- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
Quantum SD-WAN Monitoring
Watch NowCheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Identity Awareness not matching users behind proxy
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Identity Awareness not matching users behind proxy
We configured security policy layers to detect users behind proxies:

Some systems use an explicit caching Squid proxy which is configured to send requests to the Check Point security gateway's proxy interface:
acl local-servers dst 10.0.0.0/8 100.64.0.0/10 172.16.0.0/12 192.168.0.0/16
always_direct allow local-servers
always_direct deny all
never_direct deny local-servers
never_direct allow all
cache_peer 100.127.254.1 parent 3128 0 no-query no-digest
Check Point security gateway is configured accordingly:

Users can only browse when we allow unauthenticated access from the Squid proxy's IP address. We temporarily changed the workstation to explicitly use the Check Point security gateway's proxy interface, navigated to https://fwcp1.lair.co.za/connect, authenticated and thereafter changed the proxy settings back to using Squid. Reviewing log entries shows the security gateway correctly identifying the IP of the workstation behind the Squid proxy but the IP is not associated with the authenticated user for that IP:

12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In my experience using caching proxies these days causes more issues than it solves. Website contents have become so dynamic that caching website contents brings you much less than in the early days of the internet with static websites.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We are based in South Africa and subsequently suffer from 160ms latency to Europe and 270ms latency to the USA. Using caching proxies when deploying Linux systems massively reduces deployment times so we wish to continue using them.
PS: User LAN and WiFi traffic wouldn't be channeled through the caching proxies, which in turn direct their requests via the security gateway's proxy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you enable XFF on the gateway as well?
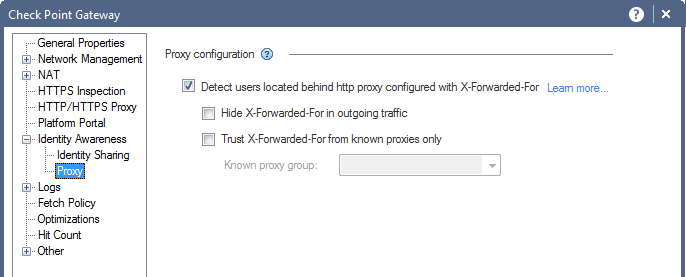
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is indeed:

network group object:
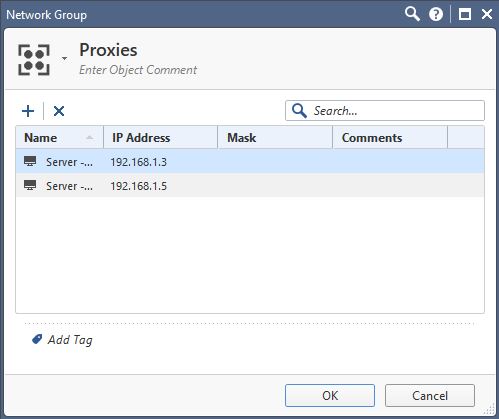
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In my right in understanding that the authentication is occurring only with Captive Portal and not with, say, Identity Collector or ADQuery?
I'd also check with a tcpdump the proxy is actually sending the XFF header.
I suspect a TAC case is probably in order also.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Correct, we run Samba AD and still need to write our own ADQuery 'equivalent' to feed authentication events to Identity Awareness using the Identity Web API. We were however pleasantly surprised to discover that captive portal and Kerberos authentication events survive policy installs, unlike AD Query Identity Awareness association events on classic Windows AD environments.
XFF is definitely working, as evident on the sample log entry in the original post where the record contains 'Proxied Source IP 192.168.5.12'.
I'll log a case with TAC, wanted to make sure I wasn't missing something first...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Wonder if you can hook up Samba to RADIUS Accounting?
I know you can hook up Samba to a RADIUS server for VPN authentication: VPN Single SignOn with Samba AD - SambaWiki
Not sure if that's easier than writing an IDA API connector, but another avenue to consider.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We actually already use FreeRADIUS to authenticate support staff to AD using security group memberships, to return relevant authorisation tokens.
Samba 4.7 and later supports Security Event logging natively (Setting up Audit Logging - SambaWiki), so we could drop our custom patches to send logon/logoff time summaries to the HR department. Legacy laws in South Africa require archaic sign in/out records for the government's worker compensation fund, with hefty penalties on non-compliance...
Anyway, debugging ADQuery a while back showed me how the Security Event logs are processed by SQL-esque queries, so I believe I can write a fairly simple event log Samba event log processor. Just need to investigate whether or not Web API Identity Awareness associations are cleared at policy install, the way ADQuery associations are. If not a boot script could tell the processor to search back for the last hour's events, the same way ADQuery does.
This is getting really off topic but I see great value in implementing WPA2-Enterprise (802.1x) for AD based WiFi authentication using RADIUS, which could then inform Identity Awareness when users connect to WiFi networks instead of replying on captive portal authentication every day.
Time, time, time...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We had another problem whereby application policies were not granting accessing to users when directing traffic via the security gateway proxy service, whilst they worked perfectly when sending requests directly. This most probably has to do with pre-defined applications being set with fixed port associations:

I'll log a feature request for HTTP_proxy and HTTPS_proxy service ports to track the security gateway's custom proxy port setting.
XFF unfortunately still doesn't work when we leave the Check Point security gateway on the default 8080 port assignment and update Squid to forward requests there.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can't you just add the custom services?
Or are you saying that doesn't appear to work?

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is locked down by the global policy on the MDS environment. I could clone the policy, change the proxy port and assign it to the relevant domain but it may be preferable to have the proxy port automatically track the associated security gateway's proxy port setting:

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Tracking the gateways explicit proxy port would definitely be an RFE.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 20 | |
| 15 | |
| 10 | |
| 8 | |
| 8 | |
| 6 | |
| 6 | |
| 6 | |
| 6 |
Trending Discussions
Upcoming Events
Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 19 Feb 2026 @ 03:00 PM (EST)
Americas Deep Dive: Check Point Management API Best PracticesTue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 19 Feb 2026 @ 03:00 PM (EST)
Americas Deep Dive: Check Point Management API Best PracticesTue 24 Feb 2026 @ 11:00 AM (EST)
Under The Hood: CloudGuard Network Security for Azure Virtual WANAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


