- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: R80.10 - VPN traditional mode to simplified mo...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
R80.10 - VPN traditional mode to simplified mode
We have the following problem. We have a SMS with version R80.10. Now, we have add a new 1490 SMB Appliance Cluster to the policy. If we install the SMB cluster policy, we become the following error: "VPN configuration in traditional mode is not supported on Check PointSmall Office Appliances."
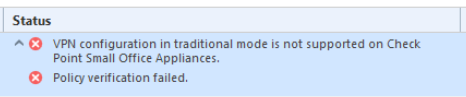
Under R77.30 I can use the wizard to convert the traditional mode policy to simplified mode policy.
With R80.10 I can no longer found this wizard.
Now my question:
Is it possible to convert the traditional mode VPN policy to simplified mode?
What do I have to do under R80.10.
Regards
Heiko
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I know new Traditional Mode VPNs cannot be created in R80.x.
I presume we did not port the relevant wizard to R80.x since Simplified Mode VPNs have been the default since R5x.
My guess: you'll have to do it manually.
22 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I know new Traditional Mode VPNs cannot be created in R80.x.
I presume we did not port the relevant wizard to R80.x since Simplified Mode VPNs have been the default since R5x.
My guess: you'll have to do it manually.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Dameon,
THX for the fast answer.
The problem with historical Traditional Mode VPN features. 
(migration path over the years R5x > R6x> R7x >R80.10)
Small suggestion for improvement:
Maybe you should get a warning when executing "migrate export" or "pre upgrade verifier" here.
Regards
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm surprised you don't get such a warning (especially if we don't include the conversion wizard).
Tomer Sole, think we might be able to suggest this get added?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Second that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
when you run the upgrader verification service you get a warning.
Firewall policies with Traditional VPN mode
Description:
Traditional mode refers to legacy VPN policy, which was replaced by Simplified VPN (first introduced at 2002 in version NG FP3). Please change the below policies by using one of the methods:
1. Convert your Firewall policies: In SmartConsole, go to Policy > Convert To > Simplified VPN, and follow the wizard instructions.
2. In your Firewall policy, delete rules that contain the actions Encrypt or Client Encrypt.
If you have a specific case in which you have to use Traditional VPN mode, please contact Check Point support.
These are the Traditional VPN policies or rules that must be converted or deleted:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Wonder if it shows when you run pre_upgrade_verifier on the CLI or if that shows only on the online one.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Mia for your answer.
This is SMS R80.10. Unfortunately this is no longer available.
This works for older versions R77.30 and lower:-)
Regards
Heiko
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
What will happen to VPN configuration after convert to simplified VPN rules?
Need to create for IPsec VPN communities manually after conversion?
Based-on my conversion, need to setup for VPN communities configuration after conversion.
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We have the same issue.
😞
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A few weeks back I was trying to add an Inline Layer for APCL/URLF o a policy and it would not let me due to the fact it was a Traditional Mode VPN policy.
Thing was there was No VPN at all, IPSEC was turned off on the gateway, but still it was nagging about it.
In this case there was nothing to convert but just copy to a new policy and all done, but still...
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
can you please share the builds you are using of R80.10?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
We also have a few security gateways that are using a Traditional Mode VPN Policy.
They do not have any VPN configuration and we would like to convert them to simplified mode to be able to create Inline Layer for APCL/URLF.
I just noticed sk171035 where it seems we could disable the Traditional Mode with the following command:
Disable Traditional VPN mode
# mgmt_cli -r true -d DOMAIN_NAME set package name "POLICY_PACKAGE_NAME" vpn-traditional-mode false --format json
Could anyone confirm if this would change the policy to be a "fully" Simplified VPN Policy?
Please note that the article title is "How to convert a Simplified VPN Policy to a Traditional VPN Policy in R80.X", but I think the title should be "How to convert a Traditional VPN Policy to a Simplified VPN Policy in R80.X"
We are running version R80.20, take 183.
Thanks for your help!
Best regards,
Harry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That SK was created…yesterday.
The way I read it is that command merely flips the bit in the policy layer so that it will be marked as a simplified VPN mode instead of traditional VPN mode.
It won’t actually convert any traditional VPN rules to simplified VPN rules, but if you don’t have any VPN rules in that layer…it should do the trick.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @PhoneBoy, this is how I also understood the article. Do you know why this information was not released earlier, since this looks like a simple fix? We were considering manually recreating the whole policy, but hesitated since it would require a lot of effort. @Maarten_Sjouw mentioned that he copied to a new policy to solve it, but at least when I try to clone the policy it still shows up as VPN Traditional mode.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, it is not a simple fix. Traditional has phase 2 parameters defined per rule, and dropping this info is something that can backfire.
The technique in the mentioned SK has had to be verified and proven to be safe, before publishing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you @_Val_. I fully understand that the fix would be difficult if VPN is used, but in our case we do not have VPN configured on those gateways.
Could you confirm if changing the package parameter (vpn-traditional-mode to false) on the policy would be the same as creating a new policy in simplified mode?
Thanks for your help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Then you are good to go. Technically, it is not the "same", but it will work for you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the information @_Val_. Would you be able to explain in which way it would be technically different? I would like to avoid facing an issue in the future due to using this method to change to simplified mode instead of creating a new policy as simplified mode.
Also, please note that the article title still says "How to convert a Simplified VPN Policy to a Traditional VPN Policy in R80.X", but I think it should be "How to convert a Traditional VPN Policy to a Simplified VPN Policy in R80.X"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Without VPN rules defined, it is practically the same. Otherwise, there are quite a few places where local definitions should be flipped/ignored/overwritten.
As already mentioned above, if you did not have any VPN, and just the policy was marked "Traditional", there is no risk, AFAIK
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
On the second issue, yes, the title is incorrect, we are fixing that. Thanks for noticing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
On new Management installations, all policies are created with the Simplified VPN mode. There is a setting in Global Properties that enables a choice when creating new policies.
Older environments that were upgraded, can still have policies with the traditional mode.
Unfortunately, switching between modes is not simple and requires various subsequent changes. The VPN mode is set when creating the policy and changing the checkbox is disabled in the UI. It is not recommended to change the VPN mode on a policy that actually uses VPN communities.
The SK describes a way to bypass the limitation and modify the field using API. This should only be used on a policy that didn't actually use VPN and by mistake was created using traditional mode. We will make sure that disclaimers and clarifications are added to the SK.
The correct way to switch between a policy using traditional mode and simplified mode is to create a new policy with the correct mode.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @_Val_ and @Tomer_Noy for the information and your help with this!
One of our security gateways has more then 2000 rules, so creating a new policy will be quite cumbersome and we want to avoid that.
This firewall cluster does not have the VPN blade enabled, so I assume I could safely use this method.
Thanks again for your help!
Best regards,
Harry
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 16 | |
| 10 | |
| 10 | |
| 9 | |
| 7 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


