R80.20+ with enabled HTTPS inspection
|
If the https inspection is enabled, the parameter host from http header can be used for the url because the traffic is analyzed by active streaming. Check Point Active Streaming (CPAS) allow the changing of data, we play the role of “man in the middle”. CPAS breaks the connection into two parts using our own stack – this mean, we are responsible for all the stack work (dealing with options, retransmissions, timers etc.). An application is register to CPAS when a connection start and supply callbacks for event handler and read handler. Several protocols uses CPAS, for example: HTTPS or also VoIP (SIP, Skinny/SCCP, H.323, etc.), Security Servers processes, etc. CPAS breaks the HTTPS connection into two parts using our own stack – this mean, we are responsible for all the stack work (dealing with options, retransmissions, timers etc.)
More read here: R80.x Security Gateway Architecture (Content Inspection)
| Tip 1 - Enable https inspection on the gateway for R80.30 |
> Gateway & Service > [Gateway] > HTTPS Inspection
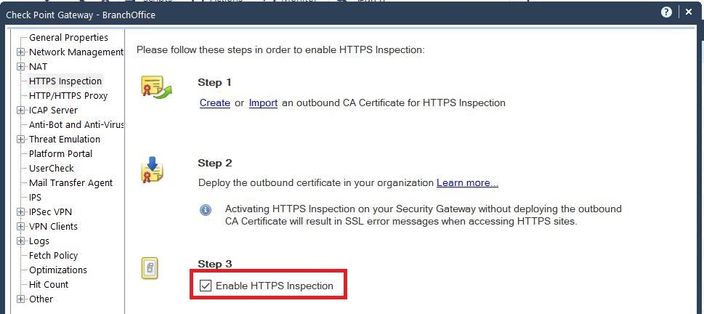
> Now creat https rules and configure all blades
| R80.20+ without enabled HTTPS inspection (use SNI) |
If the https inspection is bypassed by https inspection rule, SNI is used to recognize the virtual URL for application control and url filtering.
SNI is investigated during TLS Handshake it inspect the ‘Client Hello’ SNI field and
the server name in ‘Server Hello’. The subject field content is compared with the server name. If subject contains a Wildcard the content of subject alt name field is inspected: A valid certificate would include the server name here.
For more informations about URL Filtering see sk92743.
More read here: URL Filtering using SNI for HTTPS websites.pdf
| Tip 2 - Enable SNI without https inspection in R80.30 for “Application Control & URL Filtering Settings” |
> Gateway & Service > [Gateway] > HTTPS Inspection
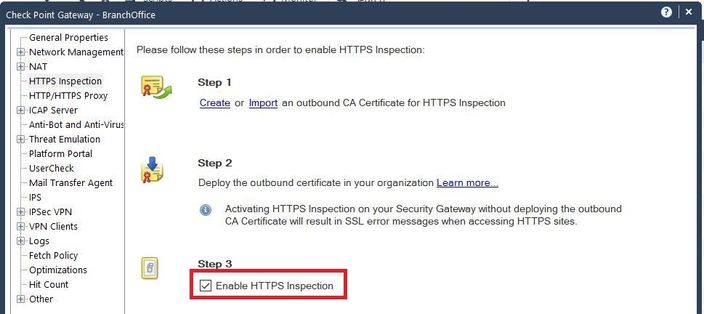
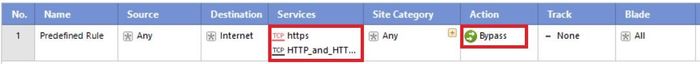
> Creat HTTPS bypass rule
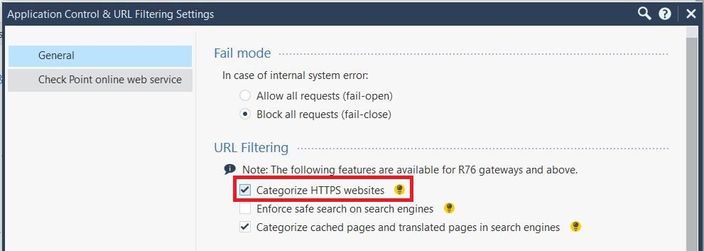
> Management & Settings > Blades > Application Control > Advanced Settings
| Tip 3 - Performance view SNI vs. HTTPS inspection |
From a performance view, it is more effective to use the SNI function if you only use URL filtering and application control.
More interesting articles:
- R80.x Architecture and Performance Tuning - Link Collection
- Article list (Heiko Ankenbrand)
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips






