- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- Re: Remote Access VPN - Overlap Network in VPN Dom...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
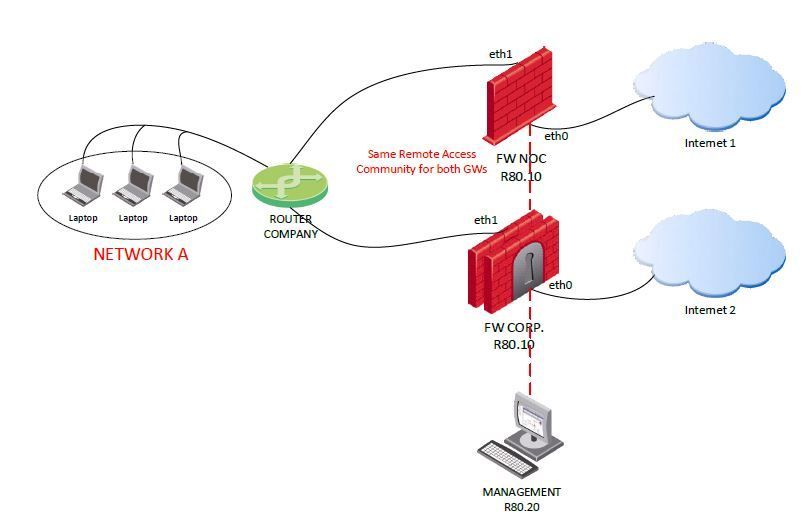
Remote Access VPN - Overlap Network in VPN Domains
Hello everyone,
I have the following scenario:
- A cluster (FW Corp) and a GW (FW NOC) on R80.10 managed by the same SMS.
- Remote access (VPN) is required for FW Corp and FW NOC.
- Users who log in through FW Corp and FW NOC must have to access the same network. (NETWORK A according to diagram)
Is it possible to have the same network (NETWORK A) in the VPN domains (overlap) for both GWs: FW Corp and FW NOC? considering that they share the same remote access community.
Additionally, FW Corp and GW have other networks declared in their VPN domains not common to each other. Only NETWORK A is the only one in common between GWs.
5 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
NETWORK A should be loadbalanced in this case. The users will use only single IP to access resources and LB will pass the packet to the selected GW based on criteria specified by LB mechanism.
Or you can use different NETWORK B (dummy, only part of 1 GW) and translate it to NETWORK A.
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you very much for your reply.
According what you're saying. I understand that it is not possible to use the same network (NETWORK A) in both encryption domains for remote access VPN. I assume this depends on the 2 domains declared in the same community (Remote Access Community).
An additional fact is that each FW has configured office mode with a different IP pool.
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello mashls4,
what you want is possible. The keyword is MEP ( Multiple Entry Point ).
With MEP you have more then one gateway with the same encryption domain. And if you have different IP-pools for remote-access clients connecting to different gateways, this will be fine. You don‘t need to NAT your remote clients, the returning packets can be routed according to the entry gateway.
Had a look at the documentation:
Remote Access VPN R80.10 and Higher Administration Guide
and search for MEP or multiple entry point.
Your need is described in the part „The need for Multiple Entry Point security gateways“
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Wolfgang,
Thank you for your reply. However, according to the information you tell me, MEP is more to create a redundacy scenario with remote access VPN. It has 3 methods for the GW selection:
1. First to respond: Indicates that "to use the same VPN domain for the Security Gateways". In our case it does not apply because the VPN domain of each GW is different but they have a common network (NETWORK A). I mean (VPN DOMAIN 1= NETWORK A + NETWORK B and VPN DOMAIN 2= NETWORK A + NETWORK C)
2. Primary Backup: does not apply because both GWs have to operate with remote access VPN at the same time.
3. Load Distribution: Indicates that "the load distribution is dynamic and the remote client randomly selects a Security Gateway". In our case it does not apply because we don't want to balance the access of the VPNs. Each GW has to work independently of the other GW.
Additionally, NETWORK A is a network that has as a mask: 255.255.224.0. Which is extremely large. And for this reason we want to restrict access to different segments of this network depending on the GW (FW_Corp or FW_NOC).
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
mashls4,
having the same encryption domain on both gateways does not mean that you have access to all ressources internal.
You can define different remote access rules for you two gateways. Meaning FW_Corp has rules only allowing traffic to "VPN DOMAIN 1= NETWORK A + NETWORK B" and FW_NOC has rules only allowing traffic to "PN DOMAIN 2= NETWORK A + NETWORK C"
The let the client only use one gateway at the time you can configures these in the trac_client_1.ttm file.
With these file you control the behaviour of the VPN client.
Hope that's fit your requirements.
Wolfgang
PS.: Be aware you can have a different VPN domain for RemoteAccess and Site2Site VPN.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 3 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter