- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud Cloud Network Security CloudMates General CNAPP CloudGuard - WAF Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Open Garden In Action:
Find and Remediate Threats Everywhere!
New Appliance Announcements
and Faster Threat Prevention
Remote Access VPN – User Experience
Help us with the Short-Term Roadmap
It's Here!
CPX 2025 Content
CheckMates Go:
AI Agents
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Fixes for CVE-2022-0778 are ready ! Refer to sk178...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Fixes for CVE-2022-0778 are ready ! Refer to sk178411 - Check Point response to OpenSSL CVE-2022-077
Fixes for CVE-2022-0778 are ready ! Refer to sk178411 - Check Point response to OpenSSL CVE-2022-0778.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes: you need to upgrade to minimum R80.20.35 with build 992002639 to be secure. All newer versions also include the fix (newer software package)
What about the 1400 series that are still running R77.20.87. Are these vulnerable? See the SK footnote:
- This issue does not apply to SMB appliances running Gaia Embedded R77.20.xx.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
20 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have updated my 1550 already 8).
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
...and found a serious bug in APPI updates making APCL work no more...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Guys
we didn't see any bug in APPI. in fact there was no change in this region, so i'll be surprise if there is a bug.
As for why OpenSSL in not 1.1.1n. the issue was fixed within the same OpenSSL version.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I resolved the bug. Not a fault of the fixed firmware...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
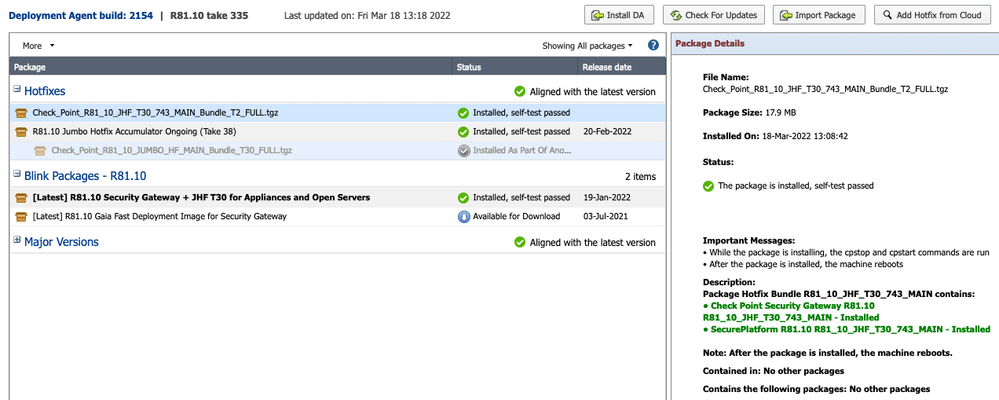
Very strange: For R80.10, HF is available based on JT_30 as Check_Point_R81_10_JHF_T30_743_MAIN_Bundle_T2_FULL.tar.
But on R81.10 JT_38, verify as well as install work perfectly:
Afterwards:
#cpopenssl versi
OpenSSL 1.1.1n 15 Mar 2022
But as only openssl-1.1.1n-1.cp996000002.....rpm gets installed that seems to be not an issue - but can CP confirm that this is supported ?
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The wording of the SK is specific, it doesn't say T30 and above.
If you need this for T38 I would contact TAC and request it be ported for official support or await the future JHF which includes it.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As only cpopenssl is replaced, it should work with R81.10 JT_38 as well. Submitted the question as feedback in sk178411!
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @G_W_Albrecht
You are right 🙂
The HF for R81.10 T30 is also valid for R81.10 T38
sk178411 is updated accordingly, refer the note in 'Solution' section.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, i just had received the reply from R&D !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R&D just released this statement:
"No changes were made to the cpopenssl module between General Availability (GA) Takes and Ongoing Takes of the Jumbo Hotfix Accumulators. Accordingly, this Hotfix also applies to Ongoing Takes."
sk178411 has been edited to reflect this.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
does anyone have information how dangerouis this issue really is?
who has seen Check Point gateways freezing by this issue?
does it affect every Check Point installation when it is reachable via HTTPS from the outside/inside world?
or is it sufficient to surf a special crafted website and this will freeze the CP gateway?
in combination with HTTPS inspection, does it also strike or even more?
since special elicpic curve ciphers are causing this ... does it make sense to disable them?
Did Check Point already release a public advisory email to inform costumers and partners?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Thomas,
AFAIK, we haven't yet seen the actual exploitation, but that doesn't mean that it hasn't or won't happen. By the description of the bug, the vulnerability is while reading the ECDSA extensions. Therefore, disabling them shouldn't have an effect as we're trying to understand what to use and that's where the exploitation takes place.
How dangerous? It is not a breach, but rather a Denial of Service, and this would happen when the gateway reads a client or server certificate (e.g. HTTPS Inspection reaching a web site with a malicious certificate).
As this is a public vulnerability with published exploits, Check Point highly recommends installing security fixes that we release.
HTH,
Ethan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ongoing Jumbo R80.40 is already available including the HF:
Check_Point_R80_40_JUMBO_HF_Bundle_T156_sk165456_FULL.tgz
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R81.10 Jumbo HotFix - Ongoing Take 44 (22 March 2022) is already available including the HF:
Check_Point_R81_10_JUMBO_HF_MAIN_Bundle_T44_FULL.tgz
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jumbo Hotfix Accumulator for R80.20 starting from Take 208 is already available including the HF.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
New IPS Protections Package No. 634222051 & 635222051 : OpenSSL Denial of Service
(CVE‑2022‑0778)
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry for bringing this old thread up. But I'm somewhat confused when it comes to Gaia Embedded / SMB. sk178411 links directly to R80.20.35 with buildnr: https://supportcenter.checkpoint.com/supportcenter/portal?action=portlets.DCFileAction&eventSubmit_d...
This build is higher than the "official" R80.30.35 listed in:
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
I suppose this means that if you are running 1500, 1600 or 1800 series on R80.20.35 or lower, you need to upgrade to minimum R80.20.35 with buildnr: 992002639 to be secure.
But what about those who are running R80.20.40, R80.20.50 or R81.10.00? I can't see anything in the R80.20.40, R80.20.50 or the R81.10.00 changelogs, or anything specific within sk178411 saying these versions are secure. I would think they all have the fix included as it was originally released as a new revision/build of R80.20.35, but some kind of confirmation on the topic would be nice.
What about the 1400 series that are still running R77.20.87. Are these vulnerable?
Certifications: CCSA, CCSE, CCSM, CCSM ELITE, CCTA, CCTE, CCVS, CCME
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes: you need to upgrade to minimum R80.20.35 with build 992002639 to be secure. All newer versions also include the fix (newer software package)
What about the 1400 series that are still running R77.20.87. Are these vulnerable? See the SK footnote:
- This issue does not apply to SMB appliances running Gaia Embedded R77.20.xx.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@G_W_Albrecht
I'm not sure how I managed to miss the part regarding R77.20. My bad. I just verified this by running "openssl version" and it looks like R80.20.40+ contains the updated OpenSSL version.
Thanks for the quick reply!
Certifications: CCSA, CCSE, CCSM, CCSM ELITE, CCTA, CCTE, CCVS, CCME
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Correct - that made it very easy to fix in future versions as openssl is a complete package that can be just exchanged to a fixed version.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 6 | |
| 6 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 3 | |
| 2 | |
| 2 |
Upcoming Events
Wed 16 Jul 2025 @ 10:00 AM (CEST)
Master GCP Security with the Cloud Architects Series (Multilingual Webinar)Wed 16 Jul 2025 @ 04:00 PM (CEST)
Operationalizing Threat Intelligence, Part II: Threat Hunting & Incident ResponseTue 22 Jul 2025 @ 10:00 AM (CEST)
Cyber Security Training in the Era of AI Threats: Managed SmartAwareness Explained - EMEATue 22 Jul 2025 @ 05:00 PM (CEST)
Cyber Security Training in the Era of AI Threats: Managed SmartAwareness Explained - AMERThu 31 Jul 2025 @ 10:00 AM (CEST)
CloudGuard Network Security for Nutanix - Full Deployment with Tenant & Transit VPC - EMEA/APACWed 16 Jul 2025 @ 04:00 PM (CEST)
Operationalizing Threat Intelligence, Part II: Threat Hunting & Incident ResponseTue 22 Jul 2025 @ 10:00 AM (CEST)
Cyber Security Training in the Era of AI Threats: Managed SmartAwareness Explained - EMEATue 22 Jul 2025 @ 05:00 PM (CEST)
Cyber Security Training in the Era of AI Threats: Managed SmartAwareness Explained - AMERThu 31 Jul 2025 @ 10:00 AM (CEST)
CloudGuard Network Security for Nutanix - Full Deployment with Tenant & Transit VPC - EMEA/APACThu 31 Jul 2025 @ 05:00 PM (CEST)
CloudGuard Network Security for Nutanix - Full Deployment with Tenant & Transit VPC - AMER/EMEAAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter