JHF of gateway/management are you doing this on?
Unless it’s all R81.20, you’ll probably need the script (among other things) from here: https://support.checkpoint.com/results/sk/sk172909
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yeah, the magic script. I have run that and made the required database changes. I'm on R81.10 at the moment. I also have an existing SAML SSO solution which is working perfectly from the same manager.
I have noted that the Metadata file provided to me from the SAML provider for this gateway is identical to the file provided by them for the previous gateway. I have asked about this and asked them to check if perhaps somehow they have provided me with a duplicate copy of the old file instead of a new one. At their far end both gateways are talking to the same SAML service, so it is quite possible this is correct.
Overnight last night I worked through as many different options as I could try and nothing has changed the behavior. The existing one works fine, though it now attempts to connect to the new gateway, fails and so connects to the existing gateway. That's weird given I've disabled MEP, but I guess this is because both gateways participate in the remote access community.
I have deployed similar for another client with 4 gateways and that has worked fine across all the gateways which are all in the same community, so I don't think that's an issue.
Thanks Matt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The file from the provider is definitely correct, so that rules that one out too.
I note R81.20 has a few fixes for SSO and I wonder if that would help, but our manager is a cloud based installation and R81.20 is not yet available to it. R81.10 Take 109 is the latest on the Available Updates page. I will upgrade to that on Friday, unless R81.20 magically becomes available.
Does anyone happen to know when this might become available to cloud installations?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you meant Smart-1 cloud mgmt server, R81.20 had been available for at least 6 months now. But, only CP can install it, not you.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Definitely not S1C, for sure. Honestly, at this point, I would consult with TAC and see if this can be fixed via remote session.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Per SK172909
- make sure that you Mgmt server and gateways are correct version plus jumbo.
- Verify that the script has been run on the environment if required.
- Verify that the Gateway has the Authentication available. Gateway object >> vpn client >> authentication
- verify that the client is on the SAML supported version or higher, anything E86.00 or higher will work.
If the issue persists, please open a Support Ticket with TAC.
SK172909 also has a section for initial configuration troubleshooting steps that resolves most first time issues.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Trending Discussions
Upcoming Events
Thu 02 May 2024 @ 10:00 AM (CEST)
CheckMates Live BeLux: How Can Check Point AI Copilot Assist You?Thu 02 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - Keine Kompromisse - Sicheres SD-WANThu 02 May 2024 @ 10:00 AM (CEST)
CheckMates Live BeLux: How Can Check Point AI Copilot Assist You?Thu 02 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - Keine Kompromisse - Sicheres SD-WANAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
Facts at a Glance
User Center