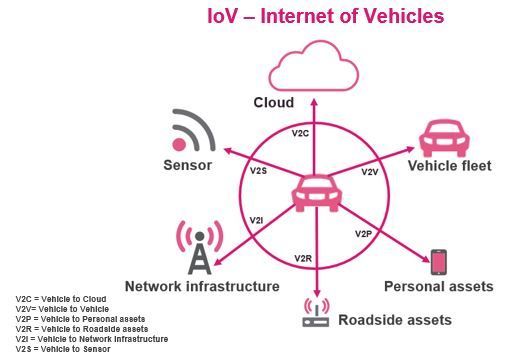
Figure 1: Internet of Vehicles assets
The automobile industry is witnessing a groundbreaking revolution with the advent of electric vehicles, EV’s. These vehicles, equipped with advanced internet connectivity and integrated technologies, are reshaping the way we drive; optimizing safety, efficiency and convenience. The connected car has become a network of its own with all those connected assets, expanding the EV footprint and attack surface. EVs represent remarkable benefits, both to drivers and society as a whole. Allow me to highlight a few.
Enhanced safety measures
One of the most significant advantages of EV’s is the integration of advanced safety features into vehicles. These vehicles rely on a network connection to collect and exchange data with other cars, infrastructure and even pedestrians. This allows them to proactively detect and avoid potential collisions, reducing the number of accidents on the road. Additionally, EV’s often come equipped with technologies such as lane departure warnings, blind-spot monitoring, adaptive cruise control and automatic emergency braking, further ensuring passenger safety. Those systems require preventative security controls, ensuring reliability.
Improved efficiency and sustainability
EV’s are key players in promoting sustainability and reducing carbon footprints. By leveraging real-time traffic data, these vehicles can suggest the most optimal routes, minimizing time spent on the road and reducing traffic congestion. Moreover, EV’s can optimize fuel efficiency by analyzing traffic patterns and adapting driving strategies, leading to reduced CO2 emissions and improved fuel economy. By embracing EV’s, we can collectively contribute to a greener and more sustainable future.
Convenience and seamless connectivity
The integration of internet connectivity in EV’s opens up a world of convenience for drivers and passengers. EV’s can provide personalized infotainment systems, allowing occupants to access real-time news, music and other entertainment options or streaming services. Additionally, these vehicles offer advanced navigation systems with voice commands, making it easier than ever to reach your destination hassle-free. Connectivity also, enables drivers to make hands-free phone calls, send messages and even access their smart home devices remotely. With connectivity and communication, so called V2X “Vehicle to everything” communication topics like vehicle operations management, traffic efficiency are addressed. V2X communication may utilize GPS, 5G, LTE and more.
Smart car maintenance and remote diagnostics
EV’s revolutionize maintenance and diagnostics practices. Through continuous monitoring and analysis of various vehicle components, EV’s can predict and alert drivers or service centers about potential malfunctions, allowing for preemptive repairs. This proactive approach helps prevent breakdowns, saves money on costly repairs and maximizes overall vehicle lifespan. Remote software updates also ensure that EV’s stay up-to-date with the latest technology advancements, bolstering their performance and usability. The concern here is how are EV’s updated in a secure manner, both cyber security and safety wise.
Data utilization and improved transportation planning
The immense amount of data generated by EV’s offers valuable insights for transportation planning and development. Governments and transportation authorities can analyze this data to identify traffic patterns, assess infrastructure requirements and make informed decisions regarding road expansions and traffic management systems. This data-driven approach can lead to more efficient transportation networks, reduced travel times, and improved urban planning. Car data monetization concerns still do need to be addressed.
In theory, could threat actors hijack systems to compromise core vehicle functions?
Yes “smart” vehicles, EV’s are very attractive assets. Everyday, new vulnerabilities are discovered. or example, hackers can hijack user accounts, impeding charging and even gaining access to home networks. If we take a look at Charge Points, CP’s which is using Open Charge Point Protocol (OCCP), we see that OCCP has been found to have many vulnerabilities and exploits. Think of the absence of encryption, access control and timely vulnerability patches. Basically, OCCP is lacking security best practices.
Other examples of compromised EV’s are: The most notorious is the Jeep hack from 2015! In a more recent event, a French team hacked a Tesla at a hacking conference in Vancouver. But it is also about EV chargers, keyless car entry here (my favorite, also really old) here, here, and much more!
And what about how?
- Attackers could impersonate charging station admin users and manipulate the system to provide free charging service.
- In the Isle of Wight, hackers disrupted the EV charging service by:
- Hacking the EV monitor to show inappropriate content
- Displaying high voltage fault codes to EV owners, preventing them from charging their vehicles, and leaving them stranded with an empty battery
- How Russian EV chargers were successfully hacked, displaying pro-Ukrainian messages on the monitor and more
- The new Combined Charging Stations (CCS) attack technique that could potentially disrupt fast charging stations. The attack was dubbed “brokenwire”
- Ransomware attacks could be executed against not only EV chargers, but also the EV users
At present, why aren’t connected vehicles sufficiently secure?
The EV industry lacks standardization. The security measures in EVs have not yet been standardized across the industry. This indicates that some vehicles may have better security features than others, making it easier for hackers to exploit certain vulnerabilities. Inconsistencies in security functionalities make it challenging to implement industry-wide protections, potentially leaving certain electric vehicles more exposed to attacks.
Other challenges:
- Vulnerabilities in software and hardware: Connected vehicles often rely on complex systems that include software, firmware, sensors, and other hardware components. These systems can be vulnerable to cyber threats if proper security measures are not implemented.
- Human error. The security of connected vehicles also depends on the actions of the people who use and maintain them. Human error, such as leaving a door unlocked or using weak passwords, can make it easier for hackers to gain access to the vehicle’s systems.
- Proliferation of connected devices: The increasing number of devices and sensors that are connected to vehicles can increase the risk of cyber attacks. Each device presents a potential entry point for hackers.
- Complexity of supply chain: The connected vehicle ecosystem involves multiple players, including manufacturers, suppliers, and service providers. The complexity of this supply chain can make it difficult to identify and address security vulnerabilities.
Can you explain what Over-The-Air (OTA) updates are and how they work in the context of connected vehicles?
The rapid advancement of EVs, has not only introduced accessible, environmentally friendly driving options, but has also given birth to another innovation – Over-The-Air (OTA) updates. OTA updates are reshaping the landscape of electric vehicles and this convergence is shaping a promising future for sustainable transportation.
Over-The-Air (OTA) updates are a type of software update that can be delivered wirelessly to a device or system. In the context of connected vehicles, OTA updates allow automakers to remotely update the software of a vehicle’s electronic systems, such as its entertainment or navigation systems, as well as its safety features, such as its automatic emergency braking or lane-keeping assist.
OTA updates work by utilizing the vehicle’s built-in communication module, which is connected to the internet via a cellular network. When an update is released, the vehicle’s software downloads the update package and installs it on the vehicle’s systems. This process can happen automatically while the vehicle is parked and connected to a Wi-Fi network, or it can be initiated manually by the owner through the vehicle’s infotainment system.
The benefits of OTA updates in connected vehicles include faster and more efficient updates, as well as the ability to remotely address software bugs or security vulnerabilities. Additionally, OTA updates can allow automakers to add new features or improve existing ones without requiring the vehicle to be taken to a dealership for a software update.
In summary, OTA updates are a wireless way to update a vehicle’s software systems and can be essential for keeping the vehicle up-to-date with the latest features, bug fixes, and security patches.
What kind of infrastructure is required to support OTA updates for connected vehicles? How does that play into the security equation?
To support OTA updates, several infrastructure requirements need to be in place:
- Vehicle Connectivity: The car must have a reliable and high-speed internet connection to download software updates. This can be achieved through built-in cellular modems, Wi-Fi connectivity, or via LTE.
- Telematics Control Unit, TCU: A TCU is a dedicated onboard computer that enables communication between the car and external servers. It manages the OTA update process, downloads and installs software updates.Finally, it handles data transmission securely.
- Secure Server Infrastructure: Automakers need to establish a secure server infrastructure to store and distribute software updates. This includes cloud-based servers that can handle a large number of update requests and protect against potential cyber threats.
- Authentication and Security Measures: Robust security measures are necessary to ensure that only authorized software updates are accepted by the car’s systems. This can involve cryptographic protocols, digital signatures, and vehicle identification verification to prevent unauthorized access.
- Data Management: The car’s system must have sufficient memory and storage capacity to download and store the software update, as well as handle the installation procedure. Data management systems ensure that updates are stored securely and can be rolled back if necessary.
- Fail-Safe and Recovery Mechanisms: OTA updates carry the risk of failure during transmission or installation. Vehicles need fail-safe mechanisms to minimize the impact of a failed update, such as the ability to revert to the previous software version and maintain essential functions.
- User Consent and Data Privacy: Car owners should have control over when and how updates are installed. Automakers need to establish clear policies regarding user consent and communicate the implications of OTA updates, including data privacy considerations.
Based on your real-world experiences, can you share best practices, recommendations and/or policy suggestions?
It is important to acknowledge the security concerns that come with this burgeoning technology. Without robust security measures in place, EVs remain vulnerable to cyber attacks, theft, and other potential threats. The future growth of the electric vehicle industry relies on addressing and rectifying these security concerns to ensure a safe and secure experience for EV owners. Efforts towards standardization, improved authentication systems, regular software updates, and enhanced security features will be crucial in bolstering security measures and inspiring consumer confidence in adopting electric vehicles.
OTA best practices:
- Security: Implement robust security measures to safeguard the entire OTA update process. This includes secure communication channels, encryption, and authentication mechanisms to prevent unauthorized access and tampering.
- Authentication and Authorization: Implement a robust authentication and authorization mechanism to verify the authenticity and integrity of the OTA updates. This ensures that only authorized updates from trusted sources are accepted by the vehicle.
- Incremental Updates: Provide incremental OTA updates, which deliver only the necessary changes, as opposed to downloading the entire software package. This saves time, reduces data usage, and enhances efficiency.
- Bandwidth Optimization: Optimize OTA updates by efficiently using the available bandwidth. Prioritize critical updates and distribute them intelligently to minimize network congestion and deliver updates efficiently.
- Fail-Safe Mechanisms: Incorporate fail-safe mechanisms within the vehicle to handle any potential failures or interruptions that may occur during the OTA update process. This ensures that the vehicle remains functional even if an update fails or is interrupted.
- Data Protection: Ensure that user data stored within the vehicle is protected during the OTA update process. Implement measures to retain user preferences, settings, and personal data to minimize any inconvenience caused by updates.
- User Communication: Establish effective communication channels with vehicle owners/users to inform them about upcoming OTA updates, their purpose, and any changes or improvements they may bring. This helps to encourage user acceptance and understanding of the update process.
- Testing and Validation: Thoroughly test and validate OTA updates before deploying them to ensure compatibility, proper functionality, and validation of user requirements. This minimizes the risk of introducing bugs or issues during the update process.
- Remote Monitoring and Diagnostics: Implement remote monitoring and diagnostics capabilities to collect information about the vehicle’s behavior, performance, and potential issues. This enables manufacturers to identify problems, evaluate the need for OTA updates, and address them remotely as needed.
- Privacy: Ensure that user privacy is protected during OTA updates. Minimize the collection and transmission of sensitive user data and implement transparent privacy policies to gain user confidence in the update process.
Conclusion
EVs are equipped with complex computer systems that control various functions, including acceleration, braking, and steering. If these systems are compromised, it could lead to dangerous situations, including remote control of the vehicle or unauthorized access to sensitive data. Hence, implementing preventative security measures is imperative to protect the integrity and safety of EVs.
Furthermore, Over-the-Air (OTA) technologies have revolutionized the way software and firmware updates are delivered to various devices and vehicles. OTA updates allow for remote patching, bug fixes, and enhancements, offering convenience and efficiency. However, if OTA systems are not adequately secured, they can be vulnerable to malicious attacks. Unauthorized access to OTA systems can compromise the security and functionality of devices, leading to unauthorized surveillance, data breaches, and even remote control of vehicles or technologies. Consequently, preventative security measures are necessary to protect OTA systems, ensuring their reliability and integrity.
In conclusion, EVs, CP, and OTA technologies are integral aspects of our modern society. However, their widespread adoption also brings significant security concerns. To mitigate potential threats and attacks, preventive security measures are essential. These measures will not only protect the safety and integrity of EVs, CPs, and OTA systems, but also guarantee the reliable and uninterrupted functioning of our society. Connected cars are not just vehicles; they represent a pivotal transformation in the automotive industry. The value they bring through enhanced safety measures, improved efficiency, added convenience, and the potential for data-driven transportation planning is unparalleled. Implementing robust security protocols should be a top priority to safeguard these technologies and ensure a secure and sustainable future.



