- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud Cloud Network Security CloudMates General CNAPP CloudGuard - WAF Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Open Garden In Action:
Find and Remediate Threats Everywhere!
New Appliance Announcements
and Faster Threat Prevention
Check Point Named Leader
Forrester Wave™: Zero Trust Platforms, Q3 2025
Remote Access VPN – User Experience
Help us with the Short-Term Roadmap
CheckMates Go:
AI Agents
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Management
- :
- Captive portal for linux SSH or Terminal windows
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Captive portal for linux SSH or Terminal windows
Hi there,
Is anyone aware if any mechanism exists to leverage Identity awareness when I would like to pass through Firewall with captive Portal enabled while using SSH or Linux with no GUI Terminal?
With browser Yes it's pretty much possible; but what if the GUI is not available?
Thanks and Regards,
Blason R
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Captive Portal is made for Browser Based Auth only - you could do a RFE here: Products and Feature Suggestions
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Captive Portal is made for Browser Based Auth only - you could do a RFE here: Products and Feature Suggestions
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Okies and thanks for the reply.
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Going back to "Captive Portal is made for Browser Based Auth only".
While this is perfectly true, browser communication in the end is just HTTP GET and HTTP POST requests.
If we would to capture a HTTP session between a, let's say Windows supported browser, and the IDA portal auth, with Fiddler or similar, and then extract and replicate the HTTP post of the authentication itself, and then script that into the linux cli box ?
Would this work ?
Afaik, Captive portal does not require any ongoing resources (keep-alive window open / cookies validation /etc) and once the IP and username have been linked on the FW side, it remains so until the configured session timeout.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Identity Awareness has an API.
Perhaps you can script up something that gives your Linux machine an identity?
Perhaps you can script up something that gives your Linux machine an identity?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks buddy!!
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
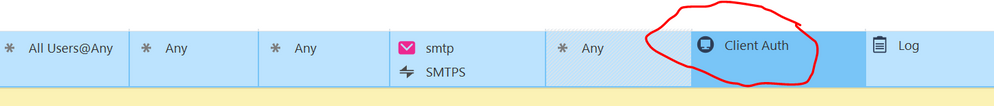
In the older times there was a possibility to telnet to port 259 on the gateway. This worked via a rule with "Client Auth" as action...
This very old document gives a good description of how to configure
http://downloads.checkpoint.com/dc/download.htm?ID=12297
But with "Client Auth" there are some limitations shown in sk115961
We had customers using this with R77.30, but never tried on R80.xx
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can find another answer in sk115242: The Linux user can use the supported SNX build for Linux CLI implementation from sk90240 (Build 800007075) instead of the Captive Portal ! See also SSL Network Extender E75 CLI Support for Mobile Access Blade Release Notes.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Client Auth has been deprecated. That said, there are a few use cases where Client Auth still makes sense (like this one).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well, the use case here is; since we have a customer whose servers are placed in DMZ and then users can access the DMZ servers and then since those are servers have outbound https access opens they do SSL Tunneling to certain sites and access it. I understand we can harden it on SSH bu disabling SSH Port forwarding but I see cases where the user has setup Squid proxy on a server and since the server has ANY Access to http/https they are able to access the internet through it.
Hence even if they take SSH of the server wondering if Captive portal could have been a better option for accessing the Internet?
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SSH can also be a SOCKS proxy as well, so there's another potential hole to close.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
RDP sessions to jump hosts in SCADA environments is another use case. I used to configure Client Auth with RSA MFA just for that purpose. Is this no loner possible in R80?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Client Auth still exists in R80.x but if memory serves, it can cause weird issues with your policy if you are using layers. We still have Client Auth rules in a couple of policies and I seem to remember testing things on a lab GW and being given some error when I tried to mix layers and Client Auth rules.
So, while the feature is still there, it may interfere with your ability to make use of newer Check Point features.
R80 CCSA / CCSE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 17 | |
| 6 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Wed 16 Jul 2025 @ 10:00 AM (CEST)
Master GCP Security with the Cloud Architects Series (Multilingual Webinar)Wed 16 Jul 2025 @ 04:00 PM (CEST)
Operationalizing Threat Intelligence, Part II: Threat Hunting & Incident ResponseTue 22 Jul 2025 @ 10:00 AM (CEST)
Cyber Security Training in the Era of AI Threats: Managed SmartAwareness Explained - EMEATue 22 Jul 2025 @ 05:00 PM (CEST)
Cyber Security Training in the Era of AI Threats: Managed SmartAwareness Explained - AMERThu 31 Jul 2025 @ 10:00 AM (CEST)
CloudGuard Network Security for Nutanix - Full Deployment with Tenant & Transit VPC - EMEA/APACWed 16 Jul 2025 @ 04:00 PM (CEST)
Operationalizing Threat Intelligence, Part II: Threat Hunting & Incident ResponseTue 22 Jul 2025 @ 10:00 AM (CEST)
Cyber Security Training in the Era of AI Threats: Managed SmartAwareness Explained - EMEATue 22 Jul 2025 @ 05:00 PM (CEST)
Cyber Security Training in the Era of AI Threats: Managed SmartAwareness Explained - AMERThu 31 Jul 2025 @ 10:00 AM (CEST)
CloudGuard Network Security for Nutanix - Full Deployment with Tenant & Transit VPC - EMEA/APACThu 31 Jul 2025 @ 05:00 PM (CEST)
CloudGuard Network Security for Nutanix - Full Deployment with Tenant & Transit VPC - AMER/EMEAAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter