- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- VPNs to different sites via different ISPs
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
VPNs to different sites via different ISPs
Hello community!
We're trying to implement the following scenario.
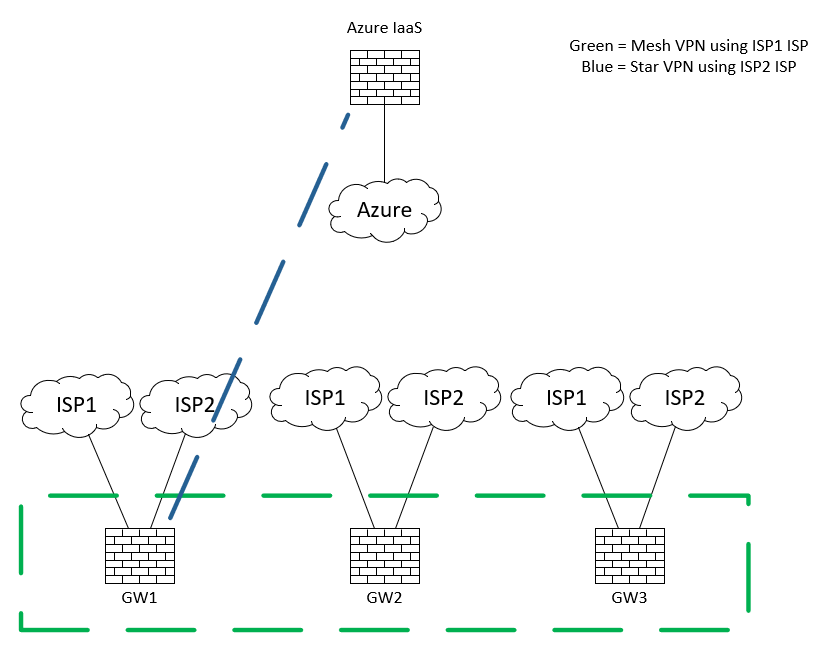
We have several on-premises sites, each with 2 ISPs. We also have a site in Azure (with 1 external interface).
We would like the local sites to have a mesh VPN community which prefers ISP1, and falls back on ISP2. ie, if GatewayX's ISP1 goes down, then the other Gateways bring up a VPN tunnel with GatewayX using ISP2.
We then want that the on-premises sites to have a star community with Azure as the hub, this time preferring ISP2, falling back on ISP1.
I'm trying to mess with combinations of 'load sharing' or 'calculate IP based on network topology' and static routes, but have not had success yet. (I think 'calculate IP based on network topology' does not do exactly what it seems to say on the tin)
All gateways are centrally managed by the same Management.
Did anyone ever configure such a setup?
Thanks!
Steven.
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you change the Outgoing Route Selection at all?
It would be helpful if you could explain (along with version/JHF level) the exact combinations you tried with the precise results you got.
Screenshots (with sensitive data masked) might also be helpful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for the reply.
Version is R80.40, Take 102 for management and gateways.
IPs are currently 'fake' as I'm doing tests in a lab which simulates the end result as much as possible.
ISP1 = 213.165.x.x
ISP2 = 195.158.x.x (this one is behind an interlink, so sometimes you will see 192.168.x.x)
Azure ISP: 13.13.x.x
Routing Config:
GW1 (on prem)
- ISP Redundancy in HA
- Primary: ISP 2 (195.158)
- Secondary: ISP 1 (213.165)
- Apply settings to VPN - DISABLED
- Static routes to GW4 - ISP 1:
- Via ISP 1 – preference 3
- Via ISP 2 – preference 6
- Static routes to GW4 - ISP 2:
- Via ISP 2 – preference 3
- Via ISP 1 – preference 6
GW4 (on prem)
- ISP Redundancy in HA
- Primary: ISP 2 (195.158)
- Secondary: ISP 1 (213.165)
- Apply settings to VPN - DISABLED
- Static routes to GW 1 - ISP 1:
- Via ISP 1 – preference 3
- Via ISP 2 – preference 6
- Static routes to GW1 - ISP 2:
- Via ISP 2 – preference 3
- Via ISP 1 – preference 6
CP-Cluster (Azure)
- Not actually a Cluster.
- 1 ISP (13.13.x.x)
- No special static routes
VPN config:
GW1:
- IP selection by remote peer: Use probing – HA – ISP 1 primary
- Outgoing route selection: Route based probing
- Source IP address setting: Automatic
GW4
- IP selection by remote peer: Use probing – HA – ISP 1 primary
- Outgoing route selection: Route based probing
- Source IP address setting: Automatic
CP-Cluster
- selection by remote peer: Selected from topology table: 13.13.x.x
- Outgoing route selection: OS routing table
- Setup: use outgoing traffic configuration
- Source IP address setting: Automatic
Results:
For GW1-to-GW4 and GW4-to-GW1, the tunnel is up and both ends are using ISP1.
Then for CPGW01-to-CPCluster, the next-hop IP is 192.168.x.x, ie ISP2 – cool this is what we want.
But for CPCluster-to-CPGW1, the Peer IP is ISP1. This is confirmed from TCPdumps (taken from GW1. GW1 is talking to 13.13.x.x via 192.168.x.x - ISP2, but CPCluster is talking back to 213.165.x.x - ISP1).
(I will try to post screenshots, but for some reason it's not working yet...)
So the VPN is coming up asymmetrically. This asymmetry is causing issues elsewhere.
We need to somehow inform CPCluster that the peer address should be 195.158.x.x, then fall back to 213.165.x.x if need be.
Should I still go through the different steps I took during testing?
Steven.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When you say inform the cluster of one IP and then fall back to a different one, Im not sure I understand that, sorry. It will always recognize the same IP and only fall back to another one if there is ISP redundancy configured and primary link goes down. What does link selection page look like, can you share that?
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you.
I'm attaching the link selection page for GW1, and also attaching a simplified version of the topology.
We want 1 VPN between GW4 and GW1 via ISP1, and 1 VPN between CPCluster and GW1 via ISP2.
But if either ISPs fails, then the respective VPN is brought up with the other ISP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So the way you have it now, IP 213.x.x.x will ALWAYS be primary link that VPN will use and should it fail, it would go to secondary link listed. You can also set this up via ISP redundancy tab in gateway properties with option "apply settings to VPN".
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Indeed. Having the primary link configured is probably not something that I want.
But when I remove that, what's to tell GW4 to prefer connecting to 213.x.x.x and CPCluster to prefer 195.x.x.x?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok ok, I totally get what you are asking now, sorry for the confusion. Short answer is "I have no clue", but, it would be nice to find out if this is even possible. I will let @PhoneBoy take a "stab" at it, as he is CP encyclopedia, but in the meantime, let me see if there are some settings in trac_client_1.ttm file on the gateway or guidbedit that may help.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I very much doubt this complexity would be possible without using advanced routing protocols and VTi interfaces. If it is possible you'll need to review edits to vpn_route.conf, user.def.FW1,crypt.def and or table.def depending on the requirements? Also have a look at the SK,s for controlling traffic with ISP redundancy - but given the requirement for "if this tunnel fails then..." this would better suit dynamic routing and VTi's I think...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I see full logic in what you said, agreed.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Dan, still trying to digest your reply.
I think in our case, then, if we go for VTIs, on each gateway we will need:
2 VTIs (for each ISP on the local gateway). and multiply that by 2 (for each ISP on the remote gateway). And do that for each remote gateway.
Right?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yes correct, then you can use dynamic routing to define paths/failover requirements.
hope this helps...
Dan
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 17 | |
| 16 | |
| 6 | |
| 5 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 2 | |
| 2 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter