- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure Users and Access)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
May the 4th (+4)
Roadmap Session and Use Cases for
Cloud Security, SASE, and Email Security
SASE Masters:
Deploying Harmony SASE for a 6,000-Strong Workforce
in a Single Weekend
Paradigm Shifts: Adventures Unleashed!
Capture Your Adventure for a Chance to WIN!
CPX 2024 Content
is Here!
Harmony SaaS
The most advanced prevention
for SaaS-based threats
CheckMates Go:
The Difference Is In The Details
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: sk113479 | Why are packets being allowed that ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sk113479 | Why are packets being allowed that are not in policy?
We see in the firewall logs for an inbound port 22/sftp connection being allowed through -- at least the first packet is (two of them actually, each one a second apart). Not only is it allowed through the firewall, but our host-based firewall on the windows server detected the connection as well. The problem: we don't allow this ip/port combo through the firewall.
In the firewall log we see "Connection terminated before the Security Gateway was able to make a decision: Insufficient data passed" and a reference to sk113479. But the question is -- why is even one packet getting through when there's nothing even related to this type of connection?
I understand that if the firewall sees a possible match it might do this, but I don't see how that would be the case with our policy and especially with the limited inbound connections we have. As much as I love seeing packets coming from a VPN server on the other side of the world being let through into our network, is there a way to prevent it?
Gateway is running R81.10.
- Tags:
- sk113479
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
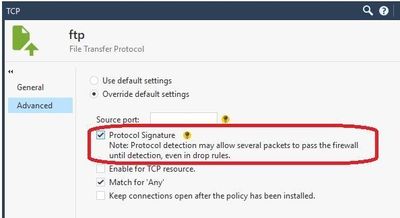
Do you have the protocol signatures option enabled? e.g.
Reviewing the issue with TAC might also be appropriate in terms of the level of detail you're happy to share.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There are two firewall rules related to the public IP I'm seeing this activity on. One is a custom TCP port and the other does not have "Protocol Signature" enabled. Do we know if it is where "Protocol Signature" is enabled on any service in any rule in the policy then it behaves this or does it also have to be related to the IP's involved?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Most likely the rules that "potentially match" are not specific enough or include things that invoke App Control.
Can we see ALL the "potential match" rules in your rulebase for this traffic?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm surprised with our current multi-layer rulebase, it's not enough logical separation to avoid this. I'm not seeing anything that would be a "potential match" until you get down into sub-layers that would have filtered out this traffic simply from the child's parent layer.
My rule base is essentially:
1 Source: Internet IPs (New Layer)
- 1.1 Allow rules
2 Source: Internal IPs (New Layer)
- 2.1 Allow rules
So what you're saying is that because I have "potential matches" on the 2.1 rules for something coming from the internet (because source may be blank on those or destination is an application like Facebook) then it's going to allow traffic from the internet like it was in the 1.1 layer?. That seems pretty wild to me.
What if I took all the inbound internet rules and put them in their own ordered Access Control layer like what was done for GEO IP? Would that be enough of a logical separation for the engine to not evaluate other stuff in the main layer?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Rules with "Any" service shouldn't cause this, it's rules that involve App Control/URL Filtering services.
We would need to see the exact rules involved (including the top-level rules leading to nested layers) in order to assist.
This might be better done through the TAC: https://help.checkpoint.com or possibly your Check Point SE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just a follow-up, we duplicated out our Source Internet rules to its own ordered layer without App & URL filtering enabled on it and it started blocking traffic normally. "Duplicated" because we still had to leave the rules in the final ordered layer to Allow acceptable traffic.
🚩 CPNotEnoughDataForRuleMatch does not mean only a few packets were let through for traffic identification.............. For example with FTP (Protocol Signature not checked), full authentication with the service can happen before the gateway steps in and blocks it like it should. We saw '230 Login OK' packets being sent back and the gateway was logging a block.............
It also advertises to the public that you have publicly reachable services even though the firewall is set to whitelist source IPs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This speaks to the services used in the relevant rules.
In a Firewall only layer, the only valid services are ones that can be matched on the first packet (TCP/UDP services).
If you use App Control/URLF services, those services may require multiple packets to match (or not).
Note that the service FTP is a "simple" service, even though it has an INSPECT handler associated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yeah -- so if anyone publishes services out to the Internet and their firewall policy has App Control/URLF enabled -- they are susceptible to attacks from the general public regardless if they have a source restriction defined or not.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It depends on the construction of the policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you expand on that?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It comes down to the exact “services” or “applications” that are used in the relevant rules involving the same source and destination.
This is relevant due to the column-based matching used to evaluate the rulebase: https://community.checkpoint.com/t5/Management/Unified-Policy-Column-based-Rule-Matching/td-p/9888
A service like SSH or https will match on the first packet.
A “service” like Gmail cannot be identified on the first packet and will require several packets to be permitted before a final decision is made.
Order of the rules matters as well.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 20 | |
| 18 | |
| 13 | |
| 11 | |
| 6 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 3 |
Upcoming Events
Thu 09 May 2024 @ 05:00 PM (CEST)
Under the Hood: Automate Azure Virtual WAN security deployments with TerraformThu 16 May 2024 @ 10:00 AM (CEST)
EMEA: Playblocks & MS Defender – Security Automation DeepDive into New Endpoint IntegrationThu 16 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - ACHTUNG, Sie werden gehackt! So schützen Sie sich!Thu 16 May 2024 @ 05:00 PM (CEST)
Americas: Playblocks & MS Defender – Security Automation DeepDive into New Endpoint IntegrationThu 16 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - ACHTUNG, Sie werden gehackt! So schützen Sie sich!Fri 17 May 2024 @ 10:00 AM (CEST)
CheckMates Live Netherlands - Sessie 26: ElasticXL & VSNext DescriptionTue 21 May 2024 @ 10:00 AM (CEST)
CheckMates Live DACH - Einführung in Check Points Hyperscalinglösung - Quantum MaestroAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
Facts at a Glance
User Center