- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud Cloud Network Security CloudMates General CNAPP CloudGuard - WAF Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Open Garden In Action:
Find and Remediate Threats Everywhere!
New Appliance Announcements
and Faster Threat Prevention
Remote Access VPN – User Experience
Help us with the Short-Term Roadmap
It's Here!
CPX 2025 Content
CheckMates Go:
AI Agents
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Management
- :
- R80.20: vsx, vsx_provisioning_tool, anti-spoofing
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
R80.20: vsx, vsx_provisioning_tool, anti-spoofing
Dear Check Mates,
Recently we started with the provisioning of virtual systems using the provisioning tool, because the Check Point API (version 1.3) does not support VSX/VSLS (yet). We have to provision 50+ virtual systems.
One of the features in R80.20 is Network defined by routes: it really works well (compared with the specific option). See screenshot.
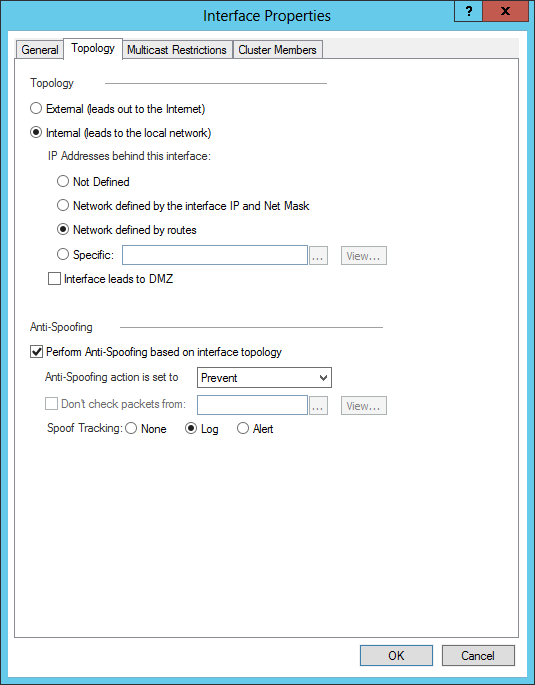
Unfortunately, the Network defined by routes can't be configured using the vsx_provision_tool:
add interface vd <vd name>[name <physical or VLAN interface name>] [leads_to <Virtual Router|Virtual Switch>] [ip <ipv4 address>[/<ipv4 prefix>]] [netmask <IPv4 netmask>] [prefix <IPv4 prefix>]] [propagate <true|false>] [ip6 <ipv6 address>[/<ipv6 prefix>]] [netmask6 <IPv6 netmask>] [prefix6 <IPv6 prefix>]] [propagate6 <true|false>] [topology <external|internal_undefined|internal_this_network|internal_specific>] specific_group <group name>]] [mtu MTU]
We have to update the topology settings for 50+ virtual systems. A cumbersome task that can easily take two hours, which only is rewarding when you are paid per hour!
Hence: automation/orchestration becomes a manual tasks.
We would appreciate if Check Point can add the following features to its next release of R80:
- Update the vsx_provisioning_tool (can be done rather quickly)
- Full API support for VSX/VSLS; at the moment there are too many repetitive tasks that have to be done manually. In reality you don't want to use the vsx_provisioning_tool but tools like Ansible.
Many thanks.
Kind regards,
Kris
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Does it not work for you or is it simply missing from the documentation, what do you see in the output of the following?
[Expert@hostname:0]# vsx_provisioning_tool -h | grep defined_by_routes
CCSM R77/R80/ELITE
9 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Gateway objects in general (including VSX) need better API support and I know it’s planned.
Updating vsx_provisioning_tool in the meantime seems reasonable but not sure if/when that’s planned.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
But just to mention:
VSX is using routing information for anti-spoofing anyway!
That's nothing new and available for a long time as routing is configured through management.
Just make sure the checkbox is active on the virtual system.
(On by default, but can be changed with parameter calc_topo_auto in provisioning tool)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jumping on to this thread.
How can I create an interface but ensure the anti-spoofing is set to detect and not prevent via the provisioning tool?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R80.20 JHF T208
PRJ-32530, PMTR-74770
VSX: UPDATE: It is now possible to define interface topology as "defined by routes" using the VSX provisioning tool.
R80.20 JHF T202
PRJ-21258, VSX-2520
VSX: Allow the addition of routes with specific group of type "Group with Exclusion" when using VSX Provisioning tool.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I remember that! I was the one that raised it with TAC.
That said - my question related to just adding an interface and ensuring Anti-spoofing did not default to 'prevent'. Is there a parameter for Anti-Spoofing that can set the mode to detect, rather then prevent?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Chris_Atkinson ,
in the VSX r81.10 admin guide there is no option to configure an interface with topology "defined by routes" with vsx provisonning tool. This is strange because it's written that is now available since r81.10 take 38
PRJ-32534,
PMTR-74770
https://sc1.checkpoint.com/documents/Jumbo_HFA/R81.10/R81.10/Take_38.htm
thank you in advance for your lights
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Does it not work for you or is it simply missing from the documentation, what do you see in the output of the following?
[Expert@hostname:0]# vsx_provisioning_tool -h | grep defined_by_routes
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I find it with "vsx_provisioning_tool -h".
So it's only missed in the documentation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
THX !
topology defined_by_routes did the job !
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 15 | |
| 4 | |
| 4 | |
| 4 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Tue 08 Jul 2025 @ 03:00 PM (CEST)
The Rise of Hybrid SASE: Beyond Cloud-Only Security Solutions EMEATue 08 Jul 2025 @ 05:00 PM (CEST)
Under the Hood: CloudGuard WAF API Security - Overview, Onboarding, and Best PracticesWed 16 Jul 2025 @ 10:00 AM (CEST)
Master GCP Security with the Cloud Architects Series (Multilingual Webinar)Wed 16 Jul 2025 @ 04:00 PM (CEST)
Operationalizing Threat Intelligence, Part II: Threat Hunting & Incident ResponseTue 08 Jul 2025 @ 03:00 PM (CEST)
The Rise of Hybrid SASE: Beyond Cloud-Only Security Solutions EMEATue 08 Jul 2025 @ 05:00 PM (CEST)
Under the Hood: CloudGuard WAF API Security - Overview, Onboarding, and Best PracticesWed 16 Jul 2025 @ 04:00 PM (CEST)
Operationalizing Threat Intelligence, Part II: Threat Hunting & Incident ResponseTue 22 Jul 2025 @ 10:00 AM (CEST)
Cyber Security Training in the Era of AI Threats: Managed SmartAwareness Explained - EMEAAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


