- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- prefer security /prefer connectivity
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
prefer security /prefer connectivity
hello support,
may i know the scenario and what kind of scenario we can use prefer security ?
and what kind of scenario we can use prefer connectivity ? what are the benefits if we use both of the parameter?
17 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
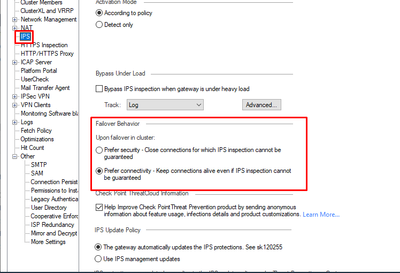
I assume you are referring to IPS blade setting on the gateway...there is an option there which is by default to prefer connectivity upon cluster failover even if IPS protections cant be guaranteed OR prefer security, which would close connections if IPS protections cant be guaranteed. Now, if you are speaking generally, it really depends who you ask. Of course, in todays world, more than ever before, security is way too important to overlook, but then if you think of connectivity, its literally something most companies require constantly. So, all in all, both are super important, but again, opinions might be split on this one.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hello rock,
thanks for the update ,
correct me if i am wrong
if i select the prefer connectivity , during the failover it simply switch the connection to standby device it ensure there is no connectivity issue failover
if i select the prefer security , during the failover it simply drop the current connection it will not ensure the connectivity right
above i mentioned is correct rock ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I attached the screenshot for your reference, hope its helpful.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You sort of got it : - ). So for prefer connectivity, yes, thats correct, IF your cluster is fully functional, then when failover happens, it will work fine if that option is selected. Now, IF prefer security is selected, does not mean current connections will close, ONLY ones for which IPS signatures can not be applied to/guaranteed. Personally, I would leave it to "prefer connectivity", which is default, as lets be honest, you do NOT want people "screaming" at you because their connections are failing : - )
By the way, sk @Chris_Atkinson provided also explains that. I would listen to him, he is EXCELLENT, very smart guy!
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One interesting side effect of "prefer connectivity" is that while the connection will be continued upon ClusterXL failover, it cannot be inspected by streaming (either active or passive) anymore. As a result the connection will be offloaded into the SXL/Accelerated Path on the newly-active member.
This looks very strange when you are watching a high-speed transfer that is subject to streaming inspection and a failover occurs; the speed of the transfer doubles or triples! Interestingly if you fail back over to the original member streaming inspection resumes (assuming the member has not been rebooted or otherwise cleared its state table) and the transfer speed drops back to what it was before. Was definitely a WTF moment when I first saw this effect, as causing a failover would massively speed up big transfers!
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
O wow, thanks for that Tim, thats super interesting 👍
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hello
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sk60160 provides some additional insight further to that provided by Andy.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What to use if you are running a 64k Scalable Plattform which is only a "Single" / "Standard" Gateway Object in SmartConsole and you can not select the options? Probably same for Maestro.
However 64k/Maestro may have failovers in the same "Chassis" or from one chassis to another. What will apply?
Prefer connectifity or prefer security?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The default on SP/Maestro is prefer connectivity. At least in R80.30SP the command was asg_ips_failover_behavior {connectivity | security} and you could check the current state with command g_fw ctl get int fwha_ips_reject_on_failover, 0 is prefer connectivity, 1 is prefer security.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks,
I can confirm "connectivity" at least for 64k and R80.20SP Jumbo HFA Take 331
g_fw ctl get int fwha_ips_reject_on_failover
-*- 10 blades: 1_01 1_02 1_03 1_04 1_05 2_01 2_02 2_03 2_04 2_05 -*-
fwha_ips_reject_on_failover = 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hello
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
can i get an update from above questions?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I cant give you answers to those, as I never tested option to prefer security, as default one is what everyone leaves it to. You would need to try it out and see the behavior.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hello rock,
thanks for the update .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi all,
if any one know the behavior and above questions answer .kindly let me know .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The kinds of failures that are being discussed here are related to the clustering technology known as ClusterXL.
Many, many things outside of the control of the Check Point configuration can cause ClusterXL to “fail over” to another device.
It obviously has an impact on the IPS service, which requires the same gateway to process the connection (thus why the Prefer Connectivity/Security option exists).
3 minutes and 11 seconds doesn’t sound unreasonable if their test of “IPS service failure” was a reboot of the primary gateway.
There are other reasons a failover can occur that don’t involve a reboot (for example, disabling/unplugging a cable on a NIC, or something else that prevents the gateways from seeing each other).
I would want to know precisely how they are testing this.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 13 | |
| 8 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter