- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure Users and Access)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
May the 4th (+4)
Roadmap Session and Use Cases for
Cloud Security, SASE, and Email Security
SASE Masters:
Deploying Harmony SASE for a 6,000-Strong Workforce
in a Single Weekend
Paradigm Shifts: Adventures Unleashed!
Capture Your Adventure for a Chance to WIN!
Mastering Compliance
Unveiling the power of Compliance Blade
CPX 2024 Content
is Here!
Harmony SaaS
The most advanced prevention
for SaaS-based threats
CheckMates Go:
CPX 2024 Recap
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Remote Access VPN
- :
- Azure AD connection R81.10
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Azure AD connection R81.10
Hi community,
I got a customer with R80.10 JHF 75 gateway and MGMT on the same version.
We implemented Client VPN access with Azure AD and SAML via Identity Profiles and that is working fine.
Now we want to limit the users, who are allowed to connect in office mode.
We have a vpn-user group and limiting access via identity tags is working fine, but the users can still connect to the VPN and can drain the available office-mode pool.
So an AzureAD object for group mapping looks like the best shot.
We created the client-secret, noted the application ID from our enterprise app and also the tenant app, but if I test the connection, connection failed, please check the credentials supplied. Permissions for Graph and Read-All is set, the gateway and mgmt got internet access.
Any ideas? Has anyone made this running so far? We followed the steps described here: Using Azure AD for Authorization (checkpoint.com) and here https://community.checkpoint.com/fyrhh23835/attachments/fyrhh23835/cloudguard-saas/90/1/AzureService...
Looking forward to your inputs
Best Regards
Chacko
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I assume you mean R81.10 and not R80.10, correct?
R80.10 is End of Support and doesn’t support SAML.
In any case, I’m not clear on what is currently happening in your environment.
What precisely happens when a user tries to authenticate?
What do you see in the logs and such?
Screenshots of exactly what you’ve configured to support this configuration would help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi - right, 81.10.
Remote Access with VPN Client and SAML Authentication is working fine, but we would like to use Azure AD for the group mappings. We configured the Azure AD Enterprise App (which is working with SAML) and created a client secret, created a azure ad object in checkpoint, but if we try to retrieve any user/group mappings via access-roles or do a test connection, it fails with invalid credentials. All settings from the admin guide were double checked and the client-secret was copy/pasted, manually checked. Not sure how to troubleshoot, or if some configuration might be missed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you also follow: https://sc1.checkpoint.com/documents/R81/WebAdminGuides/EN/CP_R81_IdentityAwareness_AdminGuide/Topic...
Regardless, actual screenshots of error messages might be helpful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Are you running EndPoint Remote Access VPN client with office mode getting authenticated with SAML? hmmm I am keen to know that setup.
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Right, SAML auth and stuff is working.
Unfortunately, you need to pick the best of from differnet support documents and SKs until you get the full picture, but in the end it's working.
Only the group-mapping via AzureAD object doesn't want to work.
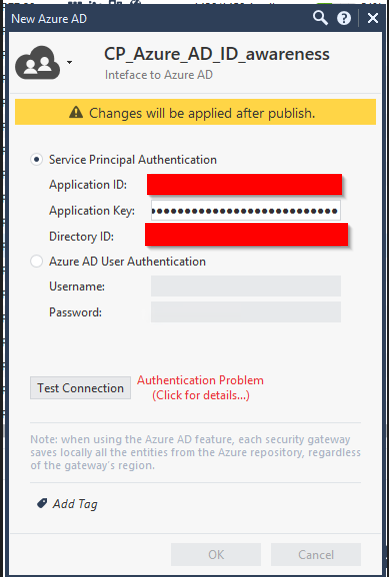
As screenshots were requested, here is the error - client secret was double checked and copied, so no way of typos and access rights are set as described in the documentation
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The only thing I can think of is the credentials don't allow access to the necessary API calls.
@Royi_Priov what's the best way to troubleshoot this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have the same problem. I defined the Azure AD object.
You can still save it if you select not to fix the error. However, I got th following message:
Does this means you cannot use the Service Principle Authentication option?
An Identity Provider object can only be created it either the VPN Remote access service is defined or the Mobile Access blade is enabled. This customer is not using either of them.
Why have the Service Principle Authentication option if it is not supported ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Hendri,
Just to check with you is this issue still haven't solved yet?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Muhamadarif,
I got integration with Azure AD to work properly. Having said that, I only configure it in R81.10 and beyond. I advise anyone to upgrade to R81.10 if they want it and still running version before R81.10. Using AD-identities much easier as of R81.10.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Understand.
Yeah i'm running on R81.10
Found out that the permission was wrong. did use application instead of user on api permission.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Trending Discussions
Upcoming Events
Thu 02 May 2024 @ 10:00 AM (CEST)
CheckMates Live BeLux: How Can Check Point AI Copilot Assist You?Thu 02 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - Keine Kompromisse - Sicheres SD-WANThu 02 May 2024 @ 10:00 AM (CEST)
CheckMates Live BeLux: How Can Check Point AI Copilot Assist You?Thu 02 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - Keine Kompromisse - Sicheres SD-WANAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
Facts at a Glance
User Center