- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Dropped or not
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dropped or not
Hello,
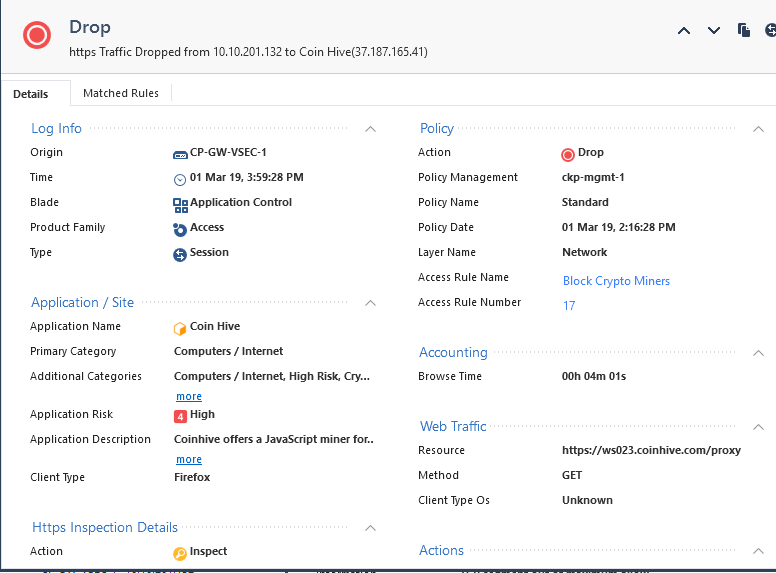
I have come across a strange situation where my packets are both Accepted and Dropped at the same time. Can anyone help me determine what is the real outcome ?
Firewall Rule:
![]()
*Picture was unclear.Updated to clearly see policy has Drop*:

Output of the log:

Description of the event:
https Traffic Accepted from <USER NAME> (<username>)(<internal_ip>) to 2.17.117.112 due to TCP segment out of maximum allowed sequence. Packet dropped.
Knowing that i found the packet that is simultaneously both accepted and dropped - I will just leave this here for reference:
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What i can see is that your Access Rule "Block Crypto Miners" does accept the packet, then it is dropped by IPS Sanity checks ! Maybe sk122072: 'TCP out of Sequence' logs in SmartView Tracker can help ?
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My mistake - the rule is configured to DROP but this was not clear in the first picture. I corrected.
Yet the logs say Rule 18, descriptions says Accepted. Protection says Dropped.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
It is accepted by policy but it is dropped by IPS. Are you getting this message continuously or for specific time. One of the reason is high memory usage as well.
SK66576 & SK114529 will be helpful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why is it accepted by the policy when the action on the rule is Drop?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The main thing is that it is dropped by IPS - i would start from there ...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My issue is that the firewall log for rule 18 says "Accepted"
I can agree that apps can only be detected and classified ONLY after allowing the connection to be initiated.
Does this mean that the unified policy is misleading? Yes
Does this mean that this traffic is passed through the next firewall rules? I don't know
My customer is asking me to advise on how to build the ruleset considering that his rules are "avoided". I would agree that if there is an explicit drop, i would much appreciate not seeing any kind of log saying it was allowed as this creates confusion. Especially If the Firewall is claiming my rule 18 matched this traffic -
The only supposition i have is that because it's somehow fragmented it cannot be inspected... but still it is accepted and on a rule with Coinhive.
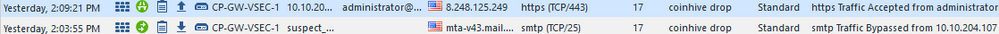
The other perculiar thing is that on the same rule i have both this example https traffic and SMTP traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would involve TAC - although i would suggest that an Accept here just means that this rule did not match, as then it would drop the packet instead. The message is from IPS, so that is the key here !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Is this for any specific traffic?
Please run zdebug and fw monitor for more troubleshooting
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Exactly the same suggestion was given by TAC. After reading the SKs i can see that setting this protection to Detect makes it be bypassed by other IPS protections.
However my issue is with the log stating Accept. Is this passed to the next rule or simply allowed?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1. I am updating with more information. I have tested this signature on different setup, everything works. This means that the app "Coinhive" itself has no issue.
2. The rule on this particular SMS/vSEC Gateway has been deleted, policy installed. Re-created, policy installed again. The result is similar:
- Traffic is dropped as intended: ;[cpu_3];[fw4_0];fw_log_drop_ex: Packet proto=6 10.10.202.44:50534 -> 86.105.182.5:443 dropped by fw_send_log_drop Reason: Rulebase drop - on layer "Network" rule 18;
- There is no log of this happening. Looked historically and things went bad on the 3rd of March when i have the last Application Control log working for this:
- The bogus logs for SMTP Bypass and Accepted HTTPS dropped by Inspection were there all along.
- Example (rule numbe changes as i moved it around):
- For the SMTP bypass support claims it is sourced by sk120964. However i cannot get my head around why would this SMTP bypass log trail around my rule 18 every single time i create or delete it. Why doesn't it pop on rule 10 or 11 or 50?
- For HTTPS with Accept message and Dropped Description there is no explanation yet. I have checked and inspection settings according to SK66576 & SK114529 , that have been brought into discussion earlier are set to Drop and Log.
- There is no proper Inspection Setting Log and regarding this or i don;t yet know where i would see inspection setting logs, as they seem more part of the firewall rather than IPS starting R80.
Unrelated Note: The new interface for Check Mates makes editing a complicated mess. It was much better before. Hope it was worth it. I just noticed while trying to make this post. You can't even paste pictures anymore. Let alone "quote" text.
Makes me think it now looks awfully aligned with the new Support Interface. Not everything is supposed to be a feed, sometimes i would like to be able to track my cases by just scrolling down, not having replies in my SR's arranged by "relevance" and "likes". Somebody actually hired some PR/Marketing guys to keep shifting interfaces around?!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
great post I like it a lot ! 🙂
Jerry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There should be a "quote" button on the right side of the toolbar. I'll see if we can enable pasting photos into the editor as, I agree, that is quite useful 🙂
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 17 | |
| 12 | |
| 10 | |
| 10 | |
| 5 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter