The Network tab in the SandBlast Mobile Dashboard provides a granular view of network events and their context.
The following network events are being reported:
| Event Type | Description |
|---|
| SSL Stripping | A third-party intercepted the traffic and downgraded it from HTTPS to HTTP |
| SSL Interception (Basic) | A third-party intercepted the traffic and posed as the original requester to the target server and as the target destination to the original requester, while controlling the responses back to the requester. |
| SSL Interception (Advanced) | Similar to basic SSL Interception, however, in this case the perpetrator responses were encrypted with an SSL certificate that was issued by a certificate authority that is listed as trusted on the victim’s device. |
| Captive Portal Redirection | The traffic from the device is redirected to the network’s portal for registration to the network. This is common with public networks, especially free networks, such as those in airports, hotels, and cafes. |
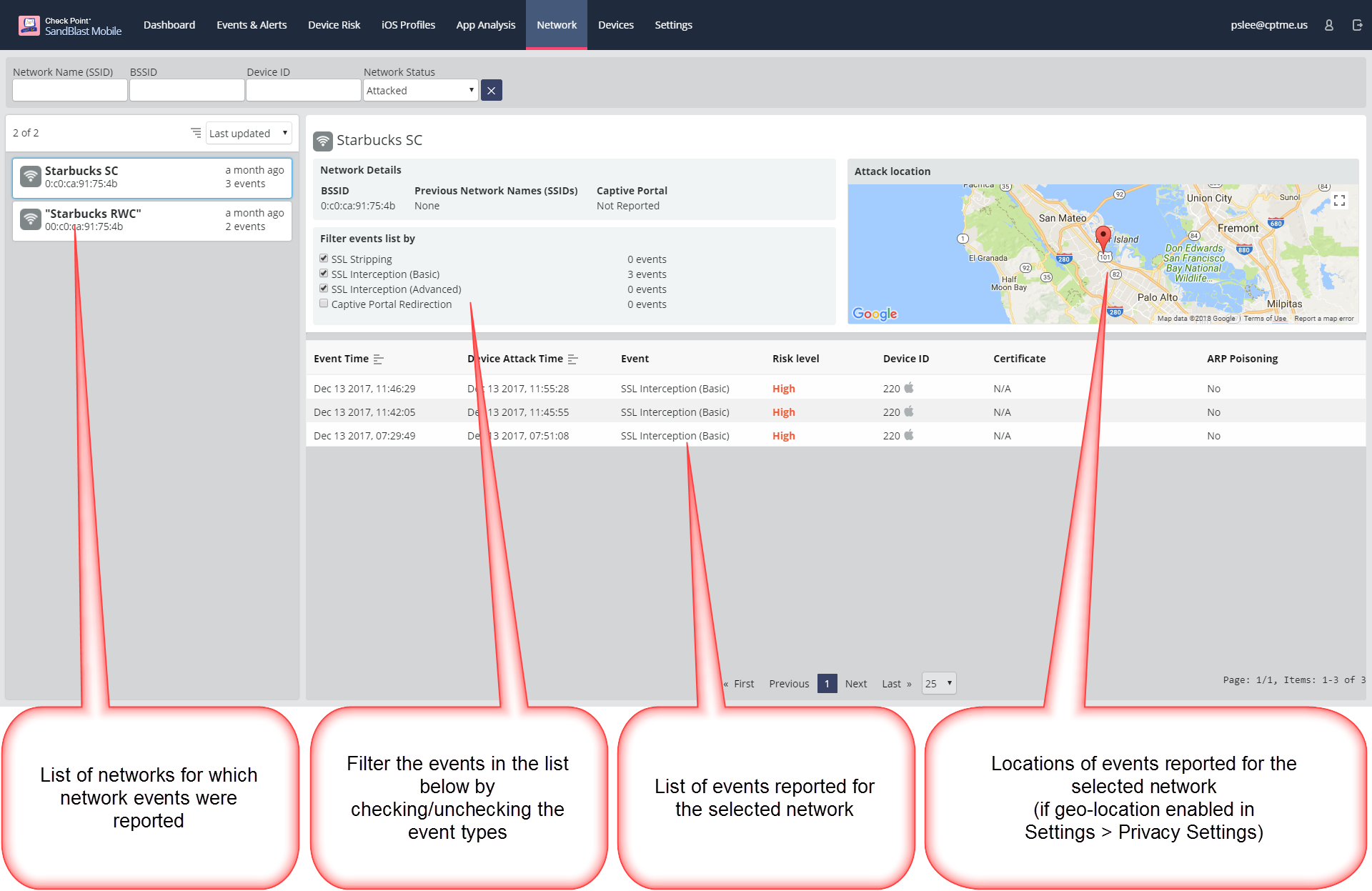
List of Networks (left pane) - The networks are listed on the left pane and can be filtered by Network Name (SSID), BSSID, or by a device ID. The list can be sorted by name or by last updated.
Network Details (right pane) - The right pane displays the details of the selected network on the left pane.
| BSSID | the network’s unique identifier |
SSID | the network’s readable name. Not unique. Can be changed over time. |
A list of the events reported for the network, each event includes the following data: | - Event Time - Event Type - Event Risk - Device ID (of the device for which the event was reported) - links to the device risk page - SSL certificate received (not applicable for SSL Stripping) - ARP poisoning used during the attack (Yes/No) - Location of the reported events on a map (can be turned ON/OFF in Settings > Privacy Settings) |
Important feature notes:
- Networks are listed on the left-hand pane by their readable SSID (network name).
However, networks are identified by their unique identifier, the BSSID.
Therefore, several networks with the same readable name can appear in the list. - Only networks that have experienced an attack are listed in the left-hand pane.
- Event time in the network tab is the actual time at which the event was detected on the device.
This is different from the time reported in Events & Alerts which is the time at which the event report was received by the dashboard. - Location collection is turned ON by default. It can be turned off in the privacy settings of the dashboard.
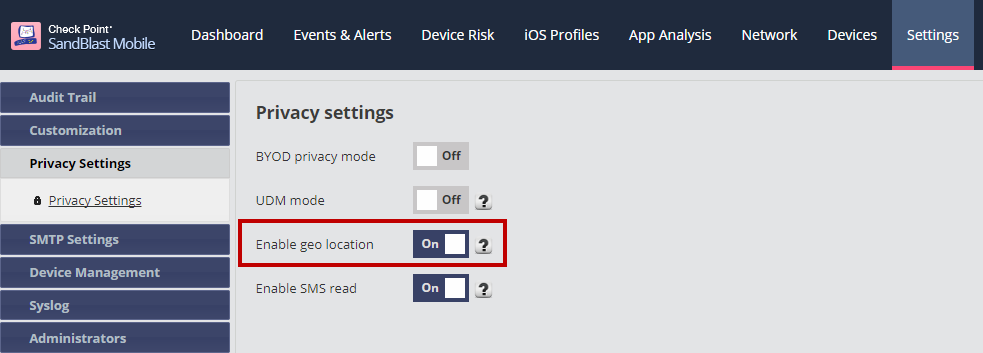
- User needs to allow location permission for the app on their device in order for it to be displayed in the dashboard.
- For Android devices this permission is requested in advance of installing/updating the mobile app, regardless of the setting in the dashboard, and granting it is required to allow that installation/upgrade.
- For iOS devices the permission is requested on-the-fly, at the first time the application attempts to access the device location.
Therefore, granting the permission is not a requirement for installing/upgrading the client, and if the collection is turned off in the dashboard, permissions will not be requested.
- New event type: Captive portal redirection
- Captive portals are a common feature of public networks, such as the networks common in hotels, airports, restaurants, public transportation and their likes. In order to gain access to the network, user are required to go through the portal and either provide some access credentials are simply accept the usage terms.
- Captive portal redirections are de-facto a form of MiTM attack and therefore can be identified and alerted on as such.
- SandBlast Mobile’s advanced detection algorithm distinguishes between captive portal redirections from other incidents of MiTM and provides dedicated indication of them.
This way, administrators have the full picture of the traffic through the networks without the hustle of the false alerts. - Please note that captive portal redirections are associated with no risk and are not reported to the Events and Alerts tab, only to the new network events dedicated tab.
Network tab introduced in v2.52 with ARP Poisoning parameter added in v2.59.




