- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: White Paper - URL Filtering using SNI for HTTP...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
White Paper - URL Filtering using SNI for HTTPS websites
Author
Abstract
The document describes how to leverage Server Name Indication (SNI) when using URL Filtering Software Blade.
For the full list of White Papers, go here.
32 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Kevin_Jones , thank you for a brief and concise document describing SNI filtering functionality. Many of my clients can benefit from reading it.
In regards to its general availability: your document is from December of last year. When is this functionality will be available in R80.20 by JHFA?
Thank you,
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R80.30
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is this functionality will be available in R80.20 by JHFA???
Considering right now R80.20 is the recommended version
Considering right now R80.20 is the recommended version
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is that available in R80_10_JUMBO_HF?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For URL filtering this is on by default
I am told that NG bypass does not require any extra configuration I am still validating
I am told that NG bypass does not require any extra configuration I am still validating
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can CheckPoint teach us how to use "Next Generation Bypass"?
Thanks for clarification.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That is part of this White Paper - URL Filtering using SNI for HTTPS websites !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is this functionality already available in R80_10_JUMBO_HF?? thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As of now, this is a separate HF that goes on top of T154.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great information!
I have two qustions:
1) Can anyone confirm is the following feature is included in the new engine of SSL Inspection in R80.30? R80.30 doesn't need the probe bypass feature since it checks de Client Hello and the certificate. Also, it works with Categorize HTTPS without SSL Inspection and without turning on the kernel parameters? I'll try to check this later in a lab enviroment.
"Using this field, rather than relying on the CN of the certificate, gives more specific and accurate information about the requested site. The recently released hotfix for Check Point R80.10 gateways does change this behavior and utilize the SNI extension for categorization. Once installed, the feature can be enabled with the following command: fw ctl set int urlf_use_sni_for_categorization 1 This hotfix also allows a further check to make sure that the SNI requested by the client matches one of the SAN entries on the certificate. To enable this feature, use this command: fw ctl set int urlf_block_unauthorized_sni 1"
2) Is there any benefit in having "Categorize HTTPS sites" AND Outbound SSL Inspection? There are many posts that state that they are mutually exclusive, but in R80.20+ you can have both turned on. So far in my testing I could not see any benefits. Maybe it doesn't inspect all the https traffic?
Thanks!
Federico Meiners
____________
https://www.linkedin.com/in/federicomeiners/
https://www.linkedin.com/in/federicomeiners/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@FedericoMeiners , the SSL categorization is there simply to improve the Application Control and URL filtering. SSL inspection actually allow the payload to be analyzed by other TP blades as well as Content Control and DLP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Vladimir I know that, but what is the effect/advantage of having Outbound SSL Inspection + HTTPS Categorization? You can turn them both in R80.20+
____________
https://www.linkedin.com/in/federicomeiners/
https://www.linkedin.com/in/federicomeiners/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Consider, for instance, the situation when you are exempting certain traffic from SSL inspection based on its categories, i.e. financial and health.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I see here many questions about SNI enhancement availability with R80.20.
As fas as I am concern, R80.20 can have SNI functionality back-ported, with a special HFA, with is not part of the regular Jumbo.
@Oren_Segev, can you please give more details?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Could someone please confirm if this functionality works on R80.20? thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Any idea when this functionality (URL Filtering using SNI for HTTPS websites) will be available for Gaia Embedded (7xx/14xx)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
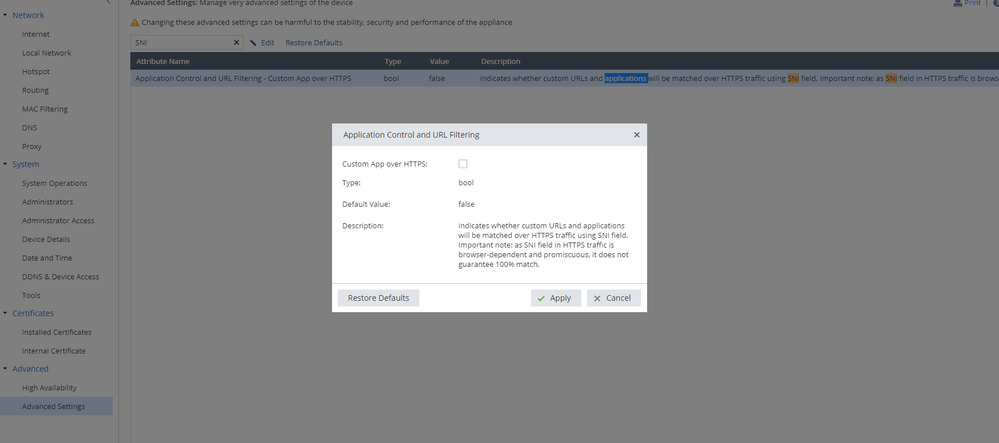
Hi Miguel,
In matter of fact, SNI for APPI/URLF it is already available on Gaia Embedded on recent firmwares (disabled by default) in locally managed mode.
Go to Device -> Advanced Settings and find [Application Control and URL Filtering - Custom App over HTTPS].
Enable the parameter and you're good to go.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @Tom_Hinoue!
What about centrally managed mode?
What about centrally managed mode?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Tom_Hinoue ,
Which version are you running on this picture?
I'm running Embedded GAIA R77.20.87 - Build 960 and I wasn't able to see this parameter Custom App Over HTTPS as shown below
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @FelipeTropeia,
This feature is only available currently on Locally Managed mode of SMB appliances since R77.20.80+, and not Centrally Managed mode as what I believe you are using now from your provided image. (and apologies to @MikeB for missing your post)
From what I know that SNI is available on R80.10+ in latest Jumbo Hotfixes on maintrain, I believe SNI on Centrally Managed Gaia Embedded which runs on R77 code is not compatible with SNI inspection yet (some one correct me if I'm wrong)
Staring the new 1550/1590 the OS now runs on R80.20 code, so maybe we can expect SNI for Centrally Managed soon 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
https inspection needs to be enabled for sni to work?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
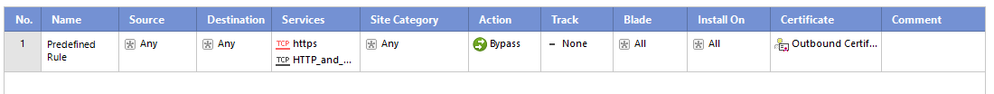
as far as I could read...Yes, you must enable HTTPS Inspection for SNI to work.
You can simple enable HTTPS Inspection with a rule to bypass all (any any bypass)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SNI support for Site Categorization
Starting from R80.30, a new functionality allows the categorization of HTTPS sites before the HTTPS Inspection begins, and prevents connectivity failure if the inspection does not succeed.
SNI is an extension to the TLS protocol, which indicates the hostname at the start of the TLS handshaking process.
The categorization is performed by examining the SNI field in the client hello message at the beginning of the TLS handshaking process. To make sure that you reached the right site, the SNI is verified against the Subject Alternative Name of the host, which appears in the certificate.
After the identity of the host is known and verified, the site is categorized, and it is determined whether the connection should be inspected or not.
SNI support is enabled by default.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Small correction. SNI works out of the box event without enabling HTTPSi on R80.40. On R80.30, you have to enable HTTPSi for it to work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
so for firewall with r80.30 we should add https inspection layer on policy and set rule in this layer with action bypass for with any source and destination?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Correct. As already mentioned above by @MikeB
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For anyone reading this white paper and Checkmates thread and believes (like me) you are all good with R80.40 without HTTPS Inspection policy and blade at all
- or with other words -
When you want to use only "HTTPS Inspection Light", which means you enabled "Categorize HTTPS sites" checkbox in URL Filtering blade settings:
Let me give you this litte hints:
- Gateway is watching the TLS handshake (not intercepting it, because we don't use full HTTPS Inspection). I guess this is done by CPAS.
- If Gateway sees problems in this TLS handshake, connection may be permitted (depending on your policy), but certificate information is not used for site categorization by URL Filtering blade. You will see a log entry of type Detect from URL Filtering blade, telling you about the problem, your gateway has with this handshake. There is no hint in the log, that site categorization by URL Filtering blade is limited because of this problem.
- If you retry the connection attempt, please take care: you will get only one log entry of this type with the first try, because site categorization will be cached in table cptls_host_name_cache.
- Problems could be
- Expired certificate
- Revoked certificate
- Untrusted CA
- While expired certificate and revoked certificate are easy to understand, the part with untrusted CA is interesting. While we are NOT intercepting TLS handshakes by NOT using HTTPS Inspection blade, the gateway still verifies the server certificate against its own HTTP Inspection trusted CA list. If this fails, URL categorization by SNI will not work.
- So when you (like me) never checked HTTPS Inspection blade settings in old SmartDashboard (still not migrated to SmartConsole in R80.40), you might not notice, that the Trusted CA list is not up to date or does not contain the CA certificates you need.
You can learn about that in sk64521 and sk159872 which also tell you, that you have to take care of the site categorization cache (table cptls_host_name_cache) and the responsible deamon (wstlsd) yourself after fixing the Trusted CA list.
Update of the HTTPS Inspection CA Trust List is documented in sk64521, but this did not work on our side. SMS downloaded recent version 2.6 zip file sucessfully (month ago), but SmartDashboard did not show an available update. We have a TAC case running for this. Workaround: Download zip file from SMS to your client with scp or something and upload it manually using SmartDashboard.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 11 | |
| 9 | |
| 9 | |
| 8 | |
| 6 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 1 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter