Hi all,
there's 2 questions for this matter:
a) Is MEP with Identity Provider seamless? Will I only have to login once, or do I have to login to every single gateway again?
b) Is a bit more technical:
We have an environment, where we have a working MEP Configuration for Username/Password.
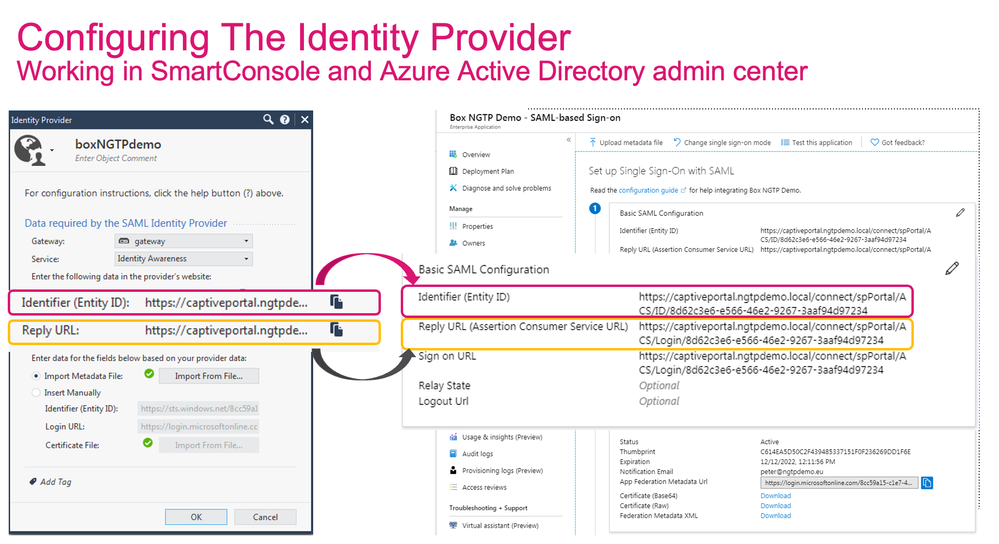
We're trying to change to Azure AD Auth with SAML / Identity Provider.
I've gone through the AdminGuide for SAML Support
(https://sc1.checkpoint.com/documents/R81.10/WebAdminGuides/EN/CP_R81.10_RemoteAccessVPN_AdminGuide/T...)
and configured my Identity Provider, added a second Login Option for Identity Provider Usage and gone through the GuiDBedit part.
For MEP, there is only one remark under "Step 4: Configure the Identity Provider as an Authentication Method":
Note - For Remote Access Multiple Entry Point (MEP), you must configure the same Login Option on all Security Gateways that participate in MEP. Make sure to add all the Identity Provider objects (one per Security Gateway) to a dedicated Login Option.
Does this implicitely mean, that we have to create an Identity Provider Object for every single gateway that takes part in the Remote Access community and therefore gets added to the MEP configuration?
And secondary, "add all IDP objects (one per Security Gateway) to a dedicated Login Option", does this mean, that I need one addtional login option with all configured Identity Providers, or do I need a separate one for each Identity Provider, given that I might indeed have to create an IDP for each participating gateway?
The Setup is that everyone connects to the main site (That one got the Identity Provider configured above), and then uses MEP to get to other sites afterwards.
Question is, can other MEP Gateways simply use the already established user verification somehow and I missed that point, or do we have to login to every gateway indeed?
In the current config: After the initial successful SAML login to the main site, the next site comes up and gives us another Identity Provider login which then fails.
Best Regards,
Jonas