- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
CheckMates Fest 2025!
Join the Biggest Event of the Year!
Share your Cyber Security Insights
On-Stage at CPX 2025
Simplifying Zero Trust Security
with Infinity Identity!
Zero Trust Implementation
Help us with the Short-Term Roadmap
CheckMates Go:
What's New in R82
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Traffic to port 500 is accepted by implied rule on...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Traffic to port 500 is accepted by implied rule on 0
We have observed a traffic permit from Source IP 106.75.64.59 (Blacklisted 6/114) to destination IP 202.56.229.167 on destination ports 500.
Observation:
* High no. of events to same destination IP
* Anomaly: Excessive Firewall Permit from Multiple Source
* As per the log analysis, we found there is a Firewall Permit on bharti firewall.
We have analysed the external to external traffic from source 106.75.64.59 (Blacklisted 6/114) to a single destination port.
Do we need to block the source if the communication is not legitimate?
If the source IP is legitimate, please confirm whether we can whitelist the same in our rule.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Prime,
There are some implied rules that open certain ports on a gateway.
Depending on the settings in "Global Properties > Firewall" the ports can be different.
You can find an overview of used ports here:
R80.x - Ports Used for Communication by Various Check Point Modules
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
7 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To confirm is the destination currently used to terminate VPNs?
(This may alter the suggestions provided)
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
(202.56.229.167)this is our secondary firewall outside interface IP, we are not using for VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Prime,
There are some implied rules that open certain ports on a gateway.
Depending on the settings in "Global Properties > Firewall" the ports can be different.
You can find an overview of used ports here:
R80.x - Ports Used for Communication by Various Check Point Modules
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
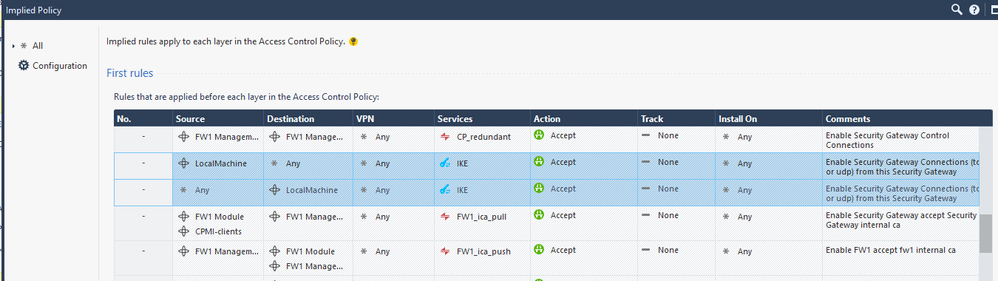
All IKE UDP 500 traffic to and from the gateway interfaces themselves (this does not include IKE traffic trying to transit the gateway) will always be allowed by these implied rules:
Once allowed the source IP address will be checked against a list of known VPN peers by vpnd, and if it doesn't match the IKE traffic is discarded. While in most cases the two endpoints for a site-to-site VPN have fixed IP addresses, all IKE traffic to the gateway's interfaces must be initially accepted from any source IP address to cover the case of a Dynamically Assigned IP (DAIP) VPN peer.
Gateway Performance Optimization R81.20 Course
now available at maxpowerfirewalls.com
now available at maxpowerfirewalls.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
is it the legitimate traffic and can we whitelist the same in our rule?
Should we block the source if the communication is not legitimate?
Attached the log
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can't directly block UDP/TCP port 500 in the main Network/Firewall policy because it is allowed in the implied rules which are always "first"; it has to be initially allowed then later denied by vpnd as an invalid peer. The only way to change this is to modify the implied rules settings in the Global Properties, but this is a great way to cause all kinds of nasty problems with basic firewall functionality and is NOT recommended.
I would suggest putting this attacking IP address in the SecureXL blacklist or in a SAM rule (sk112454: How to configure Rate Limiting rules for DoS Mitigation (R80.20 and newer)), which would kill the traffic before it is even able to reach the first implied rules. Or you could simply block that entire country with Geo Policy since it is applied prior to the first implied rules. Geo Updatable Objects are referenced after the first implied rules, so you'll need to use Geo Policy instead of Geo Updatable Objects for blocking the attacker in this specific case.
Gateway Performance Optimization R81.20 Course
now available at maxpowerfirewalls.com
now available at maxpowerfirewalls.com
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 7 | |
| 7 | |
| 7 | |
| 6 | |
| 4 | |
| 4 | |
| 4 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Fri 10 Jan 2025 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 32: Infinity External Risk Management (CyberInt)Fri 10 Jan 2025 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 32: Infinity External Risk Management (CyberInt)About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter