- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Explore New Wave of Web Based
DDoS Attacks and Mitigations
Four Ways to SASE
It's Here!
CPX 2025 Content
Remote Access VPN – User Experience
Help us with the Short-Term Roadmap
CheckMates Go:
What is UPPAK?
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: How to configure Check Point Security Gateway ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
How to configure Check Point Security Gateway as HTTP/HTTPS Proxy
Can Anybody PLease help me on this How to configure Check Point Security Gateway as HTTP/HTTPS Proxy
Thanks In advance
- Tags:
- httphttps proxy
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's it , now how can we solve this ?
60 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is documented here:
How to configure Check Point Security Gateway as HTTP/HTTPS Proxy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hello Peter,
from sk "...Transparent - All HTTP traffic on specified ports and interfaces is intercepted and sent to a proxy..."
what does it (sent to a proxy) mean?
proxy as a deamon or external box?
proxy as a deamon or external box?
thank You!
--
ak.
--
ak.
"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This means a process runs on the Check Point gateway that acts as a proxy. No 3rd party proxy would be required.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks peter this was a great help....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
and excellent work Sergei Shir and the SecureKnowledge Team!
they updated that sk110013!
"...and processed by the Proxy code in the Security Gateway..."
Thank You,
--
ak.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yes but i am not able to view it as m getting this pop up
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As a picture typically says more than a thousand words:
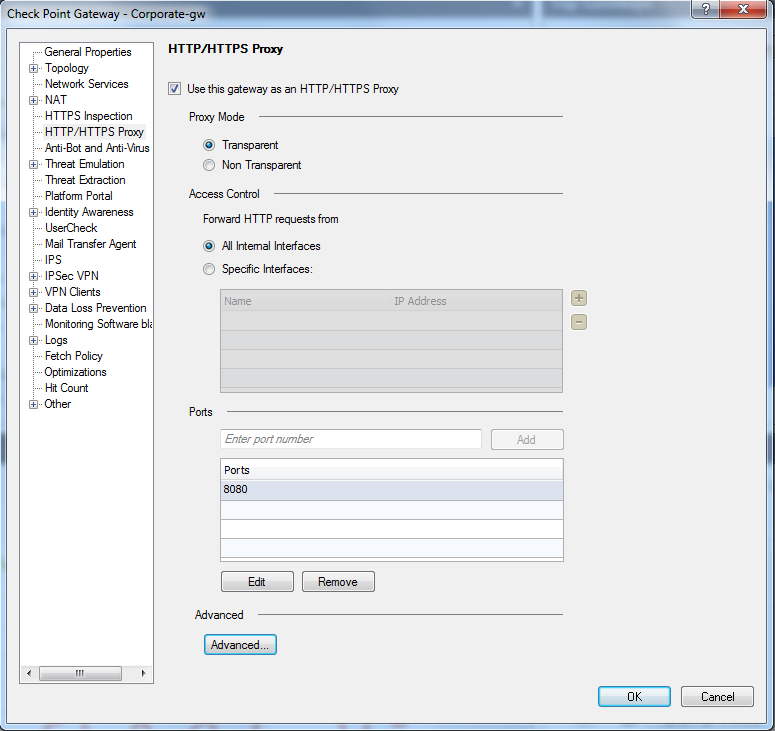
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Peter , do i also need to configure any outbound or inbound policy against this..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
By checking the box, implied rules are put in place. You need to create rules as you usually would (internal lan > internet > http+https > accept). Take into account that the gateway creates the outbound (proxied) connection from the gateway and requires a DNS to resolve against.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi peter
Bothering u again.. When creating a rule shud i select service as http 80, https 443 or http+https proxy 8080
SAT
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
http/https only should be sufficient.
The http-proxy service would allow access to other proxies, which I assume you don't want ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
what is the diffrence in transparent and non transparent proxy how they behave???
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In non-transparent mode, you must explicitly define the gateway as a proxy in the browser (directly or with a proxy.pac file stored on a different webserver). Transparent mode intercepts HTTP traffic on the specified ports and interfaces and sends it through the proxy without explicit configuration on the client side.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Dameon,
in non-transparent mode, the security gateway will break the http/https connection (meaning 2 connections, from client to security gateway, security gateway to http/https web server).
1. my understanding is, in order to intercept the web traffic, the security gateway should listen to tcp/8080. when i login to the gaia os cli expert level, i did not see a listening port at tcp/8080 (netstat -an) or is there other commands to view this?
2. using http/https proxy, the gateway show spawn off a httpd process to intercept web request at tcp/8080. so may i know what is the process name and how to view this process from gaia os cli expert level?
Thank You
TH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
netstat doesn't show it because it's not a process that is listening on that port.
The firewall kernel intercepts the traffic and "folds" it to fwd, which listens on a number of ports (not tcp/8080).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Dameon for the clarification.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If we can not test anything through netstat, how can we verify that the proxy works correctly? And how correctly to troubleshoot it?
In our case, we see logs, there are no deny actions, but the user does not have access to the Internet. On the test environment, I see this line:
[Expert@GW]# netstat | grep 8080
unix 2 [ ] DGRAM 8080 /tmp/pmsock
But in another environment I don't see it, and proxy doesn't work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The most obvious first step would be to telnet to the firewall on port 8080 and see if it answers.
If it doesn't answer, then it might be a configuration issue or it might be something else.
Worth engaging the TAC in any case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Dameon,
I have a quick question; I'd like to configure the Gateway as a proxy as stated on this thread. However, in my case, I am using public ip addresses for internal resources. The reason, is that in this enviromnent (Azure), customer has overlapping vNETS.
Is it possible to have Gateway work with public ip addresses for internal resources while using proxy mode? I can't get it to work in this scenario sadly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Whether the IP addresses are public or private shouldn't matter from our point of view.
Where you're going to have problems is if the IP addresses between public and private overlap in any way.
It's routing 101: how do I know which a.b.c.d address you're referring to?
This is generally solved with NAT rules that translate both the source and destination.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Dameon, yes we are handling the NAT rules as well. I've got it to work. Time to make this work in a multi Azure VNET as we have a limitation that we cannot peer them VNETS for internal BS, hence this approach with the public IPs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am a bit puzzled by the behavior of Transparent Proxy:

And yet, I could not verify that the proxy is working.
There are no log entries signifying its utilization and online proxy checkers do not indicate that the proxy is being used:

I have enabled the headers for explicit purpose of identifying that the proxy is working, but do not see any confirmations to that effect.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is App Control enabled in this situation?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The blade is enabled, but the rule governing egress traffic from this host/network is a basic net--to--any--allow--log:
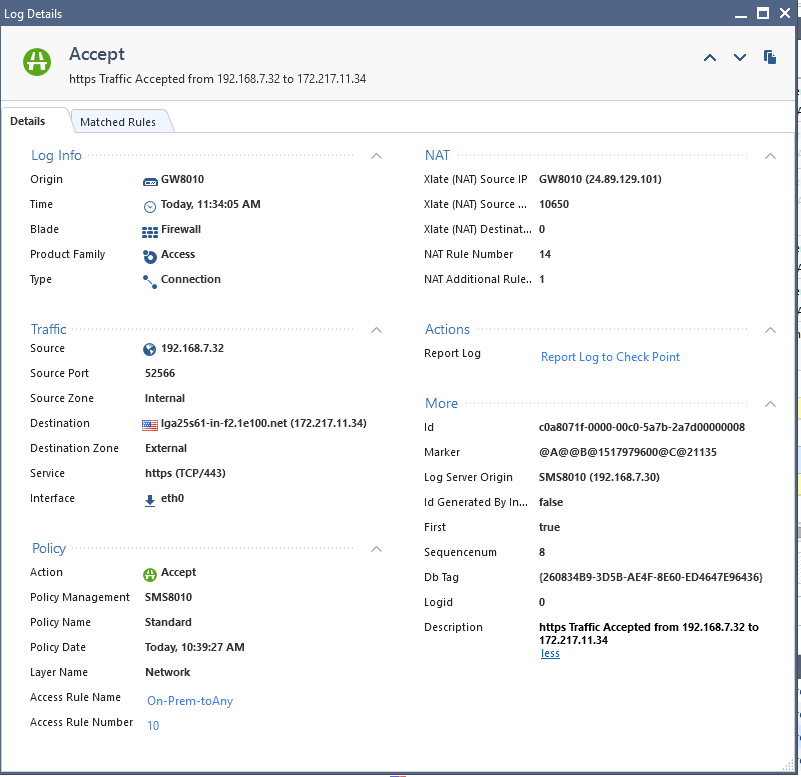

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You probably need to set the log to Detailed or Extended Log (versus log) which will activate App Control for that rule.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I do not want to activate app control for that rule: the proxy function is unrelated to App Control/URLF, I simply want to verify that it is, in fact, working.
According to the external proxy tests, no proxy headers are being attached, which is not an expected behavior.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The feature requires App Control/URLF to the best of my knowledge.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Let's suppose it does, for the sake of argument. It is licensed and enabled on that gateway:



- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Right, but it's not enabled for the rule that's being matched.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 21 | |
| 8 | |
| 6 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Tue 13 May 2025 @ 04:00 PM (CEST)
German Session: NIS2- Compliance: Effiziente Vorbereitung und UmsetungTue 13 May 2025 @ 04:00 PM (CEST)
Maestro Masters EMEA: Quantum Maestro Architectures and OptimizationTue 13 May 2025 @ 02:00 PM (EDT)
Maestro Masters Americas: Quantum Maestro Architectures and OptimizationWed 14 May 2025 @ 10:00 AM (CEST)
ATAM 360°: Elevate Your Cyber Security Strategy with Proactive services - EMEAWed 14 May 2025 @ 03:00 PM (CEST)
NIS2 Readiness: Assess, Secure, and Comply with ConfidenceWed 14 May 2025 @ 10:30 AM (BRT)
Transforme sua Segurança de Rede com Agilidade e EficiênciaTue 13 May 2025 @ 04:00 PM (CEST)
Maestro Masters EMEA: Quantum Maestro Architectures and OptimizationTue 13 May 2025 @ 02:00 PM (EDT)
Maestro Masters Americas: Quantum Maestro Architectures and OptimizationWed 14 May 2025 @ 10:00 AM (CEST)
ATAM 360°: Elevate Your Cyber Security Strategy with Proactive services - EMEAWed 14 May 2025 @ 03:00 PM (CEST)
NIS2 Readiness: Assess, Secure, and Comply with ConfidenceWed 14 May 2025 @ 10:30 AM (BRT)
Transforme sua Segurança de Rede com Agilidade e EficiênciaWed 14 May 2025 @ 05:00 PM (CEST)
ATAM 360°: Elevate Your Cybersecurity Strategy with Proactive services - AMERICASThu 15 May 2025 @ 09:00 AM (IDT)
PA In-Person CloudGuard Workshop (CGNS, WAF, & API Security)About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


