- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Share your Cyber Security Insights
On-Stage at CPX 2025
Simplifying Zero Trust Security
with Infinity Identity!
CheckMates Toolbox Contest 2024
Make Your Submission for a Chance to WIN up to $300 Gift Card!
CheckMates Go:
What's New in R82
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Remote Access VPN
- :
- Re: Avoiding VPN client fingerprint message when c...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Avoiding VPN client fingerprint message when changing certificate
Hello Guys,
I'm in need to change the Certificate which is represented to the Clients for Remote Access.
As far as I Understand, Checkpoint presents the Fingerprint of the Root CA of the VPN Certificate so the client dont have issues when Certificates are exchanged if they come from the same CA.
Unfortunately we are moving from one CA to another and this is not clearly for me. Also not in SK: Avoiding VPN / SNX client fingerprint message when changing certificate or connecting to a backup si...
We have "vpn.corp.com" as CN/DNS. So I digged already into the registry of my clients and there as mentioned a respective fingerprint for my VPN Infrastructure.
[HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\CheckPoint\accepted_cn\vpn.corp.com]
"--Fingerprint--"=" XXXX XXX XXX XXX XXXX XXX XXXX XXXX XXX XXXX XXX XXXX"
1. Question: Can I assign more then one Fingerprint in the Registry ? So we have an entry for our "vpn.corp.com" and there is currently one Fingerprint. Can I enter the second (new one) to and it will work? Is there an SK for this?
So it will look like:
[HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\CheckPoint\accepted_cn\vpn.corp.com]
"--Fingerprint--"=" XXXX XXX XXX XXX XXXX XXX XXXX XXXX XXX XXXX XXX XXXX"
"--Fingerprint--"=" YYYY YYY YYY YYY YYYY YYY YYYY YYYY YYY YYYY YYY YYYY"
2. Question: If the 1. is not a viable option will I be forced to create a new DNS Entry (for example remote.corp.com) to prepare the registry? And also reflect this in the new certificate ?
[HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\CheckPoint\accepted_cn\remote.corp.com]
"--Fingerprint--"=" YYYY YYY YYY YYY YYYY YYY YYYY YYYY YYY YYYY YYY YYYY"
3. Question: I did not find the SK where it is cleary mentioned which fingerprint of which certificate checkpoint will present its clients. Is there something? Because even the SK above in the text says "From test host with VPN client installed and existing site created, export the following registry key value data:"
And this is quite hard in a live environment.
Regards
22 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It seems, you already did most of your investigative work, @electromichi3
Funny thing, your post title is almost identical to SK you cannot find.
Look into sk66263, that's all you need.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
yes as mentioned I found this article, but it is not clear for me if I change the fingerprint if I can enter just a second one in the windows registry. So the client will trust 2 fingerprints, then we migrate the certificate and then we remove the old fingerprint from the client.
I'm in need to let the user trust the old AND the new fingerprint because we cant push the registry key to all clients in the same moment where we replace the cert on the gateway
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Safest is to use different site IDs, such as you described in question 2. I would also check in the lab if you can have two fingerprints for a single site. Most probably not, but worth checking.
Also, are you moving CMA to a different IP or just moving the GW to another MGMT? If former, you can keep your fingerprint.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Regarding to question 3: What the CP VPN client is checking here is the RfC#1751 encoded representation of the SHA-1 fingerprint of the root certificate of your VPN GW SSL certificate chain.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Windows registry does not allow 2 of the same values in a registry key.
Working with support we were told this should work:
"--Fingerprint--"=" XXXX XXX XXX XXX XXXX XXX XXXX XXXX XXX XXXX XXX XXXX: YYYY YYY YYY YYY YYYY YYY YYYY YYYY YYY YYYY YYY YYYY"
Has not been tested yet, so if anyone tests, would like to hear back on results.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Jacinto_Rodrigu - did you ever get a chance to test this to see if it works.
Also, I know that CP uses the RFC 1751 to create the fingerprint in human text, but do they have a tool to determine the fingerprint without installing/replacing the current certificate on a gateway?
Also, do they plan to make it easier to manage the SSL cert for the MAB? With browsers all enforcing a max validity of 397 days, it means a lot more frequent update of the certificate than in the past, and it's a very manual process with about a dozen steps just to get a proper wildcard cert for a single gateway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Regarding "Also, I know that CP uses the RFC 1751 to create the fingerprint in human text, but do they have a tool to determine the fingerprint without installing/replacing the current certificate on a gateway?":
--> Maybe, I've never found one. So I used the C code from that RfC, compiled it and used it for converting in both directions. Please take care to use the SHA-1 fingerprint of the root certificate of your VPN GW SSL certificate chain. Not the fingerprint from the actual server certificate or any of the intermediate ones.
$ ./rfc_1751.exe "f9:02:bc:09:9a:9e:58:dc:28:6f:f6:4c:54:dd:71:e0:cf:29:f2:30"
Output: WEAN GAM ANT PRY SURF CURL MEW FEUD HALO LAIR SAUL TUBA
$ ./rfc_1751.exe "WEAN GAM ANT PRY SURF CURL MEW FEUD HALO LAIR SAUL TUBA"
Output: F9:02:BC:09:9A:9E:58:DC:28:6F:F6:4C:54:DD:71:E0
Back in R77 days, I remember it was possible to import the new certificate in SmartDashboard, NOT clicking ok or save, than copy the new fingerprint it shows to you, and than click cancel. Never tried this with R80+ and SmartConsole, maybe it is still working this way.
And as CP is only checking fingerprint of Root CA, there is no need to update trust on clients when you stay with that Root CA while changing server cert every year.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's what I thought, and I just confirmed that I have the same fingerprint on my two clusters that have the same Root CA. We must have switches Root CAs or the CA must have updated their Root certificate path the last time we renewed as it changed on us and we had to scramble to push out a registry edit to all client so that users didn't get the prompt.
How is everyone handling the need to renew a wildcard certificate every year with the new browser changes introduced over the past year forcing CAs to limit validity to 397 days? Any done any automation or use any 3rd party certificate management tools to help with this process?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just an update to myself. It's not the fingerprint of the Root CA, it's the CA that issued the certificate. So if you are using a traditional public CA that has a 2 tier hierarchy, it's the intermediate CA fingerprint that it used.
DigiCert Global Root CA
--> GeoTrust RSA CA 2018
---> portal.example.com
So in that example, it's the fingerprint on GeoTrust RSA CA 2018 that is used by the client for verification.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Could you please double check that?
In all the years I've doing this, it was always the fingerprint of the Root CA, never the one of the issuing CA or any other intermediate CA.
I've even checked some environments this morning, its always the fingerprint of the Root CA which is shown.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
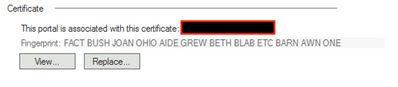
I did double-check.
The fingerprint shown from SmartConsole for the MAB certificate:
And the fingerprints for the Root CA and Subordinate CA (from SmartConsole, via the View option):
Click to Expand
Subject: CN=DigiCert Global Root CA,OU=www.digicert.com,O=DigiCert Inc,C=US
Issuer: CN=DigiCert Global Root CA,OU=www.digicert.com,O=DigiCert Inc,C=US
Not Valid Before: Thu Nov 9 19:00:00 2006 Local Time
Not Valid After: Sun Nov 9 19:00:00 2031 Local Time
Serial No.: 083be056904246b1a1756ac95991c74a
Public Key: RSA (2048 bits)
Signature: RSA with SHA1
Key Usage:
digitalSignature
keyCertSign
cRLSign
Basic Constraint:
is CA
MD5 Fingerprint:
79:E4:A9:84:0D:7D:3A:96:D7:C0:4F:E2:43:4C:89:2E
SHA-1 Fingerprints:
1. A8:98:5D:3A:65:E5:E5:C4:B2:D7:D6:6D:40:C6:DD:2F:B1:9C:54:36
2. KURD NEED ARTY RAID BRAE SOOT LOSE MOOR HOVE FIVE CURD HEWN
Subject: CN=GeoTrust RSA CA 2018,OU=www.digicert.com,O=DigiCert Inc,C=US
Issuer: CN=DigiCert Global Root CA,OU=www.digicert.com,O=DigiCert Inc,C=US
Not Valid Before: Mon Nov 6 07:23:45 2017 Local Time
Not Valid After: Sat Nov 6 08:23:45 2027 Local Time
Serial No.: 0546fe1823f7e1941da39fce14c46173
Public Key: RSA (2048 bits)
Signature: RSA with SHA256
CRL distribution points:
http://crl3.digicert.com/DigiCertGlobalRootCA.crl
Key Usage:
digitalSignature
keyCertSign
cRLSign
Extended Key Usage:
serverAuth
clientAuth
Basic Constraint:
is CA 0 levels
MD5 Fingerprint:
A9:5D:7F:13:A6:4A:5E:BE:00:36:4D:8B:E6:7D:EC:ED
SHA-1 Fingerprints:
1. 7C:CC:2A:87:E3:94:9F:20:57:2B:18:48:29:80:50:5F:A9:0C:AC:3B
2. FACT BUSH JOAN OHIO AIDE GREW BETH BLAB ETC BARN AWN ONE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Even worse, the fingerprint that the SNX client shows appears to be the fingerprint of the actual certificate, not the Intermediate or the Root CA as is used by the Endpoint Security client.
I just confirmed this on my SNX install. The fingerprint that the user is prompted to trust (or update every time the SSL certificate is updated) is from the actual SSL Server certificate, not the Intermediate or the Root CA.
Very confusing and hard to tell which fingerprint the user will see. Check Point needs an SK for this sort of information, so that it's clear which certificate fingerprint is used in which situation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Tobias_Moritz - Do you have your compiled rfc_1751 executable available anywhere (github/etc)? It's crazy that Check Point does not provide a simple tool for this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello EY, no I don't. And while I wanted to wrote something like: "just compile it yourself", I did a compare of my code in my archive against the orginal one from the RfC and found some things I changed to made it work (modified a helper function to support 16 instead of 8 bits, added one more helper function and the main function to make it a standalone-usable binary). Really forgot that, was a long time ago 😄
So here is my modified code from that RfC:
Click to Expand
/* This code originally appeared in the source for S/Key(TM),
* available in the directory
* ftp://thumper.bellcore.com/pub/nmh
*
* It has been modified only to remove explicit S/Key(TM) references.
*/
#include <stdio.h>
#include <string.h>
#include <assert.h>
#include <ctype.h>
#include <stdlib.h>
#ifdef __STDC__
#define __ARGS(x) x
#else
#define __ARGS(x) ()
#endif
static unsigned long extract __ARGS((char *s,int start,int length));
static void standard __ARGS((char *word));
static void insert __ARGS((char *s, int x, int start, int length));
static int wsrch __ARGS((char *w,int low,int high));
/* Dictionary for integer-word translations */
char Wp[2048][4] = { "A", "ABE", "ACE", "ACT", "AD", "ADA", "ADD",
"AGO", "AID", "AIM", "AIR", "ALL", "ALP", "AM", "AMY", "AN", "ANA",
"AND", "ANN", "ANT", "ANY", "APE", "APS", "APT", "ARC", "ARE", "ARK",
"ARM", "ART", "AS", "ASH", "ASK", "AT", "ATE", "AUG", "AUK", "AVE",
"AWE", "AWK", "AWL", "AWN", "AX", "AYE", "BAD", "BAG", "BAH", "BAM",
"BAN", "BAR", "BAT", "BAY", "BE", "BED", "BEE", "BEG", "BEN", "BET",
"BEY", "BIB", "BID", "BIG", "BIN", "BIT", "BOB", "BOG", "BON", "BOO",
"BOP", "BOW", "BOY", "BUB", "BUD", "BUG", "BUM", "BUN", "BUS", "BUT",
"BUY", "BY", "BYE", "CAB", "CAL", "CAM", "CAN", "CAP", "CAR", "CAT",
"CAW", "COD", "COG", "COL", "CON", "COO", "COP", "COT", "COW", "COY",
"CRY", "CUB", "CUE", "CUP", "CUR", "CUT", "DAB", "DAD", "DAM", "DAN",
"DAR", "DAY", "DEE", "DEL", "DEN", "DES", "DEW", "DID", "DIE", "DIG",
"DIN", "DIP", "DO", "DOE", "DOG", "DON", "DOT", "DOW", "DRY", "DUB",
"DUD", "DUE", "DUG", "DUN", "EAR", "EAT", "ED", "EEL", "EGG", "EGO",
"ELI", "ELK", "ELM", "ELY", "EM", "END", "EST", "ETC", "EVA", "EVE",
"EWE", "EYE", "FAD", "FAN", "FAR", "FAT", "FAY", "FED", "FEE", "FEW",
"FIB", "FIG", "FIN", "FIR", "FIT", "FLO", "FLY", "FOE", "FOG", "FOR",
"FRY", "FUM", "FUN", "FUR", "GAB", "GAD", "GAG", "GAL", "GAM", "GAP",
"GAS", "GAY", "GEE", "GEL", "GEM", "GET", "GIG", "GIL", "GIN", "GO",
"GOT", "GUM", "GUN", "GUS", "GUT", "GUY", "GYM", "GYP", "HA", "HAD",
"HAL", "HAM", "HAN", "HAP", "HAS", "HAT", "HAW", "HAY", "HE", "HEM",
"HEN", "HER", "HEW", "HEY", "HI", "HID", "HIM", "HIP", "HIS", "HIT",
"HO", "HOB", "HOC", "HOE", "HOG", "HOP", "HOT", "HOW", "HUB", "HUE",
"HUG", "HUH", "HUM", "HUT", "I", "ICY", "IDA", "IF", "IKE", "ILL",
"INK", "INN", "IO", "ION", "IQ", "IRA", "IRE", "IRK", "IS", "IT", "ITS",
"IVY", "JAB", "JAG", "JAM", "JAN", "JAR", "JAW", "JAY", "JET", "JIG",
"JIM", "JO", "JOB", "JOE", "JOG", "JOT", "JOY", "JUG", "JUT", "KAY",
"KEG", "KEN", "KEY", "KID", "KIM", "KIN", "KIT", "LA", "LAB", "LAC",
"LAD", "LAG", "LAM", "LAP", "LAW", "LAY", "LEA", "LED", "LEE", "LEG",
"LEN", "LEO", "LET", "LEW", "LID", "LIE", "LIN", "LIP", "LIT", "LO",
"LOB", "LOG", "LOP", "LOS", "LOT", "LOU", "LOW", "LOY", "LUG", "LYE",
"MA", "MAC", "MAD", "MAE", "MAN", "MAO", "MAP", "MAT", "MAW", "MAY",
"ME", "MEG", "MEL", "MEN", "MET", "MEW", "MID", "MIN", "MIT", "MOB",
"MOD", "MOE", "MOO", "MOP", "MOS", "MOT", "MOW", "MUD", "MUG", "MUM",
"MY", "NAB", "NAG", "NAN", "NAP", "NAT", "NAY", "NE", "NED", "NEE",
"NET", "NEW", "NIB", "NIL", "**bleep**", "NIT", "NO", "NOB", "NOD", "NON",
"NOR", "NOT", "NOV", "NOW", "NU", "NUN", "NUT", "O", "OAF", "OAK",
"OAR", "OAT", "ODD", "ODE", "OF", "OFF", "OFT", "OH", "OIL", "OK",
"OLD", "ON", "ONE", "OR", "ORB", "ORE", "ORR", "OS", "OTT", "OUR",
"OUT", "OVA", "OW", "OWE", "OWL", "OWN", "OX", "PA", "PAD", "PAL",
"PAM", "PAN", "PAP", "PAR", "PAT", "PAW", "PAY", "PEA", "PEG", "PEN",
"PEP", "PER", "PET", "PEW", "PHI", "PI", "PIE", "PIN", "PIT", "PLY",
"PO", "POD", "POE", "POP", "POT", "POW", "PRO", "PRY", "PUB", "PUG",
"PUN", "PUP", "PUT", "QUO", "RAG", "RAM", "RAN", "RAP", "RAT", "RAW",
"RAY", "REB", "RED", "REP", "RET", "RIB", "RID", "RIG", "RIM", "RIO",
"RIP", "ROB", "ROD", "ROE", "RON", "ROT", "ROW", "ROY", "RUB", "RUE",
"RUG", "RUM", "RUN", "RYE", "SAC", "SAD", "SAG", "SAL", "SAM", "SAN",
"SAP", "SAT", "SAW", "SAY", "SEA", "SEC", "SEE", "SEN", "SET", "SEW",
"SHE", "SHY", "SIN", "SIP", "SIR", "SIS", "SIT", "SKI", "SKY", "SLY",
"SO", "SOB", "SOD", "SON", "SOP", "SOW", "SOY", "SPA", "SPY", "SUB",
"SUD", "SUE", "SUM", "SUN", "SUP", "TAB", "TAD", "TAG", "TAN", "TAP",
"TAR", "TEA", "TED", "TEE", "TEN", "THE", "THY", "TIC", "TIE", "TIM",
"TIN", "TIP", "TO", "TOE", "TOG", "TOM", "TON", "TOO", "TOP", "TOW",
"TOY", "TRY", "TUB", "TUG", "TUM", "TUN", "TWO", "UN", "UP", "US",
"USE", "VAN", "VAT", "VET", "VIE", "WAD", "WAG", "WAR", "WAS", "WAY",
"WE", "WEB", "WED", "WEE", "WET", "WHO", "WHY", "WIN", "WIT", "WOK",
"WON", "WOO", "WOW", "WRY", "WU", "YAM", "YAP", "YAW", "YE", "YEA",
"YES", "YET", "YOU", "ABED", "ABEL", "ABET", "ABLE", "ABUT", "ACHE",
"ACID", "ACME", "ACRE", "ACTA", "ACTS", "ADAM", "ADDS", "ADEN", "AFAR",
"AFRO", "AGEE", "AHEM", "AHOY", "AIDA", "AIDE", "AIDS", "AIRY", "AJAR",
"AKIN", "ALAN", "ALEC", "ALGA", "ALIA", "ALLY", "ALMA", "ALOE", "ALSO",
"ALTO", "ALUM", "ALVA", "AMEN", "AMES", "AMID", "AMMO", "AMOK", "AMOS",
"AMRA", "ANDY", "ANEW", "ANNA", "ANNE", "ANTE", "ANTI", "AQUA", "ARAB",
"ARCH", "AREA", "ARGO", "ARID", "ARMY", "ARTS", "ARTY", "ASIA", "ASKS",
"ATOM", "AUNT", "AURA", "AUTO", "AVER", "AVID", "AVIS", "AVON", "AVOW",
"AWAY", "AWRY", "BABE", "BABY", "BACH", "BACK", "BADE", "BAIL", "BAIT",
"BAKE", "BALD", "BALE", "BALI", "BALK", "BALL", "BALM", "BAND", "BANE",
"BANG", "BANK", "BARB", "BARD", "BARE", "BARK", "BARN", "BARR", "BASE",
"BASH", "BASK", "BASS", "BATE", "BATH", "BAWD", "BAWL", "BEAD", "BEAK",
"BEAM", "BEAN", "BEAR", "BEAT", "BEAU", "BECK", "BEEF", "BEEN", "BEER",
"BEET", "BELA", "BELL", "BELT", "BEND", "BENT", "BERG", "BERN", "BERT",
"BESS", "BEST", "BETA", "BETH", "BHOY", "BIAS", "BIDE", "BIEN", "BILE",
"BILK", "BILL", "BIND", "BING", "BIRD", "BITE", "BITS", "BLAB", "BLAT",
"BLED", "BLEW", "BLOB", "BLOC", "BLOT", "BLOW", "BLUE", "BLUM", "BLUR",
"BOAR", "BOAT", "BOCA", "BOCK", "BODE", "BODY", "BOGY", "BOHR", "BOIL",
"BOLD", "BOLO", "BOLT", "BOMB", "BONA", "BOND", "BONE", "BONG", "BONN",
"BONY", "BOOK", "BOOM", "BOON", "BOOT", "BORE", "BORG", "BORN", "BOSE",
"BOSS", "BOTH", "BOUT", "BOWL", "BOYD", "BRAD", "BRAE", "BRAG", "BRAN",
"BRAY", "BRED", "BREW", "BRIG", "BRIM", "BROW", "BUCK", "BUDD", "BUFF",
"BULB", "BULK", "BULL", "BUNK", "BUNT", "BUOY", "BURG", "BURL", "BURN",
"BURR", "BURT", "BURY", "BUSH", "BUSS", "BUST", "BUSY", "BYTE", "CADY",
"CAFE", "CAGE", "CAIN", "CAKE", "CALF", "CALL", "CALM", "CAME", "CANE",
"CANT", "CARD", "CARE", "CARL", "CARR", "CART", "CASE", "CASH", "CASK",
"CAST", "CAVE", "CEIL", "CELL", "CENT", "CERN", "CHAD", "CHAR", "CHAT",
"CHAW", "CHEF", "CHEN", "CHEW", "CHIC", "CHIN", "CHOU", "CHOW", "CHUB",
"CHUG", "CHUM", "CITE", "CITY", "CLAD", "CLAM", "CLAN", "CLAW", "CLAY",
"CLOD", "CLOG", "CLOT", "CLUB", "CLUE", "COAL", "COAT", "COCA", "**bleep**",
"COCO", "CODA", "CODE", "CODY", "COED", "COIL", "COIN", "COKE", "COLA",
"COLD", "COLT", "COMA", "COMB", "COME", "COOK", "COOL", "COON", "COOT",
"CORD", "CORE", "CORK", "CORN", "COST", "COVE", "COWL", "CRAB", "CRAG",
"CRAM", "CRAY", "CREW", "CRIB", "CROW", "CRUD", "CUBA", "CUBE", "CUFF",
"CULL", "CULT", "CUNY", "CURB", "CURD", "CURE", "CURL", "CURT", "CUTS",
"DADE", "DALE", "DAME", "DANA", "DANE", "DANG", "DANK", "DARE", "DARK",
"DARN", "DART", "DASH", "DATA", "DATE", "DAVE", "DAVY", "DAWN", "DAYS",
"DEAD", "DEAF", "DEAL", "DEAN", "DEAR", "DEBT", "DECK", "DEED", "DEEM",
"DEER", "DEFT", "DEFY", "DELL", "DENT", "DENY", "DESK", "DIAL", "DICE",
"DIED", "DIET", "DIME", "DINE", "DING", "DINT", "DIRE", "DIRT", "DISC",
"DISH", "DISK", "DIVE", "DOCK", "DOES", "DOLE", "DOLL", "DOLT", "DOME",
"DONE", "DOOM", "DOOR", "DORA", "DOSE", "DOTE", "DOUG", "DOUR", "DOVE",
"DOWN", "DRAB", "DRAG", "DRAM", "DRAW", "DREW", "DRUB", "DRUG", "DRUM",
"DUAL", "DUCK", "DUCT", "DUEL", "DUET", "DUKE", "DULL", "DUMB", "DUNE",
"DUNK", "DUSK", "DUST", "DUTY", "EACH", "EARL", "EARN", "EASE", "EAST",
"EASY", "EBEN", "ECHO", "EDDY", "EDEN", "EDGE", "EDGY", "EDIT", "EDNA",
"EGAN", "ELAN", "ELBA", "ELLA", "ELSE", "EMIL", "EMIT", "EMMA", "ENDS",
"ERIC", "EROS", "EVEN", "EVER", "EVIL", "EYED", "FACE", "FACT", "FADE",
"FAIL", "FAIN", "FAIR", "FAKE", "FALL", "FAME", "FANG", "FARM", "FAST",
"FATE", "FAWN", "FEAR", "FEAT", "FEED", "FEEL", "FEET", "FELL", "FELT",
"FEND", "FERN", "FEST", "FEUD", "FIEF", "FIGS", "FILE", "FILL", "FILM",
"FIND", "FINE", "FINK", "FIRE", "FIRM", "FISH", "FISK", "FIST", "FITS",
"FIVE", "FLAG", "FLAK", "FLAM", "FLAT", "FLAW", "FLEA", "FLED", "FLEW",
"FLIT", "FLOC", "FLOG", "FLOW", "FLUB", "FLUE", "FOAL", "FOAM", "FOGY",
"FOIL", "FOLD", "FOLK", "FOND", "FONT", "FOOD", "FOOL", "FOOT", "FORD",
"FORE", "FORK", "FORM", "FORT", "FOSS", "FOUL", "FOUR", "FOWL", "FRAU",
"FRAY", "FRED", "FREE", "FRET", "FREY", "FROG", "FROM", "FUEL", "FULL",
"FUME", "FUND", "FUNK", "FURY", "FUSE", "FUSS", "GAFF", "GAGE", "GAIL",
"GAIN", "GAIT", "GALA", "GALE", "GALL", "GALT", "GAME", "GANG", "GARB",
"GARY", "GASH", "GATE", "GAUL", "GAUR", "GAVE", "GAWK", "GEAR", "GELD",
"GENE", "GENT", "GERM", "GETS", "GIBE", "GIFT", "GILD", "GILL", "GILT",
"GINA", "GIRD", "GIRL", "GIST", "GIVE", "GLAD", "GLEE", "GLEN", "GLIB",
"GLOB", "GLOM", "GLOW", "GLUE", "GLUM", "GLUT", "GOAD", "GOAL", "GOAT",
"GOER", "GOES", "GOLD", "GOLF", "GONE", "GONG", "GOOD", "GOOF", "GORE",
"GORY", "GOSH", "GOUT", "GOWN", "GRAB", "GRAD", "GRAY", "GREG", "GREW",
"GREY", "GRID", "GRIM", "GRIN", "GRIT", "GROW", "GRUB", "GULF", "GULL",
"GUNK", "GURU", "GUSH", "GUST", "GWEN", "GWYN", "HAAG", "HAAS", "HACK",
"HAIL", "HAIR", "HALE", "HALF", "HALL", "HALO", "HALT", "HAND", "HANG",
"HANK", "HANS", "HARD", "HARK", "HARM", "HART", "HASH", "HAST", "HATE",
"HATH", "HAUL", "HAVE", "HAWK", "HAYS", "HEAD", "HEAL", "HEAR", "HEAT",
"HEBE", "HECK", "HEED", "HEEL", "HEFT", "HELD", "HELL", "HELM", "HERB",
"HERD", "HERE", "HERO", "HERS", "HESS", "HEWN", "HICK", "HIDE", "HIGH",
"HIKE", "HILL", "HILT", "HIND", "HINT", "HIRE", "HISS", "HIVE", "HOBO",
"HOCK", "HOFF", "HOLD", "HOLE", "HOLM", "HOLT", "HOME", "HONE", "HONK",
"HOOD", "HOOF", "HOOK", "HOOT", "HORN", "HOSE", "HOST", "HOUR", "HOVE",
"HOWE", "HOWL", "HOYT", "HUCK", "HUED", "HUFF", "HUGE", "HUGH", "HUGO",
"HULK", "HULL", "HUNK", "HUNT", "HURD", "HURL", "HURT", "HUSH", "HYDE",
"HYMN", "IBIS", "ICON", "IDEA", "IDLE", "IFFY", "INCA", "INCH", "INTO",
"IONS", "IOTA", "IOWA", "IRIS", "IRMA", "IRON", "ISLE", "ITCH", "ITEM",
"IVAN", "JACK", "JADE", "JAIL", "JAKE", "JANE", "JAVA", "JEAN", "JEFF",
"JERK", "JESS", "JEST", "JIBE", "JILL", "JILT", "JIVE", "JOAN", "JOBS",
"JOCK", "JOEL", "JOEY", "JOHN", "JOIN", "JOKE", "JOLT", "JOVE", "JUDD",
"JUDE", "JUDO", "JUDY", "JUJU", "JUKE", "JULY", "JUNE", "JUNK", "JUNO",
"JURY", "JUST", "JUTE", "KAHN", "KALE", "KANE", "KANT", "KARL", "KATE",
"KEEL", "KEEN", "KENO", "KENT", "KERN", "KERR", "KEYS", "KICK", "KILL",
"KIND", "KING", "KIRK", "KISS", "KITE", "KLAN", "KNEE", "KNEW", "KNIT",
"KNOB", "KNOT", "KNOW", "KOCH", "KONG", "KUDO", "KURD", "KURT", "KYLE",
"LACE", "LACK", "LACY", "LADY", "LAID", "LAIN", "LAIR", "LAKE", "LAMB",
"LAME", "LAND", "LANE", "LANG", "LARD", "LARK", "LASS", "LAST", "LATE",
"LAUD", "LAVA", "LAWN", "LAWS", "LAYS", "LEAD", "LEAF", "LEAK", "LEAN",
"LEAR", "LEEK", "LEER", "LEFT", "LEND", "LENS", "LENT", "LEON", "LESK",
"LESS", "LEST", "LETS", "LIAR", "LICE", "LICK", "LIED", "LIEN", "LIES",
"LIEU", "LIFE", "LIFT", "LIKE", "LILA", "LILT", "LILY", "LIMA", "LIMB",
"LIME", "LIND", "LINE", "LINK", "LINT", "LION", "LISA", "LIST", "LIVE",
"LOAD", "LOAF", "LOAM", "LOAN", "LOCK", "LOFT", "LOGE", "LOIS", "LOLA",
"LONE", "LONG", "LOOK", "LOON", "LOOT", "LORD", "LORE", "LOSE", "LOSS",
"LOST", "LOUD", "LOVE", "LOWE", "LUCK", "LUCY", "LUGE", "LUKE", "LULU",
"LUND", "LUNG", "LURA", "LURE", "LURK", "LUSH", "LUST", "LYLE", "LYNN",
"LYON", "LYRA", "MACE", "MADE", "MAGI", "MAID", "MAIL", "MAIN", "MAKE",
"MALE", "MALI", "MALL", "MALT", "MANA", "MANN", "MANY", "MARC", "MARE",
"MARK", "MARS", "MART", "MARY", "MASH", "MASK", "MASS", "MAST", "MATE",
"MATH", "MAUL", "MAYO", "MEAD", "MEAL", "MEAN", "MEAT", "MEEK", "MEET",
"MELD", "MELT", "MEMO", "MEND", "MENU", "MERT", "MESH", "MESS", "MICE",
"MIKE", "MILD", "MILE", "MILK", "MILL", "MILT", "MIMI", "MIND", "MINE",
"MINI", "MINK", "MINT", "MIRE", "MISS", "MIST", "MITE", "MITT", "MOAN",
"MOAT", "MOCK", "MODE", "MOLD", "MOLE", "MOLL", "MOLT", "MONA", "MONK",
"MONT", "MOOD", "MOON", "MOOR", "MOOT", "MORE", "MORN", "MORT", "MOSS",
"MOST", "MOTH", "MOVE", "MUCH", "MUCK", "MUDD", "MUFF", "MULE", "MULL",
"MURK", "MUSH", "MUST", "MUTE", "MUTT", "MYRA", "MYTH", "NAGY", "NAIL",
"NAIR", "NAME", "NARY", "NASH", "NAVE", "NAVY", "NEAL", "NEAR", "NEAT",
"NECK", "NEED", "NEIL", "NELL", "NEON", "NERO", "NESS", "NEST", "NEWS",
"NEWT", "NIBS", "NICE", "NICK", "NILE", "NINA", "NINE", "NOAH", "NODE",
"NOEL", "NOLL", "NONE", "NOOK", "NOON", "NORM", "NOSE", "NOTE", "NOUN",
"NOVA", "NUDE", "NULL", "NUMB", "OATH", "OBEY", "OBOE", "ODIN", "OHIO",
"OILY", "OINT", "OKAY", "OLAF", "OLDY", "OLGA", "OLIN", "OMAN", "OMEN",
"OMIT", "ONCE", "ONES", "ONLY", "ONTO", "ONUS", "ORAL", "ORGY", "OSLO",
"OTIS", "OTTO", "OUCH", "OUST", "OUTS", "OVAL", "OVEN", "OVER", "OWLY",
"OWNS", "QUAD", "QUIT", "QUOD", "RACE", "RACK", "RACY", "RAFT", "RAGE",
"RAID", "RAIL", "RAIN", "RAKE", "RANK", "RANT", "RARE", "RASH", "RATE",
"RAVE", "RAYS", "READ", "REAL", "REAM", "REAR", "RECK", "REED", "REEF",
"REEK", "REEL", "REID", "REIN", "RENA", "REND", "RENT", "REST", "RICE",
"RICH", "RICK", "RIDE", "RIFT", "RILL", "RIME", "RING", "RINK", "RISE",
"RISK", "RITE", "ROAD", "ROAM", "ROAR", "ROBE", "ROCK", "RODE", "ROIL",
"ROLL", "ROME", "ROOD", "ROOF", "ROOK", "ROOM", "ROOT", "ROSA", "ROSE",
"ROSS", "ROSY", "ROTH", "ROUT", "ROVE", "ROWE", "ROWS", "RUBE", "RUBY",
"RUDE", "RUDY", "RUIN", "RULE", "RUNG", "RUNS", "RUNT", "RUSE", "RUSH",
"RUSK", "RUSS", "RUST", "RUTH", "SACK", "SAFE", "SAGE", "SAID", "SAIL",
"SALE", "SALK", "SALT", "SAME", "SAND", "SANE", "SANG", "SANK", "SARA",
"SAUL", "SAVE", "SAYS", "SCAN", "SCAR", "SCAT", "SCOT", "SEAL", "SEAM",
"SEAR", "SEAT", "SEED", "SEEK", "SEEM", "SEEN", "SEES", "SELF", "SELL",
"SEND", "SENT", "SETS", "SEWN", "SHAG", "SHAM", "SHAW", "SHAY", "SHED",
"SHIM", "SHIN", "SHOD", "SHOE", "SHOT", "SHOW", "SHUN", "SHUT", "SICK",
"SIDE", "SIFT", "SIGH", "SIGN", "SILK", "SILL", "SILO", "SILT", "SINE",
"SING", "SINK", "SIRE", "SITE", "SITS", "SITU", "SKAT", "SKEW", "SKID",
"SKIM", "SKIN", "SKIT", "SLAB", "SLAM", "SLAT", "SLAY", "SLED", "SLEW",
"SLID", "SLIM", "SLIT", "SLOB", "SLOG", "SLOT", "SLOW", "SLUG", "SLUM",
"SLUR", "SMOG", "SMUG", "SNAG", "SNOB", "SNOW", "SNUB", "SNUG", "SOAK",
"SOAR", "SOCK", "SODA", "SOFA", "SOFT", "SOIL", "SOLD", "SOME", "SONG",
"SOON", "SOOT", "SORE", "SORT", "SOUL", "SOUR", "SOWN", "STAB", "STAG",
"STAN", "STAR", "STAY", "STEM", "STEW", "STIR", "STOW", "STUB", "STUN",
"SUCH", "SUDS", "SUIT", "SULK", "SUMS", "SUNG", "SUNK", "SURE", "SURF",
"SWAB", "SWAG", "SWAM", "SWAN", "SWAT", "SWAY", "SWIM", "SWUM", "TACK",
"TACT", "TAIL", "TAKE", "TALE", "TALK", "TALL", "TANK", "TASK", "TATE",
"TAUT", "TEAL", "TEAM", "TEAR", "TECH", "TEEM", "TEEN", "TEET", "TELL",
"TEND", "TENT", "TERM", "TERN", "TESS", "TEST", "THAN", "THAT", "THEE",
"THEM", "THEN", "THEY", "THIN", "THIS", "THUD", "THUG", "TICK", "TIDE",
"TIDY", "TIED", "TIER", "TILE", "TILL", "TILT", "TIME", "TINA", "TINE",
"TINT", "TINY", "TIRE", "TOAD", "TOGO", "TOIL", "TOLD", "TOLL", "TONE",
"TONG", "TONY", "TOOK", "TOOL", "TOOT", "TORE", "TORN", "TOTE", "TOUR",
"TOUT", "TOWN", "TRAG", "TRAM", "TRAY", "TREE", "TREK", "TRIG", "TRIM",
"TRIO", "TROD", "TROT", "TROY", "TRUE", "TUBA", "TUBE", "TUCK", "TUFT",
"TUNA", "TUNE", "TUNG", "TURF", "TURN", "TUSK", "TWIG", "TWIN", "TWIT",
"ULAN", "UNIT", "URGE", "USED", "USER", "USES", "UTAH", "VAIL", "VAIN",
"VALE", "VARY", "VASE", "VAST", "VEAL", "VEDA", "VEIL", "VEIN", "VEND",
"VENT", "VERB", "VERY", "VETO", "VICE", "VIEW", "VINE", "VISE", "VOID",
"VOLT", "VOTE", "WACK", "WADE", "WAGE", "WAIL", "WAIT", "WAKE", "WALE",
"WALK", "WALL", "WALT", "WAND", "WANE", "WANG", "WANT", "WARD", "WARM",
"WARN", "WART", "WASH", "WAST", "WATS", "WATT", "WAVE", "WAVY", "WAYS",
"WEAK", "WEAL", "WEAN", "WEAR", "WEED", "WEEK", "WEIR", "WELD", "WELL",
"WELT", "WENT", "WERE", "WERT", "WEST", "WHAM", "WHAT", "WHEE", "WHEN",
"WHET", "WHOA", "WHOM", "WICK", "WIFE", "WILD", "WILL", "WIND", "WINE",
"WING", "WINK", "WINO", "WIRE", "WISE", "WISH", "WITH", "WOLF", "WONT",
"WOOD", "WOOL", "WORD", "WORE", "WORK", "WORM", "WORN", "WOVE", "WRIT",
"WYNN", "YALE", "YANG", "YANK", "YARD", "YARN", "YAWL", "YAWN", "YEAH",
"YEAR", "YELL", "YOGA", "YOKE"
};
/* Encode 8 bytes in 'c' as a string of English words.
* Returns a pointer to a static buffer
*/
char *
btoe(engout,c)
char *c, *engout;
{
char cp[9]; /* add in room for the parity 2 bits*/
int p,i ;
engout[0] = '\0';
memcpy(cp, c,8);
/* compute parity */
for(p = 0,i = 0; i < 64;i += 2)
p += extract(cp,i,2);
cp[8] = (char)p << 6;
strncat(engout,&Wp[extract(cp, 0,11)][0],4);
strcat(engout," ");
strncat(engout,&Wp[extract(cp,11,11)][0],4);
strcat(engout," ");
strncat(engout,&Wp[extract(cp,22,11)][0],4);
strcat(engout," ");
strncat(engout,&Wp[extract(cp,33,11)][0],4);
strcat(engout," ");
strncat(engout,&Wp[extract(cp,44,11)][0],4);
strcat(engout," ");
strncat(engout,&Wp[extract(cp,55,11)][0],4);
/* printf("engout is %s\n\r",engout);*/
return(engout);
}
/* convert English to binary
* returns 1 OK - all good words and parity is OK
* 0 word not in data base
* -1 badly formed in put ie > 4 char word
* -2 words OK but parity is wrong
*/
int
etob(out, e)
char *out;
char *e;
{
char *word;
int i, p, v,l, low,high;
char b[9];
char input[36];
if(e == NULL)
return -1;
strncpy(input,e,sizeof(input));
memset(b, 0, sizeof(b));
memset(out, 0, 8);
for(i=0,p=0;i<6;i++,p+=11){
if((word = strtok(i == 0 ? input : NULL," ")) == NULL)
return -1;
l = strlen(word);
if(l > 4 || l < 1){
return -1;
} else if(l < 4){
low = 0;
high = 570;
} else {
low = 571;
high = 2047;
}
standard(word);
if( (v = wsrch(word,low,high)) < 0 )
return 0;
insert(b,v,p,11);
}
/* now check the parity of what we got */
for(p = 0, i = 0; i < 64; i +=2)
p += extract(b, i, 2);
if( (p & 3) != extract(b, 64,2) )
return -2;
memcpy(out,b,8);
return 1;
}
/* Display 8 bytes as a series of 16-bit hex digits */
char *
put16(out,s)
char *out;
char *s;
{
sprintf(out,"%02X:%02X:%02X:%02X:%02X:%02X:%02X:%02X:%02X:%02X:%02X:%02X:%02X:%02X:%02X:%02X",
s[0] & 0xff,s[1] & 0xff,s[2] & 0xff,
s[3] & 0xff,s[4] & 0xff,s[5] & 0xff,
s[6] & 0xff,s[7] & 0xff,
s[8] & 0xff,s[9] & 0xff,s[10] & 0xff,
s[11] & 0xff,s[12] & 0xff,s[13] & 0xff,
s[14] & 0xff,s[15] & 0xff
);
return out;
}
#ifdef notdef
/* Encode 8 bytes in 'cp' as stream of ascii letters.
* Provided as a possible alternative to btoe()
*/
char *
btoc(cp)
char *cp;
{
int i;
static char out[31];
/* code out put by characters 6 bits each added to 0x21 (!)*/
for(i=0;i <= 10;i++){
/* last one is only 4 bits not 6*/
out[i] = '!'+ extract(cp,6*i,i >= 10 ? 4:6);
}
out[i] = '\0';
return(out);
}
#endif
/* Internal subroutines for word encoding/decoding */
/* Dictionary binary search */
static int
wsrch(w,low,high)
char *w;
int low, high;
{
int i,j;
for(;;){
i = (low + high)/2;
if((j = strncmp(w,Wp[i],4)) == 0)
return i; /* Found it */
if(high == low+1){
/* Avoid effects of integer truncation in /2 */
if(strncmp(w,Wp[high],4) == 0)
return high;
else
return -1;
}
if(low >= high)
return -1;
/* I don't *think* this can happen...*/
if(j < 0)
high = i; /* Search lower half */
else
low = i; /* Search upper half */
}
}
static void
insert(s, x, start, length)
char *s;
int x;
int start, length;
{
unsigned char cl;
unsigned char cc;
unsigned char cr;
unsigned long y;
int shift;
assert(length <= 11);
assert(start >= 0);
assert(length >= 0);
assert(start +length <= 66);
shift = ((8 -(( start + length) % 8))%8);
y = (long) x << shift;
cl = (y >> 16) & 0xff;
cc = (y >> 😎 & 0xff;
cr = y & 0xff;
if(shift + length > 16){
s[start /8] |= cl;
s[start/8 +1] |= cc;
s[start/8 +2] |= cr;
} else if(shift +length > 8){
s[start/8] |= cc;
s[start/8 + 1] |= cr;
} else {
s[start/8] |= cr;
}
}
static void
standard(word)
register char *word;
{
while(*word){
if(!isascii(*word))
break;
if(islower(*word))
*word = toupper(*word);
if(*word == '1')
*word = 'L';
if(*word == '0')
*word = 'O';
if(*word == '5')
*word = 'S';
word++;
}
}
/* Extract 'length' bits from the char array 's'
starting with bit 'start' */
static unsigned long
extract(s, start, length)
char *s;
int start, length;
{
unsigned char cl;
unsigned char cc;
unsigned char cr;
unsigned long x;
assert(length <= 11);
assert(start >= 0);
assert(length >= 0);
assert(start +length <= 66);
cl = s[start/8];
cc = s[start/8 +1];
cr = s[start/8 +2];
x = ((long)(cl<<8 | cc) <<8 | cr) ;
x = x >> (24 - (length + (start %8)));
x =( x & (0xffff >> (16-length) ) );
return(x);
}
/* convert.c -- Wrapper to S/Key binary-to-English routines.
Daniel L. McDonald -- U. S. Naval Research Laboratory. */
#include <string.h>
/* eng2key() assumes words must be separated by spaces only.
eng2key() returns
1 if succeeded
0 if word not in dictionary
-1 if badly formed string
-2 if words are okay but parity is wrong.
(see etob() in S/Key)
*/
int eng2key(keyout,eng)
char *keyout,*eng;
{
int rc=0,state=1;
char *eng2;
/* Find pointer to word 7. */
for (eng2 = eng; rc<7 && (*(++eng2) != '\0'); )
if (*eng2 != ' ')
{
rc += state;
state = 0;
}
else state=1;
if ( (rc = etob(keyout,eng)) != 1)
return rc;
rc = etob(keyout+8,eng2);
return rc;
}
/* key2eng() assumes string referenced by
engout has at least 60 characters
(4*12 + 11 spaces + '\0') of space.
key2eng() returns pointer to engout.
*/
char *key2eng(engout,key)
char *engout,*key;
{
btoe(engout,key);
strcat(engout," ");
btoe(engout+strlen(engout),key+8);
return engout;
}
void removeChar(char *str, char garbage) {
char *src, *dst;
for (src=dst = str; *src != '\0'; src++) {
*dst = *src;
if (*dst != garbage) dst++;
}
*dst = '\0';
}
int main (int argc, char** argv)
{
char* output = calloc(60,sizeof(char));
char* output2 = calloc(60,sizeof(char));
char* input = calloc(16,sizeof(char));
int returncode = 0;
/*printf("Input: %s\n",argv[1]);*/
if (argv[1][2] == ':')
{
removeChar(argv[1],':');
/*printf("Input: %s\n",argv[1]);*/
const char* pos = argv[1];
/* WARNING: no sanitization or error-checking whatsoever */
for (size_t count = 0; count < 16; count++) {
sscanf(pos, "%2hhx", (unsigned char *) &input[count]);
pos += 2;
}
/*printf("0x");
for(size_t count = 0; count < 16; count++)
printf("%02x", input[count]);
printf("\n");*/
key2eng(output,input);
printf("Output: %s\n",output);
}
else
{
returncode = eng2key(output,argv[1]);
output2 = put16(output2,output);
printf("Return Code: %i\n", returncode);
printf("Output: %s\n",output2);
/*printf("Output org: ");
for (int i = 0; i < 16; i ++) {
printf(" %02x", (unsigned)output[i]);
}
putchar('\n');
key2eng(output2,output);
printf("Output: %s\n",output2);
printf("sizeof(char): %li\n",sizeof(char));
printf("sizeof(int): %li\n",sizeof(int));*/
}
return 0;
}Just compile it:
gcc rfc_1751.c -o rfc_1751.exe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @EY ,
If Check Point provides such a tool, how would you use it? What do you expect to supply as input and what do you expect to see as output (something else besides fingerprint)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I dunno how to get this into the Toolbox Scripts board, but I cobbled this together in Python. It's not glorious, so someone is free to clean it as you wish.
#!/usr/bin/python3
import sys, os
import binascii
from Crypto.Util import RFC1751
def main(argv=None):
if argv is None:
argv = sys.argv
if not (len(argv)):
print("Fingerprint hex string missing\n")
print("Usage: {} <string>\n".format(__file__))
print("String may be colon-separated hex (00:01:aa:bb...) or without colons (0001abcd...)\n")
exit(1)
fingerprint_arg=argv[0]
fingerprint_str=fingerprint_arg.replace(':','')
if (len(fingerprint_str) == 40):
fingerprint_hex=fingerprint_str[:32]
elif (len(fingerprint_str) == 32):
fingerprint_hex=fingerprint_str
else:
print("Usage: {} <string>\n".format(__file__))
exit(1)
fingerprint_txt=RFC1751.key_to_english(binascii.unhexlify(fingerprint_hex[:32]))
print("\nASCII fingerprint string:\n")
print(fingerprint_txt)
print("\n")
if __name__ == "__main__":
main(sys.argv[1:])
$ script.py AB:3A:04:87:F0:83:07:DC:B6:22:45:0C:CC:8E:5D:B9:3F:FE:C3:4C
ASCII fingerprint string:
LAUD RISE KID SOAK OUR TORE MAIN EVA US HOBO SWAG SING
$ script.py 4607BC6AD16849924F612CD2D6EB4358
ASCII fingerprint string:
WOW SPA HIM JOKE FOOL ORGY AVER BUS POP LIAR LUND LEEK
If you are using the Windows certificate details view, the Thumbprint value is 40-bytes, long not 32, so that has to be truncated (which the script does). Feel free to paste the whole 40-byte string as the argument. If you are using openssl x509 -fingerprint, then use the -sha1 argument to get the SHA1 hash (may be default, but a newer openssl may change that some day).
So far, this seems to match certificates and fingerprints that I've tested. No guarantee this is perfect, tho.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@_Val_ flagging for your review
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Duane_Toler @PhoneBoy Yes, ToolBox material. Duane, I will reach to you offline for the process.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just tested and it works! Even with more than two fingerprints...
But be careful not to have any blanks around the ":", at the beginning or the end.
[HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\CheckPoint\accepted_cn\vpn.acme.com]
"--Fingerprint--"="XXXX XXX XXX XXX XXXX XXX XXXX XXXX XXX XXXX XXX XXXX:YYYY YYY YYY YYY YYYY YYY YYYY YYYY YYY YYYY YYY YYYY"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Attention no space in between the colon and the 2nd fingerprint !!!
"--Fingerprint--"="XXXX XXXX XXXX XXXX XXXX XXXX:YYYY YYYY YYYY YYYY YYYY YYYY"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
By coincidence, I had to do this for a customer today. I'm guessing "things" have changed with the Endpoint VPN client over time, as sk66263 is a bit erroneous. I sent a feedback on the SK article with the changes I observed.
1) The name of the registry key is the name of VPN gateway + the literal text "VPN Certificate" (e.g.: "office-fw VPN Certificate").
2) The fingerprint value is indeed that of the internal_ca (the issuer certificate), not the gateway IPsec VPN certificate (I believe this is different for SAML, however).
If you want to be fancy and clever, using that Python script I attached above, you can get it all in one shot. (obviously use your gateway's IP address)
./rfc1751.py $(openssl s_client -connect 192.0.2.1:443 -showcerts </dev/null 2>/dev/null |sed -n -e '/0 s:/,/END CERT/p'|openssl x509 -noout -fingerprint -sha1|awk -F= '{print $2}')
The SK article is correct, however, on the location of the registry key, so follow that as described. I verified the registry key info on my PC after a manual site configuration and connection, as well.
Hope this helps others.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 7 | |
| 6 | |
| 5 | |
| 4 | |
| 4 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Tue 05 Nov 2024 @ 10:00 AM (CET)
EMEA CM LIVE: 30 Years for the CISSP certification - why it is still on topTue 05 Nov 2024 @ 05:00 PM (CET)
Americas CM LIVE: - 30 Years for the CISSP certification - why it is still on topThu 07 Nov 2024 @ 05:00 PM (CET)
What's New in CloudGuard - Priorities, Trends and Roadmap InnovationsTue 05 Nov 2024 @ 10:00 AM (CET)
EMEA CM LIVE: 30 Years for the CISSP certification - why it is still on topTue 05 Nov 2024 @ 05:00 PM (CET)
Americas CM LIVE: - 30 Years for the CISSP certification - why it is still on topTue 12 Nov 2024 @ 03:00 PM (AEDT)
Topic No Suits, No Ties: From Calm to Chaos: the sudden impact of ransomware and its effects (APAC)Wed 20 Nov 2024 @ 05:00 PM (CET)
Under the Hood: DO NOT Renew your WAF without watching THIS!!Tue 19 Nov 2024 @ 12:00 PM (MST)
Salt Lake City: Infinity External Risk Management and Harmony SaaSWed 20 Nov 2024 @ 02:00 PM (MST)
Denver South: Infinity External Risk Management and Harmony SaaSAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter